Analysis of the Sality Gambling Campaign
Check Point has a wide and global install base, from which we receive anonymized logs of millions of security incidents per day. At the end of July, one of our anomaly detection algorithms found the following domains in logs from approximately 15% of our sensors in Vietnam:
blindzone.ivyro.net
argentinaenimagenes.com
imou.wz.cz
burakcay.com
All four of these domains appear in the DNS request of thousands of files in the wild. These files all seem different from one another (different sizes, different file names etc.), but each one is identified by over 45 of 56 vendors in VT as related to Sality, a well-known malware family.
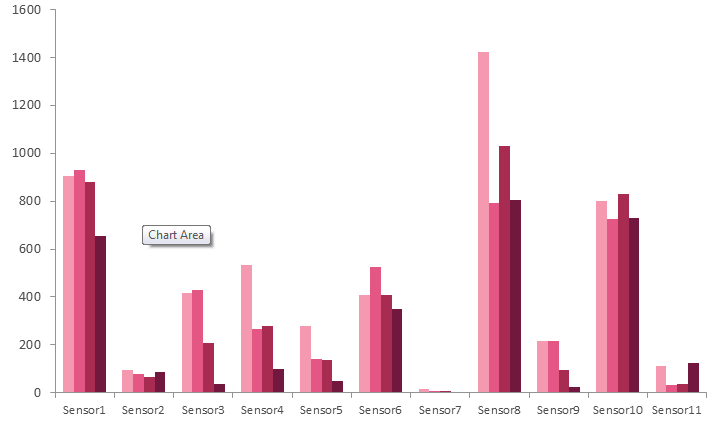
In the graph below, it is evident that indicators for these four signatures always create logs together. The graph details the amount of logs triggered by the four Sality domains during the month of July in each Vietnamese Sensor.
A few words about Sality
Sality was first discovered in 2003, and has advanced over the years to become a dynamic, enduring and full-featured form of malicious code. Since 2010, certain variants of Sality have also incorporated the use of rootkit functions as part of the malware family’s ongoing evolution. Due to its continued development and capabilities, Sality is considered to be one of the most complex and formidable forms of malware to date.
Sality is a Windows 32 bit binary that acts as a dropper, a program that installs a virus, Trojan or worm onto a hard drive. Previous research on Sality found that it delivered fake-AV malware as the final payload. Sality possesses a few self-propagation techniques that are able to infect not only local drives but also USB devices and network folders. In addition, it has the capability to terminate services and processes. We should emphasize that this malware can act as a server as well.
Statistics
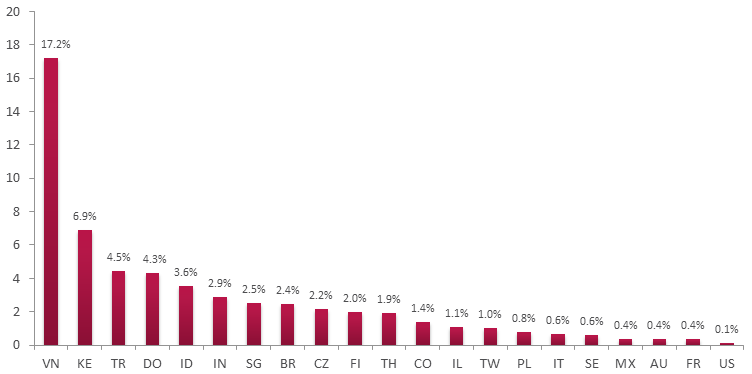
The amount of logs generated by these four domains in Vietnam during the month of July was significantly higher than in the rest of the world. This graph represents the percentage of organizations in each country in which the Sality domains were triggered.
Our Malware Reversing team investigated the samples to understand if this was the start of a new Sality campaign and determine the final payload.
We ultimately concluded that this was a known version of Sality, and that the dropped content was a file packed via a custom UPX packer. This file acts as an intermediate dropper, which in turn drops malware that operates as a spam bot. We found that the samples we investigated are related to two different variants of the dropper. Details of both variants can be found in the appendix.
The email spread by the spammers in these variants of Sality
The mail we found was written in Swedish; it mentions the Ruby Palace casino and appears to be connected to one of its advertising campaigns.
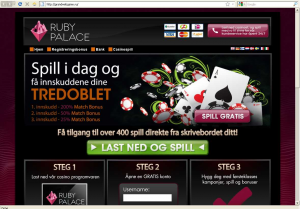
Back in 2013, the “Ruby Casino” was involved in a spamming campaign. A fake casino website asked users to download malicious software in the guise of casino software. The domain ’softlam.fr’ was a redirect for the domain ’IrubyPalaceGoldCasino.com’:
http://www.onlinethreatalerts.com/article/2013/12/21/fake-casino-website-www-irubypalacegoldcasino-com/
The domain IrubyPalaceGoldCasino.com was purchased on November 15, 2013 for one year and is not currently available.
In the current Sality campaign’s spam email, there is a link to the URL ‘melkbos.co.za/mural.htm’ which redirects to the domain ‘grandwebgame.ru’, purchased on August 4, 2015 for a term of one year.
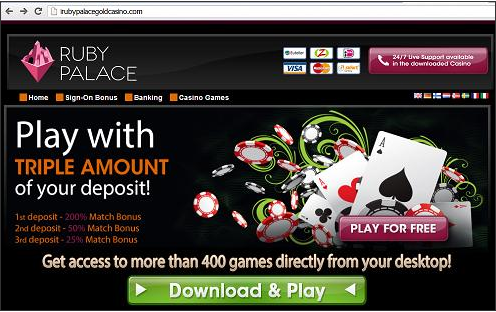
In another interesting fact, a Google search for the casino ‘Ruby Palace’ found a different URL from those detailed above. This URL ‘www.rubyfortune.com’ has a homepage which looks very similar to the website involved in our spam campaign
In conclusion, one of our proprietary algorithms found a wide spread of Sality in Vietnam. We found that this version of Sality drops malware that operates as a spam bot, in this case sending spam about the “Ruby Palace” casino. As a result of this analysis, we enriched our ThreatCloud DB with new indicators that will block this type of Sality traffic.
Appendix
Part 1 – Sality Variants
Variant 1:
These are the URLs received after unpacking (the URL that contains real payload is marked in bold):
hxxp://elcisigur.ro/stats/logo.gif
hxxp://funwebstrankaaqworlds.wz.cz/image.gif
hxxp://gdergi.com/images/image.gif
hxxp://bamas.planet-it.co.id/logo.gif
hxxp://batata.webzdarma.cz/bottom.gif
hxxp://ilmesters.edu.pk/image.gif
This SHA1: 169492897A667322C3FFCABF96834244A4477EC8 is the downloaded intermediate dropper which uses the following URLs to download the spammer:
hxxp://muratusta.com.tr/images/logo.gif
hxxp://fcgagra.ge/images/logo.gif
hxxp://cgaclagosarea.org/images/button.gif
The downloaded spammer has the following SHA1: DE7347E63EBD9D060F98C96B3A2F80C52030022B
The spammer starts communication with the IP address 93.186.196.19 (Germany). After packets are exchanged, the spammer starts to generate spam and uses the following SMTP servers to send it: gmx.de, bluewin.ch, hotmail.com, web.de, gmx.at and many more.
Variant 1a:
These are the URLs received after unpacking (the URL that contains real payload is marked in bold):
hxxp://pspbrzezinki.internetdsl.pl/logo.gif
hxxp://nsdavet.com/images/image.gif
hxxp://tareqbhuyan.com/images/logo.gif
hxxp://clock.retrowatch.ru/images/bottom.gif
hxxp://pousadadomarguaratiba.com.br/images/image.gif
hxxp://ms6.com.br/logo.gif
hxxp://bahtiyarhaliyikama.com/bottom.gif
The data downloaded from the first URL is the same as for Variant 1.
Variant 2:
These are the URLs received after unpacking (the URL that contains real payload is marked in bold):
hxxp://www.cdp-associates.com/images/about.gif
hxxp://callistus.in/images/about.gif
hxxp://www.burakcay.com/about.gif
hxxp://blindzone.ivyro.net/about.gif
hxxp://argentinaenimagenes.com/about.gif
hxxp://imou.wz.cz/about.gif
hxxp://gdergi.com/images/about.gif
hxxp://79.96.88.43/about.gif
This SHA1: 7B6EF356C7FBEAD074C8B4643A42B3B7A5D46C8A is the downloaded intermediate dropper. At first it seemed that the downloaded sample is the same size as the file from Variant 1 and they are therefore identical. However, during the network analysis we noticed a difference in the URLs used to download the spammer:
hxxp://www.demirkonsturuksiyon.com
hxxp://m-ledz.com/logo.gif
hxxp://americanheattreating.com/css/logo.gif
The downloaded spammer has this SHA1: 539AF8BC5FB36E34FF4FE6869CDAC998F1C9575D
The spammer uses this IP address for its initial communication: 31.193.142.216 (United Kingdom)
The following differences were noticed between the Variant 1 spammer and this one:
- Lack of these hardcoded SMTP servers:com, smtp.live.com and msn.com.
- Lack of packet’s response information parsing.
Part 2 – IOCs
Sality:
SHA1:
adf205560e8bfde14378471ebee9342853781c50
d18dc8b64eaabb3047d503403f47f406ffe478b7
59bb3e745a5de05e821544522f5785d15cb65c00
a95455da6013caa421f9105b6b0aa9cc60b74cbb
29482261e903199483eba567bc082c5746526d46
97ce2e0e27397880966087225156f1bbf397c37b
Mutex:
uxJLpe1m
Ap1mutx7
Mutexes in the system (responsible for multiple injections): ${process_name}M_${pid}_
Device with the following name: \\.\amsint32
Presence of the following service on computer: amsint32
Presence of the autorun.inf file on each drive in the following format:
[AutoRun]
;RnIgCalmdtltebSOlLpOKdGxVct
;fywxkBXEybbyxlRyBLvkFYAmBxlysFmmDyXRL
oPEn=${filename}
;gFmhGt quidbarQudu
Shell\opEN\DEFAulT=1
;uXXNclivGaiv stjGLYctrcH NMrFDPphybeVqD
shell\explOrE\COMmaNd = ${filename}
;
sheLL\oPen\COMmaND= ${filename}
;GjrXu aBfDiQmTxKO YlFKiHlnCWwlIjWDe tqmv
sheLL\AutoPLaY\CoMMaNd=${filename}
${filename} is the name of the file that was dropped by Sality (the same copy) and resides in the root directory of a drive.
Note: the algorithm of case sensitivity/insensitivity was not reversed. We can try to check autorun.inf file for structure prevented above and then check the hashsum of ${filename} file.
Presence of the following sub keys in HKEY_CURRENT_USER\Software\${random_or_pseudorandom_name}:
- -993627007 with its own sub keys
- Keys in the following format A%d_%d = ${ip_network_form} of type REG_DWORD
Note: there is no need to reverse an algorithm of key name generation (if it exists), because we can check all keys of HKEY_CURRENT_USER\Software\ for the presence of the conditions specified above. .
Network (access to the following resources):
http://elcisigur.ro/stats/logo.gif
http://funwebstrankaaqworlds.wz.cz/image.gif
http://gdergi.com/images/image.gif
http://bamas.planet-it.co.id/logo.gif
http://batata.webzdarma.cz/bottom.gif
http://ilmesters.edu.pk/image.gif
http://www.cdp-associates.com/images/about.gif
http://callistus.in/images/about.gif
http://www.burakcay.com/about.gif
http://blindzone.ivyro.net/about.gif
http://argentinaenimagenes.com/about.gif
http://imou.wz.cz/about.gif
http://gdergi.com/images/about.gif
http://79.96.88.43/about.gif
http://pspbrzezinki.internetdsl.pl/logo.gif
http://nsdavet.com/images/image.gif
http://tareqbhuyan.com/images/logo.gif
http://clock.retrowatch.ru/images/bottom.gif
http://pousadadomarguaratiba.com.br/images/image.gif
http://ms6.com.br/logo.gif
http://bahtiyarhaliyikama.com/bottom.gif
Backdoor:
SHA1:
7b6ef356c7fbead074c8b4643a42b3b7a5d46c8a
169492897a667322c3ffcabf96834244a4477ec8
Mutex: qiwuyeiu2983
Network:
http://muratusta.com.tr/images/logo.gif
http://fcgagra.ge/images/logo.gif
http://cgaclagosarea.org/images/button.gif
www.demirkonsturuksiyon.com
http://m-ledz.com/logo.gif
http://americanheattreating.com/css/logo.gif
Spammer:
SHA1:
de7347e63ebd9d060f98c96b3a2f80c52030022b
539af8bc5fb36e34ff4fe6869cdac998f1c9575d
Mutex: sobakavolos33919
Network:
93.186.196.19
31.193.142.216