
Introducing Check Point Mobile Threat Prevention
[Click here to learn more about today’s Certifi-gate Threat Advisory.]
Introducing Check Point Mobile Threat Prevention
We’re more mobile than we’ve ever been, so it’s no surprise that smartphones and tablets aren’t our second screens, they’re our first. These devices move massive amounts of data around the clock and around the world, and while some data may be trivial, the increasing trend is that most of it isn’t.
We use mobile devices to manage everything from our health records and banking information to confidential work documents and other critical business content with little concern over its security. But without the right protection, cyber thieves know the information on our smartphones and tablets is theirs for the taking.
A Better Way to Protect Mobile Devices
Check Point today introduces Mobile Threat Prevention, an innovative approach to mobile security for iOS and Android devices that detects and stops mobile threats before they start. Whether your data’s at rest on a device or in flight through the cloud, Mobile Threat Prevention helps protect you from vulnerabilities and attacks that could put that data at risk.
The Highest Level of Mobile Security For the Enterprise
Only Check Point provides a complete mobile security solution that protects devices from threats on the device (OS), in applications, and in the network, and delivers the industry’s highest threat catch rate for iOS and Android. Mobile Threat Prevention uses malicious app detection to find known and unknown threats by applying threat emulation, advanced static code analysis, app reputation and machine learning. It safeguards devices from unprotected Wi-Fi® network access and Man-in-the-Middle attacks and stops access to the corporate network when a threat is detected. It uses real-time risk assessments at the device-level (OS) to reduce the attack surface by detecting attacks, vulnerabilities, changes in configurations and advanced rooting and jailbreaking. And its dynamic threat response prevents compromised devices from accessing an organization’s network and allows organizations to set adaptive policy controls based on unique thresholds for mitigation and elimination of threats on the device.
Full Mobile Threat Visibility and Intelligence
Mobile Threat Prevention’s cloud-based dashboard makes managing supported devices and controlling mobile threats fast and easy. It provides security and mobility teams with real-time threat intelligence and visibility into the quantity and types of mobile threats that could impact their business or users. The solution pushes threat intelligence to Check Point SmartEvent automatically for monitoring of security events and correlation with attacks on internal networks. There, this information is shared and correlated in Check Point’s Threat Cloud, providing the broadest set of threat intelligence that can be used within network environments to prevent cyber attacks from occurring.
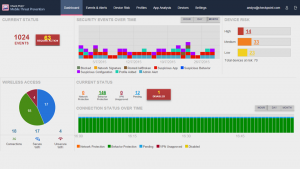
Deploying Mobile Security Has Never Been Easier
Security and mobility teams have enough to worry about. That’s why Mobile Threat Prevention is designed to help them secure mobile devices quickly and confidently through integration and cooperation with MDM or EMM solutions. That helps make the solution highly scalable and delivers strong operational and deployment efficiencies for managing mobile security within a broader security infrastructure. And because end users continue to enjoy their devices as they always have, with an experience that maintains privacy and performance, administrators don’t have to worry about additional training or end user adoption issues. Users can quickly and easily remove any discovered threats themselves to stay protected and productive.
To learn more about Check Point Mobile Threat Prevention, visit http://www.checkpoint.com/mobilesecurity.









