
What Does Fast Threat Emulation Mean?
Your IT department has probably deployed multiple kinds of defenses to protect your network from malware. We are all familiar with antivirus and intrusion prevention programs. They protect us from known threats and are our first line of protection defense. Known threats are characterized and stored in a threat database. The more we know, the more we can protect against.
So how does a threat become known? It turns out there are a few ways.
- We hear things: From sources wide and far we get reports on new threats. As we hear about them, we characterize them and put them into our threat database.
- We see things: Every file we see we test in what is called threat emulation. Emulation allows us to simulate a file to see how it reacts. If it exhibits malware characteristics, we create a signature and update our database. Emulation is all about being accurate and, most importantly, fast.
- We share things: As soon as we identify a new threat, we send out protection updates, first and foremost, protecting our clients. The faster we share, the faster our clients are protected.
Detecting unknown malware is very important and Check Point has the industry’s best catch rate. See for yourself by reading our Unknown 300 test report. Check Point also has the industry’s fastest and most efficient threat emulation. For more on that, see our Zero Second test report. We can save you a little time by sharing the highlights.
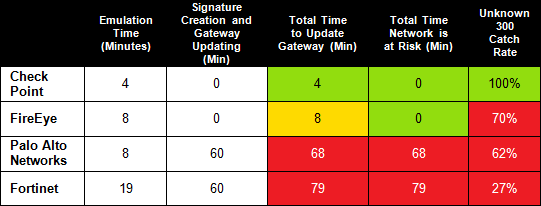
Table 1 – Zero Second Emulation and Update Time Results
Our role is to make IT’s job easier where security is concerned. Fast and accurate threat detection is a must and we are proud to be the fastest and most accurate.









