iOS Core Application Design Flaw May Expose Apple ID Credentials
Check Point alerted Apple to a privacy issue in iOS core applications that may expose a user’s credentials even though the user performed a sign out. The fix is now available through the iOS 9 release.
Introduction
iOS is a mobile operating system created and developed by Apple and distributed exclusively for Apple hardware. It is the operating system that presently powers many of the company’s mobile devices, including the iPhone, iPad, and iPod touch.
The operating system offers users a very convenient way to manage your device with an Apple ID.
Your Apple ID is your user name for everything you do with Apple: shop the iTunes Store, enable iCloud on all your devices, buy from the Apple Online Store, make a reservation at an Apple Retail Store, access the Apple Support website, and more. The iOS market share is estimated to be more than 40% of the mobile device industry.
Executive Summary
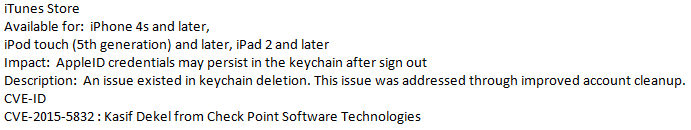
Check Point security researcher Kasif Dekel recently discovered a software design flaw (CVE-2015-5832) in a core feature responsible for managing credentials for core Apple applications, like the App Store, in certain versions of Apple’s operating system (prior to iOS 9). This flaw could lead to sensitive data exposure from the mobile device, as it keeps the login credentials even after the logout operation is performed.
Apple verified and acknowledged the security issue and has released a security advisory that addresses this issue with an upgrade to iOS 9. https://support.apple.com/en-il/HT205212
Technical Details
Due to a security bug in the application, the logout mechanism allows the device to perform the logout process without purging the sensitive keychain data stored by the application.
A keychain is an encrypted container that holds passwords, certificates, identities and more for multiple applications and secure services. Keychains are a secure storage container, which means that an application can access only its own keychain items. To share the data between apps, they must have the same Access Group in code signing entitlements.
On a jailbroken device, a tool that has been signed with a self-signed certificate with a “wildcard” entitlement grants access to all the keychain items that would have been granted had the tool been signed with each individual entitlement.
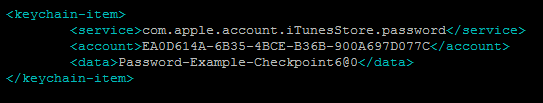
An example of such information pulled from the keychain:
A common and highly likely way in which a user’s private data could be exposed is when a device (iPhone/iPad/iPod) is sold, without the owner being aware of the proper way to clean the application keychain data.
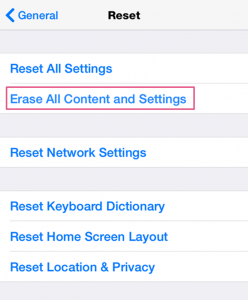
It is important to note that even if the user logs out from the application and performs a partial device reset (“Reset All Settings”), the information will still be stored in the keychain.
The proper way to avoid this kind of sensitive data exposure for pre-iOS 9 users is to select “Erase All Content and Settings” in the device settings.
Summary
“Apple worked closely with Check Point on this issue. We are very happy that the fix is available through iOS 9, which is expected to have a high adoption rate. This eliminates the risk of the vulnerability being exploited,” said Oded Vanunu, Security Research Group Manager at Check Point.
Check Point customers using Mobile Threat Prevention to protect iOS devices from advanced mobile threats are already safe, due to the product’s Anti-Jailbreak protection feature which eliminates the primary step to exploiting this security flaw.
Check Point continues to be on the lookout for vulnerabilities in common software and Internet platforms, disclosing issues as they are discovered, protecting consumers and customers against tomorrow’s threats.