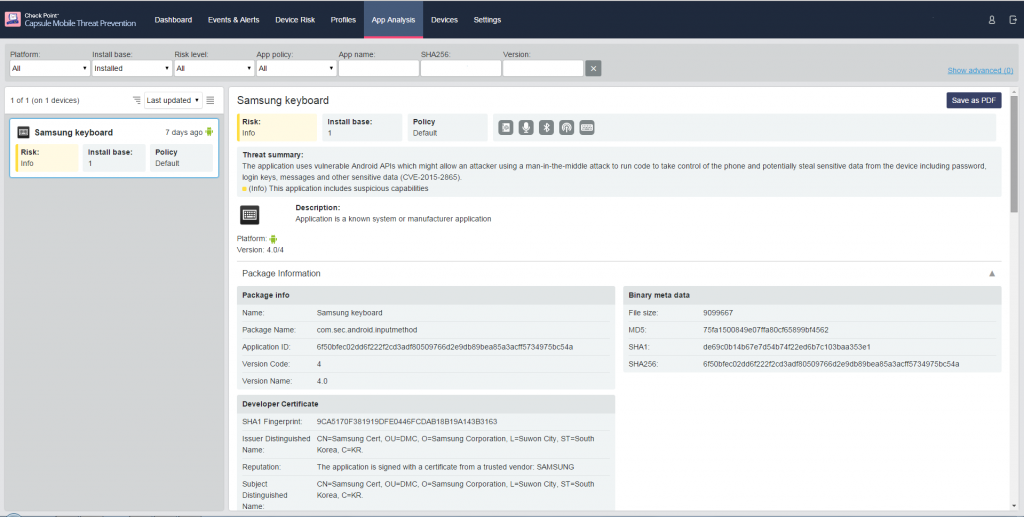
SwiftKey Leaves Samsung Devices Susceptible to Cybercrime
A vulnerability in the SwiftKey virtual keyboard pre-installed on the Samsung Galaxy S4 Mini, S4, S5 and S6 could let hackers take complete control of these devices, researchers discovered recently. This is because the keyboard, which is designed to accept and install language updates via HTTP (and not HTTPS) fails to properly validate the file, which could be replaced with a malicious payload using a man-in-the-middle (MitM) attack. Once on the device, the keyboard will execute the file without user interaction, allowing it to infect the device and enabling a hacker to take control.
The vulnerability (CVE-2015-2765) is the latest example of how hackers can use a combination of flaws to get into mobile devices and to steal information. In this case, hackers take advantage of three key weaknesses on Android devices:
- Android .Zip file extraction traversal vulnerabilities
- SwiftKey’s method of downloading updates using an unencrypted channel
- Samsung (and potentially other manufacturers) embedding of SwiftKey as a system user on the device.
Using this combination, a hacker capable of executing a MitM attack serves the malicious file when the SwiftKey application asks for an update. The impact on the user is a complete takeover of the device as a system (privileged) user, not just leakage of any information being typed using SwiftKey.
Therefore, regardless of the type of secure container on the device and whether or not input was accepted from the SwiftKey keyboard or not, the hacker would be capable of executing keylogging, memory scrapes, or screen scrapes from any app on the device.
Check Point Mobile Threat Prevention provides a defense-in-depth approach to detecting and mitigating this type of attack. Since MTP can detect both app- and device-based threats, it is capable of detecting devices on which a vulnerable version of SwiftKey is installed as a system app. These devices are then automatically flagged and administrators and users notified of the threat. Using Check Point Mobile Threat Prevention, organizations have visibility into affected devices so that they can monitor the extent of the threat and the reduction of risk over time as device operating systems are updated.