Tales from the Crypter: Thwarting Malware Obfuscation with Threat Emulation
Summary
Malware writers employ a variety of specialized obfuscation techniques to render known malware invisible to existing antivirus defenses. These techniques, known as “crypting,” enable malware writers to create unknown variants of proven, highly effective malware that evade AV detection and extend the reach of existing bot infrastructure.
Check Point Threat Emulation recently demonstrated that not all defenses are so easily evaded when it detected and blocked a crypted and previously unknown malware variant designed to deliver the DarkComet remote administration tool (RAT). Although this sample was able to evade most AV solutions, Threat Emulation was able to reveal it and additional investigation by our research team traced it to a malware campaign that has been detected at work in Europe and Latin America.
In addition to detecting and blocking this dangerous malware through the ThreatCloud network, this catch by Threat Emulation highlights the inner workings of the family of advanced attacks that are changing both the threat landscape, and the range of solutions that security managers need in order to defend their networks and their data.
Detailed Analysis
Intercepting a suspicious attachment
On December 31, 2013, Check Point ThreatCloud received an alert triggered by a Threat Emulation detection in a customer network. At the time of detection, the malware sample was unknown to the VirusTotal community and was able to pass numerous different antivirus engines with no detections. (VirusTotal is a Google-owned service that analyzes suspicious files and URLs and maintains a malware database that is shared back to the research community.)
The malware was sent by email from a fake Gmail address with the subject “PROFORMA INVOICE”, appearing to present a previously discussed possible purchase deal from a seller. The email included an attachment named ‘PROFORMA_INVOICE.rar’, which is a valid extractable RAR archive containing an executable file. Unlike attacks which exploit an OS or application vulnerability, this malware simply needs the end-user to run the executable once extracted from the RAR file.
Threat Emulation intercepted the attachment, extracted its contents, and attempted to open it in a controlled emulation environment, a process also referred to as ‘malware sandboxing.’ During emulation, it was detected that the file exhibited multiple suspicious activities when executed, including creating additional processes, writing suspicious files, and registering for system-wide notifications.
Based on these emulation results, this sample was forwarded for further analysis with Check Point Malware Research Group, which extracted the malicious payload and undertook additional analysis.
Analysis revealed that the executable contained an obfuscated version of the DarkComet RAT. DarkComet is a freely available remote administration tool (RAT), with useful abilities such as keylogging, screen captures, file transfers and more. When used maliciously, DarkComet can essentially turn any computer into a fully-featured bot, and this is, in fact, the primary notorious use for this software, as we often see evidence of DarkComet malware campaigns.
In its plain, non-obfuscated form DarkComet is detected by the majority of AV products.
‘Crypter’ services make a business of antivirus evasion
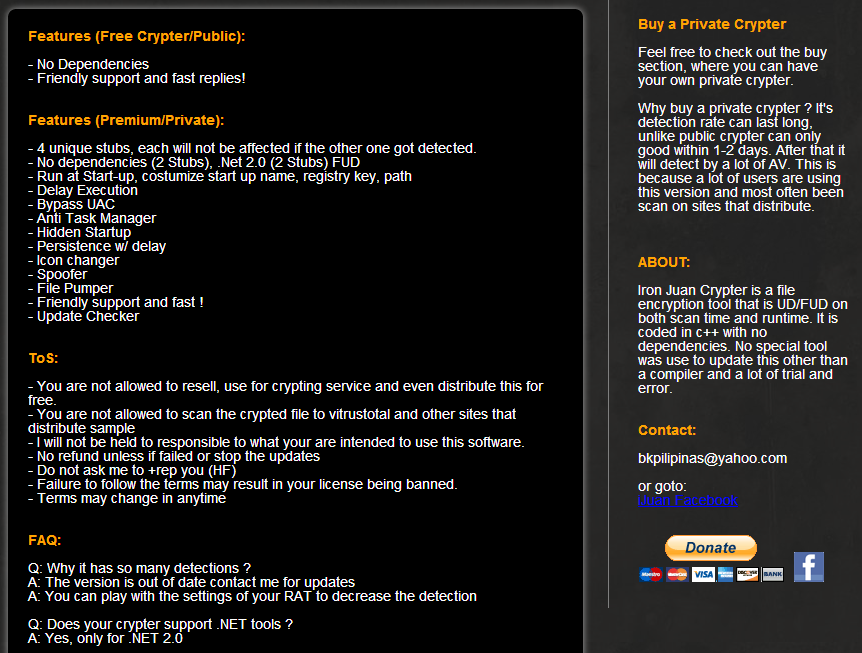
In order to bypass detection by AV software, modern malware authors maintain and use specialized obfuscation tools called “crypters.” Technically classified as a Portable Executable (PE) Packer, and not to be confused with encrypting ransomware such as Cryptolocker, crypters like this sample disguise executables through the use of various encryption and encoding schemes, cleverly combined and recombined, often more than once. To verify that their variants are undetected, malware authors avoid online AV scanning platforms such as VirusTotal and others which share samples with AV vendors, and instead utilize ‘private’ services such as razorscanner, vscan (aka NoVirusThanks) and chk4me. PE Packers and other ‘crypters’ are classified by hacker communities as UD (UnDetectable) or FUD (Fully UnDetectable) according to their success at evading antivirus detection.
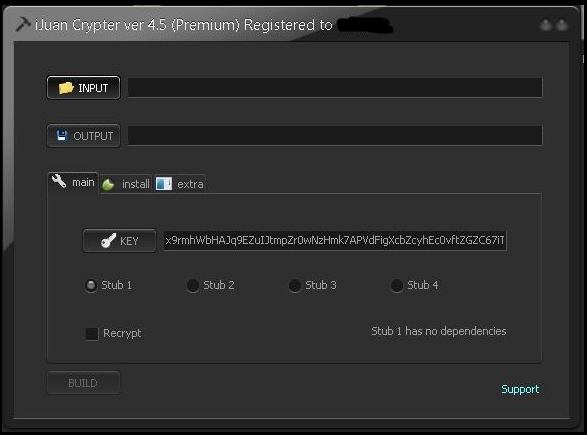
In the case of our detected sample, an embedded PDB string gave away that it was by the iJuan Crypter, which is available online both as a free (UD) version as well as a premium (FUD) purchase option. The fact that even malware writers are experimenting with the ‘freemium’ pricing model offers yet another example of the sophistication of the underground malware economy.
It may be surprising to some to read how the crypter author (nicknamed ‘Iron Juan’ but otherwise anonymous) boasts about the ability of his ‘crypting’ software to evade antivirus software, in obvious disregard for the potentially criminal intent of the users and buyers.
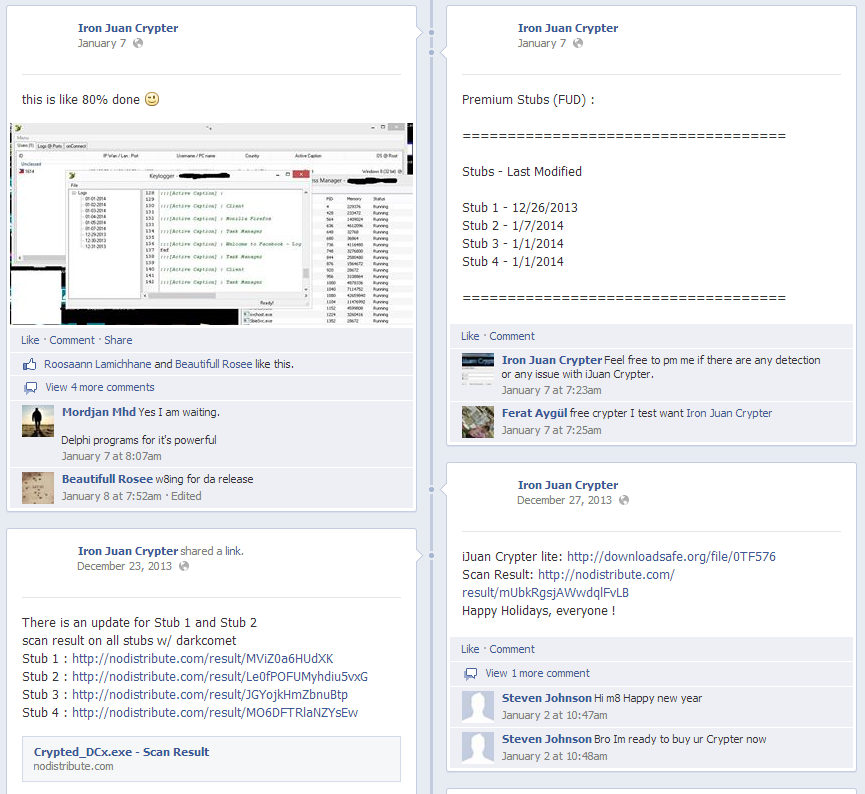
The ‘Iron Juan Crypter’ even has a Facebook page and YouTube channel, where the author describes and demonstrates his development progress across new versions, showing current detections to the enthusiastic and appreciative audience. (As with most sites in the underground malware community, average users are advised to exercise extreme caution when visiting any sites dedicated to buying, selling, trading and developing malware.)
Uncovering the campaign
Once executed, the malware attempts to communicate with its hard-coded command and control (C&C) server at: roland1926.no-ip.biz:1604
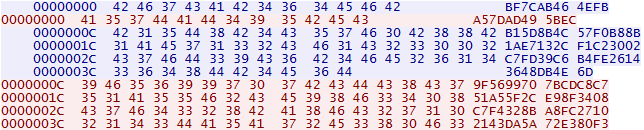
The following is sample traffic generated in our lab:
Both the port and the communication pattern are highly indicative of DarkComet traffic, encrypted via a custom password RC4 algorithm, submitting victim data to campaign operators.
Less than a week after the initial detection, we received a second Threat Emulation alert for a similar detection in a different country. Performing a similar analysis has revealed it to be a differently obfuscated version of the same DarkComet payload and communicating to the same C&C server, which together indicate that these two distinct detections – one in Europe and the other in Latin America – are in fact part of the same campaign.
Protecting your organization from this type of attack
All Organizations
In order to reduce the chance of infection from this kind of malware, organizations should educate users not to open unexpected or suspicious attachments from external email addresses
Check Point Customers
Customers who have enabled the Antivirus and Anti-Bot Blades on their Check Point gateways automatically received updated detections for these newly detected variants through ThreatCloud. For additional protection against previously undetected malware, customers should consider enabling Threat Emulation as a public or private cloud service.
Non-Check Point Customers
Non-Check Point customers should monitor for outbound communication to roland1926.no-ip.biz:1604 and take action to remediate infected clients.
Appendix
Hashes for detected malware are:
MD5:
fc2576a2883de7ed3f30b1fcbf937e38
b61b771c4b80c9ba8d6bba4d908fe9e5
f88093bea5abd4e8d859cf179d6e684e
SHA1:
MD5:
d0afdbefa942b0f98c6a786afabedfc1cd5fedf8
90ac55fd5cb55a664b49622d8aedf64ad69c522d
7bc49c4a1801b5d04b54c63638534df7ddf13da1
Click the download for full article (Download PDF)