Certifi-gate Found in the Wild on Google Play
New Insights on the Extent, Exploitation, and Mitigation of This New Threat
Three weeks ago, Check Point publicly disclosed Certifi-gate, a new vulnerability on Android. Using anonymous data collected from the Certifi-gate scanner, an app that tells users if their devices are vulnerable, Check Point uncovered some startling new information:
- An instance of Certifi-gate was found running in the wild in an app on Google Play
- At least 3 devices sending anonymous scan results were actively being exploited
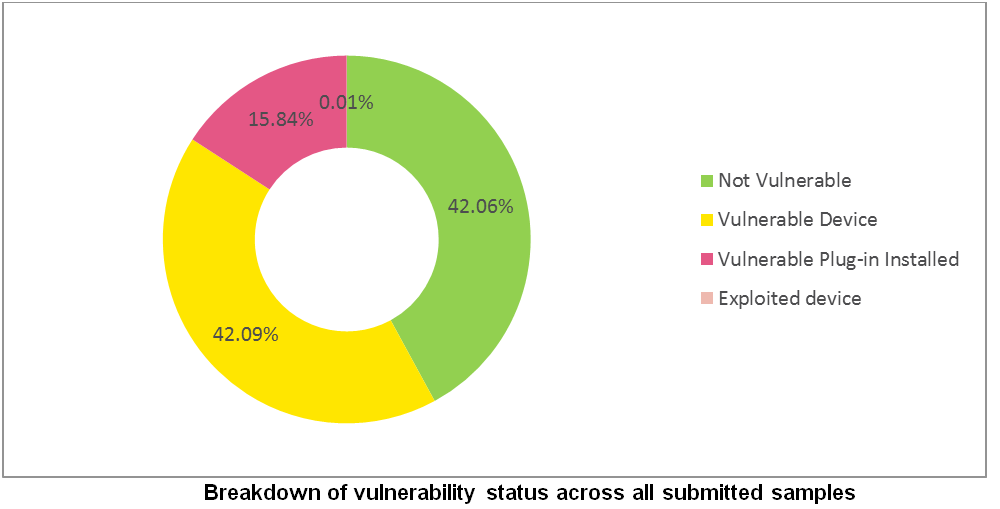
- 15.84% of devices anonymously reported having a vulnerable plugin installed
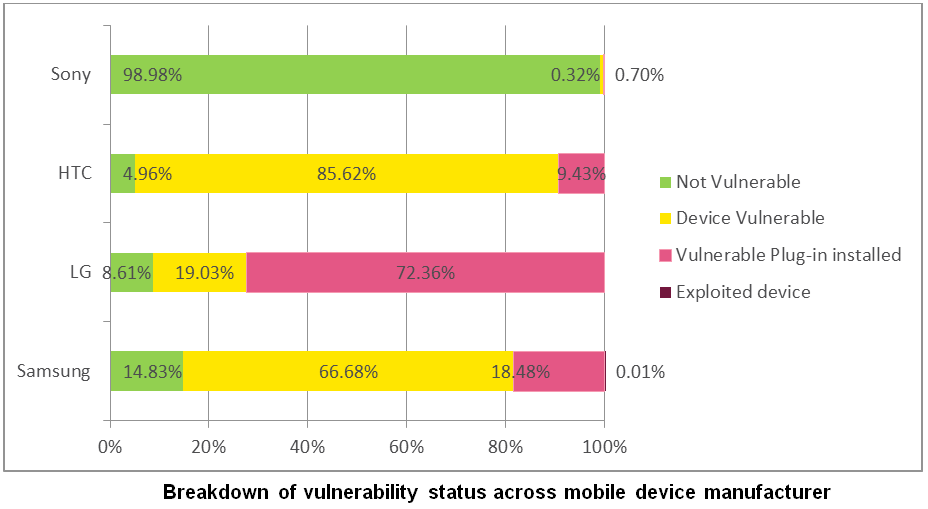
- Devices made by LG were the most vulnerable, followed by Samsung and HTC
In this blog, the research team presents its analysis of Recordable Activator, an in-the-wild exploitation of Certifi-gate, and shares new insights on the extent of the threat and recommendations for mitigation.
In-The-Wild Certifi-gate Exploitation
Recordable Activator
Recordable Activator, an app developed by UK-based Invisibility Ltd., and which has between 100,000 and 500,000 downloads on Google Play, exploited the Certifi-gate vulnerability successfully on three devices evaluated by our Certifi-gate scanner app. The Recordable Activator app bypassed the Android permission model to use the TeamViewer’s plug-in to access system level resources and to record the device screen.
<UPDATE: At August 25, 2015 @ 730AM PDT, the Check Point Mobile Research Team noticed that Google had removed Recordable Activator from Google Play. No further communication was received by Check Point from Google beyond notification that it was investigating the issue.>
Check Point reached out to both TeamViewer and Google regarding Recordable Activator. TeamViewer said that the way this app uses its plug-in is a violation of the code’s use and that it does not allow any third parties to use their code. Google said that it is investigating the issue, but it has not yet removed Recordable Activator from Google Play.
Our in-depth analysis of Recordable Activator highlights the unusual attributes of the Certifi-gate vulnerability.
Overview
A subcomponent in a multi-component utility called “EASY screen recorder NO ROOT” is designed to assist users with capturing the device screen. It’s described on Google Play as:
Recordable is the easy way to create high-quality screen recordings on Android.
- Is simple to install and easy to use
- Does not require root
Android restricts ordinary, non-system apps from interacting with screen capturing functionality, as this introduces significant security and privacy risks. Therefore, this functionality is usually available only to trusted, system-level apps or to apps on rooted devices.
To achieve this functionality, “EASY screen recorder NO ROOT” and its subcomponent Recordable Activator installs a vulnerable version of the TeamViewer plug-in on-demand. Because the plug-in is signed by various device manufacturers, it’s considered trusted by Android and is granted system-level permissions.
From this point, Recordable Activator exploits the authentication vulnerability and connects with the plug-in to record the device screen.
From our research team’s perspective, the developer did a poor job of protecting the interaction with subcomponents. The communication with the Recordable Activator component can be spoofed without any authentication, thus allowing any malicious app to record the screen of the device.
Recordable Activator demonstrates the following inherent issues related to Certifi-gate:
- Unprivileged apps can leverage a vulnerability to take full control of a device without having to request permissions from Android to do so.
- Even after TeamViewer fixed its official version, malicious parties can still abuse old versions of the plug-in to conduct malicious acts.
- Mobile devices can be exploited even if a vulnerable plug-in was not pre-installed on a device.
- Apps that can exploit these vulnerabilities can be found today on Google Play.
- The only fix is for manufacturers to push updated ROMs to affected devices.
In-Depth Analysis
Structure:
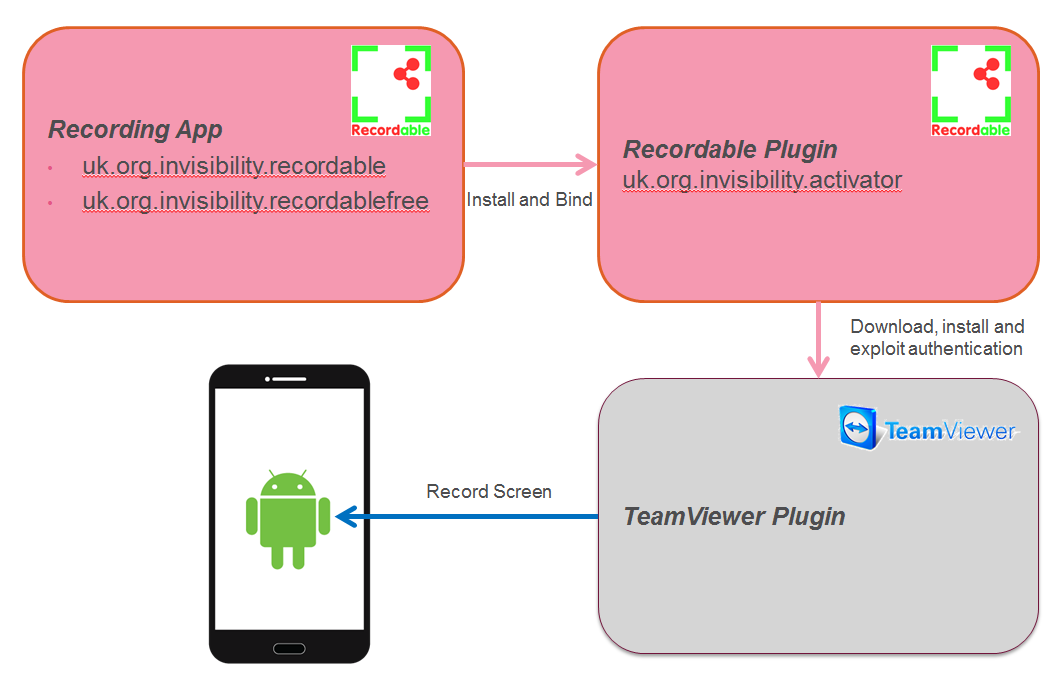
The utility contains two main components: the Recording app (uk.org.invisibility.recordable or uk.org.invisibility.recordablefree) and a Recordable plug-in (uk.org.invisibility.activator)
Vulnerable plug-in download:
The main app supports installing the plug-in or using root / adb shell to enable screen recording through other means. If the user decides to install the plug-in, when the plug-in runs it downloads the TeamViewer plug-in APK, based on the relevant certificate of the device manufacturer.
The download takes place from http://pool.apk.aptoide.com, a third-party APK marketplace. (Note that the User must enable “Unknown sources” for installation.)
Recordable Activator Flow
Operation:
The Recordable plug-in exports a service that wraps around the TeamViewer plug-in service and authenticates with the spoofed certificate field. Next, the Recording app binds to the Recordable plug-in service, which then binds to the TeamViewer plug-in, and returns that binder object back to the Recording app. From this point, the main recording app can communicate with the TeamViewer plug-in directly. There is no security on the Recordable plug-in service to make sure third parties cannot connect to it.
The Recordable plug-in only provides screen recording functionality.
Spoofing the TeamViewer Certificate
Scanner Results & Mitigation
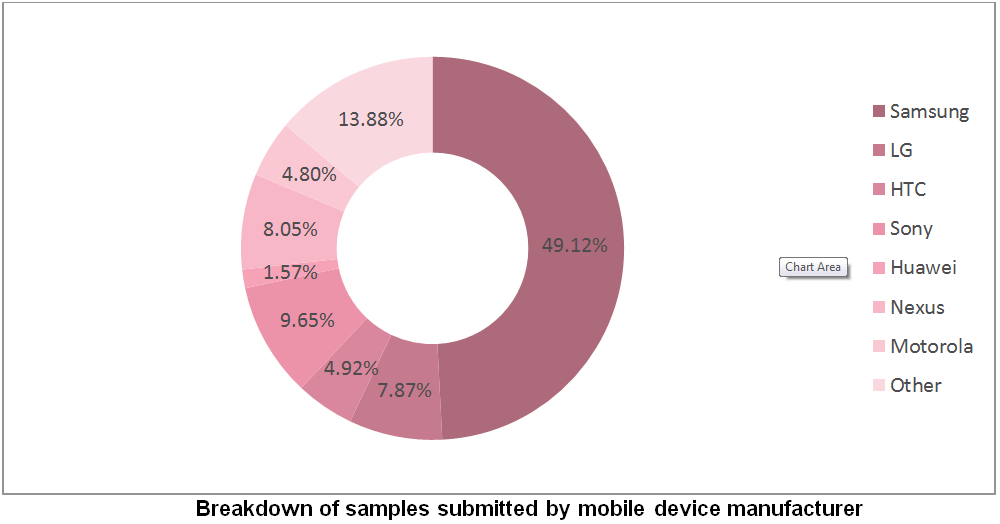
A Look at the Numbers
Exposure & Mitigation
There are three main exposures a user may experience:
 An exploited device
An exploited device
The device is affected by the Certifi-gate vulnerability, a vulnerable mRST plug-in is installed, and a third-party application is exploiting the plug-in to gain elevated access to the device and its sensitive resources. (i.e. the screen or keyboard, etc.).
Mitigation
If your device already has the vulnerable plug-in installed, and there is also a 3rd party application that is exploiting the plug-in:
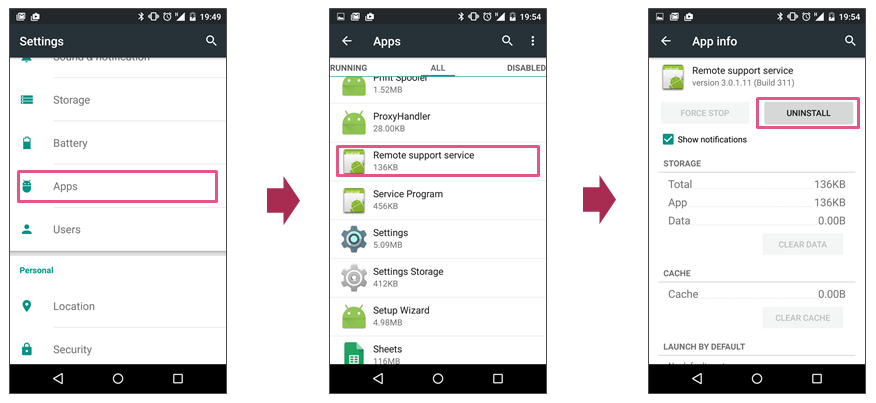
- Try to remove the vulnerable plug-in using the following steps: Settings –> Apps –> Locate the vulnerable plug-in and click it –> Click Uninstall
- Try to locate the exploiting app and uninstall it.
- If the plug-in was pre-installed on the device, you will most likely not be able to uninstall it. In this case, contact your device manufacturer and ask for a fix.
 A device with vulnerable plug-in installed
A device with vulnerable plug-in installed
The device is affected by the Certifi-gate vulnerability and a vulnerable mRST plug-in is installed on the device. Any malicious application can take full control of the device by exploiting the installed plug-in.
Mitigation
If your device already has the vulnerable plug-in installed:
- Try to remove the vulnerable plug-in using the following steps: Settings –> Apps –> Locate the vulnerable plug-in and click it –> Click Uninstall
- If the plug-in was pre-installed on the device, you will most likely not be able to uninstall it. In this case, contact your device manufacture and ask for a fix.
- Download only trustworthy apps, and run the Certifi-gate scanner app after you install questionable apps.
 Vulnerable device identified
Vulnerable device identified
The device is affected by the Certifi-gate vulnerability. A malicious application will need to install a vulnerable plug-in before proceeding with exploitation.
Mitigation
If your device is in a vulnerable state, and you should consider reaching out to your mobile carrier or device manufacturer (Samsung, LG, etc.) to ask when a patch or fix will be delivered.
- The vulnerability can be fully remediated by a new ROM that revokes certificates the old, vulnerable plug-ins were signed with. As far as we know today, no device manufacturers have delivered a patch.
- Our current recommendation is to download only trustworthy apps, and run the Certifi-gate scanner app after installing questionable apps.
- If you are being asked to install a plug-in for a mobile remote support tool, consider canceling the installation.