Security Disclosure: Google’s iOS Gmail App Potential Target for Threat Actors
As part of our ongoing research into Apple’s iOS environment, we analyze mobile apps from various perspectives.
During a routine analysis of the Gmail  iOS app we unexpectedly came across a vulnerability which enables a threat actor that is performing a Man-in-the-Middle attack to view, and even modify, encrypted communications.
iOS app we unexpectedly came across a vulnerability which enables a threat actor that is performing a Man-in-the-Middle attack to view, and even modify, encrypted communications.
Secure Mobile Communications 101
In general, secure communications rely on encryption, i.e. SSL, between an app and the back-end server to prevent prying eyes from seeing into content during transmit. The problem with using just SSL is that a threat actor can impersonate the back-end server by creating a spoofed SSL certificate. The certificate is essentially a validation that the server is who it claims to be (in this specific scenario, that back-end server is Google’s Gmail).
By impersonating the legitimate server (i.e. performing a Man-in-the-Middle) through the usage of a spoofed SSL certificate, the threat actor can open up the encryption, view, and even modify, all communications in plain-text – including passwords, emails, and chats.
In particular, in iOS, a threat actor can install a configuration profile which contains the root Certificate Authority (CA). The configuration profile is an extremely sensitive iOS file which allows to re-define system functionality parameters such as device, mobile carrier and network settings. The root CA is what enables the threat actor to create spoofed certificates of legitimate services. It is important to note that the configuration profile is very simple to install. More so, many legitimate enterprise policies demand its installation.
To overcome this threat in mobile, the concept of certificate pinning was introduced. With certificate pinning, the app developer codes the intended server certificate within the app. So if communication is re-routed via the threat actor’s server, the mobile app will recognize the inconsistency between the back-end server certificate as coded within the app, and the certificate returned from the so-called server.
The Vulnerability: Gmail’s iOS App Does Not Perform Certificate Pinning
Unexpectedly, we found that the Gmail iOS app does not perform certificate pinning. As a result a threat actor can perform a MitM attack and open up the Gmail encrypted communications. The victim does not receive any indication of suspicious activity.
We were quite surprised by this finding because Google had implemented certificate pinning for their Android Gmail app. Clearly, not implementing this for iOS was an oversight by Google.
Lacoon’s research team informed Google about this problem on February 24. Google had recognized this flaw and validated it. We were told that they were going to fix this issue though to date, this vulnerability still exists.
What does a MitM attack for iOS apps that implement SSL encryption look like?
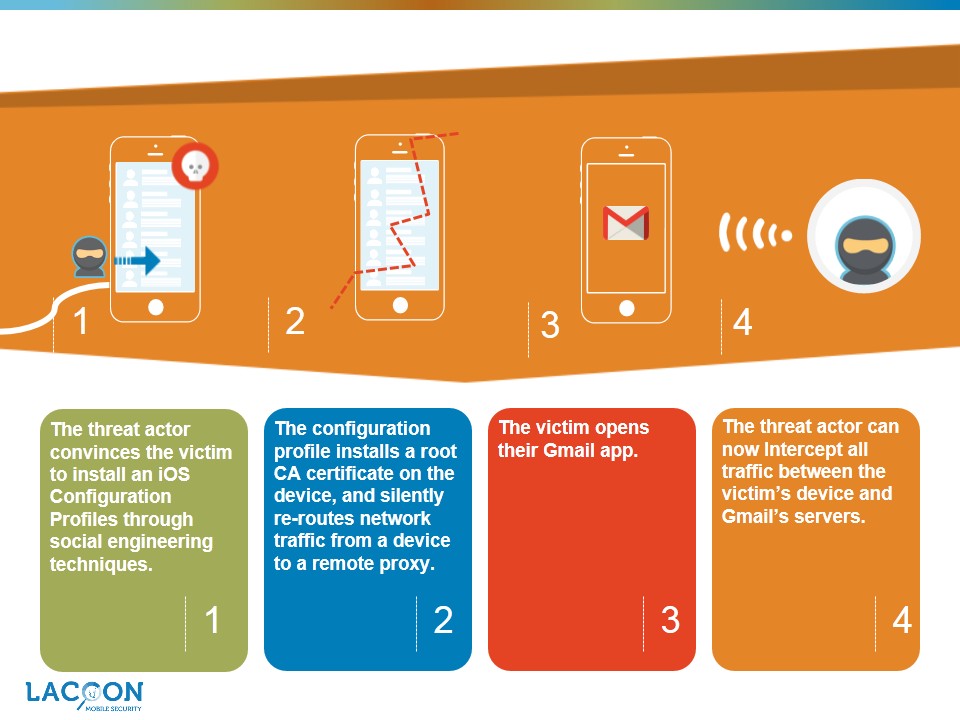
The threat actor performs the following steps:
- Tricks victim into installing a configuration profile containing the root certificate and the details of the server to reroute the traffic to.
(Note: to do this, a threat actor can use a variety of social engineering methods such as sending an email, purportedly from the IT department, requesting to install the configuration profile.) - Reroutes victim’s traffic through the server under the threat actor’s control, defined by the malicious configuration profile.
- Creates spoofed certificates which are identified as valid by the victim’s device.
- Intercepts all traffic between the attacked device and intended server.Diagram of the attack:
Were there similar vulnerabilities in other apps in the past?
Yes. Not using certificate pinning is a great concern when it comes to targeted threats. In fact, this issue has been raised before by previous researchers. For example, following Facebook’s $19B acquisition of WhatsApp, researchers found that WhatsApp had never used certificate pinning.
How to mitigate these types of vulnerabilities?
First and foremost, it’s up for the mobile app developer to implement certificate pinning. With enough public concern, let’s hope that app developers start listening to their customers and placing the necessary security measures.
In the meantime, enterprises dealing with corporate apps that do not implement certificate pinning should follow these best practices:
- Check the configuration profiles of devices in your enterprise to ensure that they do not include root certificates.
- Ensure that employees use a VPN or any other secure channel when connecting to enterprise resources
- Perform on-device and network analysis to detect MitM attempts









