
Plugging the Security Hole in a WordPress Plug-In
Check Point researcher, Roi Paz recently discovered a critical vulnerability that would have enabled attackers to steal personal and financial data from thousands of websites and their visitors via the LiveSupporti WordPress plug-in. After being alerted to the situation, LiveSupporti plugged the security hole.
LiveSupporti is a software service that enables website visitors to engage in a live chat with representatives (or “agents”) of the site. The cloud-based service promises to increase sales by helping to convert site visitors into customers through text-based live chat. Adding LiveSupporti to a website is just a matter of adding a snippet of code to the website’s HTML.
LiveSupporti offers a WordPress plug-in, which enables owners of WordPress blogs and sites to easily add LiveSupporti’s live chat support. Any site visitor can initiate this text-based chat with the site’s owner, operator, or other agent. LiveSupporti’s website also provides a history of previous chats to all users of its WordPress plug-in. The free WordPress plug-in is currently in version 1.0.0 and has been downloaded more than 26,000 times.
Where the Plug-In Was Vulnerable
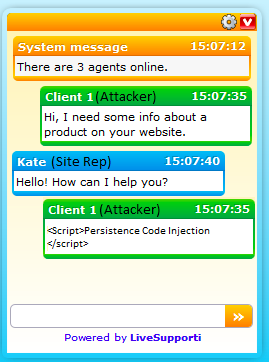 Check Point security researchers have often taken the lead in identifying and ‘cracking the code’ on emerging security threats, such as the recent DirCrypt Ransomware exploit.
Check Point security researchers have often taken the lead in identifying and ‘cracking the code’ on emerging security threats, such as the recent DirCrypt Ransomware exploit.
In this case, Check Point researchers discovered a significant Persistent Cross Site Scripting vulnerability in the LiveSupporti website chat history service. The vulnerability could have allowed an attacker to send a site agent a crafted string via text chat, which upon accessing the site’s chat history could be executed. This may have resulted in account hijacking by changing the account details or by other Man-in-the-Browser (MitB) attack methods, such as loading Browser Exploitation Framework (BeEF) testing tools.
By taking control of a WordPress LiveSupporti admin account, an attacker could have stolen personal and financial data from a website’s owner or operator. Thousands of websites around the globe would have been affected.
Check Point reported the security hole to LiveSupporti. LiveSupporti and WordPress confirmed the vulnerability and fixed it (CVE-2014-6063).









