Mobile Security Weekly – Android Threats Stack Up
 On the heels of BlackHat USA, perhaps it’s hardly surprising that this week has been especially full of malware. Much like the demonstrations and presentations at Blackhat, this week’s stories highlight attackers’ technical prowess as well as effectiveness and practicality.
On the heels of BlackHat USA, perhaps it’s hardly surprising that this week has been especially full of malware. Much like the demonstrations and presentations at Blackhat, this week’s stories highlight attackers’ technical prowess as well as effectiveness and practicality.
- Researchers in Russia have discovered that half a million devices have been infected with a form of banking malware.
541,000 smartphones running on Android in Russia, Europe and the US are already infected with malware that grants the perpetrators full access to people’s mobile devices.A recurring trend, this attack is based on a large scale SMS campaign, which bombards victims with fake messages until they break and download a malicious file. It’s a well known fact that most Russian banks use SMS messages to communicate confidential details to users. This has quickly become a target for many types of malware. This specific attack can relay a victim’s messages back to a remote server as well as access most other types of data on the device. http://www.bloomberg.com/news/2014-08-05/a-peek-at-a-program-that-lets-hackers-steal-anything-from-your-smartphone.html
Why is this Significant?
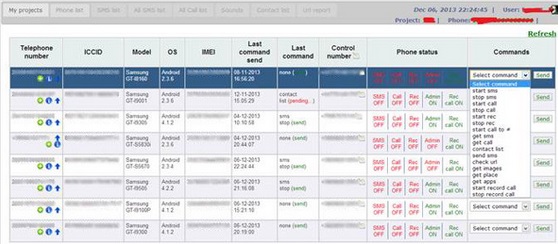
- Besides the obvious severity of the attack, it’s worth noting that this malware has also taken an impressive step forward in usability. Attacking mobile devices has never been easier – as demonstrated in the below screenshot:
The malware is controlled by a very comfortable program that is even equipped with a drop-down menu next to each victim’s phone number. The options for violating the smartphone owner’s privacy include “get images,” “get place” and “start record call.”
- Android mRAT impersonates Kaspersky Mobile Security
An advanced mRAT (Mobile Remote Access Trojan) attack impersonating well-known AV vendor Kaspersky Lab, is actively targeting Polish Android users.Similar to the previous item, the attack is based on a fake email sporting the firm’s logo and warning users that a “..virus designed to steal SMS codes (mTANs) used to authorize bank transfers has been detected on their devices…”.The scam goes on to provide the victim with a free virus app that has been commissioned by the users’ bank: “To prevent theft of cash from your account, please promptly install Kaspersky Mobile Security Antivirus on your mobile device..”Sadly, the attached file – Kaspersky_Mobile_Security.apk – is not a security solution, but a variant of the Android SandroRAT. This version of the malware can steal the users’ contact list, SMS messages, browser history, bookmarks, and GPS location. It can also intercept and relay incoming calls and text messages and room audio.http://www.securityweek.com/mobile-users-targeted-sandrorat-posing-security-softwareWhy is this Significant?
It’s interesting to see how attackers are taking older strains of malware and updating them. In this case the mRAT can now both access encrypted Whatsapp chats (unless Whatsapp has been updated) and obtain the unique encryption key using the Google email account of the device, something that the original version wasn’t able to do.
We predict that it won’t be long before this attack spreads out from Poland and starts targeting users worldwide.
- Researchers discover that some banking apps designed with Apache Cordova suffer from serious security issues.
It has been discovered that attackers can steal login credentials and other sensitive data from 1 in 10 Android banking apps, and about six per cent of all Android apps. Users should avoid using the vulnerable apps, which were built using Apache Cordova up to version 3.5.0, until they have been updated.The problem is in Cordova, a toolkit for crafting mobile software using HTML, CSS and JavaScript. A cross-application scripting (CAS) hole allows threat actors to remotely run malicious JavaScript code in the context of a vulnerable Cordova-built app. Apparently, it’s possible to exploit other bugs within Cordova to then extract additional sensitive information, such as login cookies.
http://www.theregister.co.uk/2014/08/06/android_vuln_banking_app_riskWhy is this Significant?
Left untreated, this vulnerability can be abused in a number of different ways to steal online bank account credentials that would enable criminals to withdraw or transfer funds. It’s important to note that in a similar fashion to Heartbleed – this is neither the users nor the app developers fault. An inherent security problem within an app-developing kit is to blame. Sometimes, it’s almost impossible to predict where a security issue will sprout from.









