Israeli Public Sector Targeted by Zeus Trojan Hidden in a Word Document
Two months ago, a malicious Rich Text Format (RTF) document came to the attention of Check Point Threat Intelligence & Research via a worried high-profile client in the public sector. The file had been sent to many employees, several of whom opened the file; as a result, their machines became infected. Check Point took actions to prevent this document from further infecting the customer’s network, and also analyzed the file to better understand the attack. The result was a discovery of a larger-scale campaign that has been targeting Israeli public and private organizations for some time.
The Investigation
As the team conducted research it quickly became apparent that this was no ordinary phishing or macro attack: the document utilized three different remote code execution vulnerabilities in MS-Word. The specific vulnerabilities being exploited were enough to determine that this malicious document was not crafted by hand, but rather auto-generated by a well-known exploit kit called Microsoft Word Intruder (MWI).
MWI has been marketed in underground forums since mid-2013 to anyone willing to pay a few thousand dollars. Would-be attackers provide an executable payload of their choice, and MWI crafts a document that will execute that payload when opened by their target(s). MWI also provides a control panel where attackers can track their campaigns, including successful exploitations and information about their victims, such as IP addresses and geographic locations. More detailed information about MWI can be found in this report published earlier by Check Point and in this detailed report by FireEye.
The payload bundled with this specific malicious document was a generic derivative of the Zeus Trojan, with all the usual functionality: the modification of browser security parameters; stealing FTP credentials, cookies and mail settings; and the ability to download and execute additional modules.
![]()
Figure 1. Excerpt of Malicious RTF file, including a report back to the C&C server using an INCLUDEPICTURE directive.
Analysis of the network traffic generated by the Zeus Trojan revealed that it was “phoning home” and sending an HTTP GET request to a live C&C server. This server’s domain was owned by a legitimate local residential letting agency abroad, which had been compromised and used as a pivot for the campaign.
From the contents of the malicious C&C server, it later became clear that the server was used as a rendezvous point for seven groups of campaigns, each with a separate control panel:
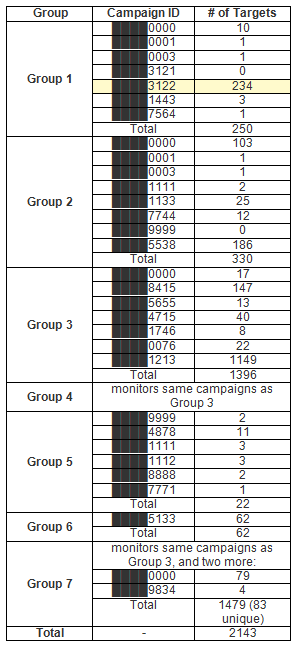
Figure 2. Breakdown of targets by panel and campaign ID. The campaign associated with our infected .rtf is highlighted. Group names have been replaced with generic numbers.
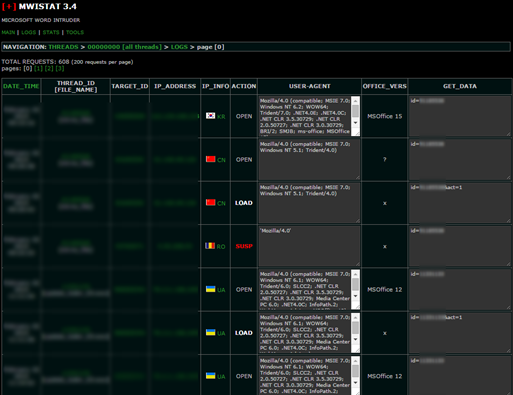
Figure 3. The MWIStat statistics panel used by the attacker to track their campaign. “LOAD” in the action column indicates successful infection.
Some control panels overlapped in their monitoring functions. For example, the Group 4 and Group 3 control panels monitored the same campaigns. Many campaigns disseminated various kinds of Trojans. Others seemed to be “dummy” campaigns, used as a proof of concept.
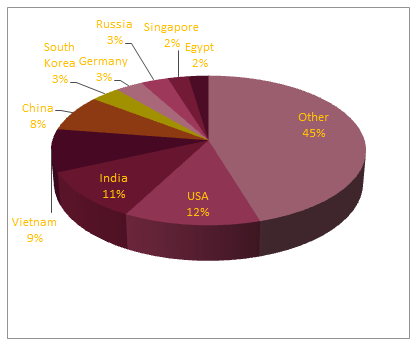
Figure 4. Breakdown of target IP addresses by geographical region for campaign 1213 from Group 3. This campaign, hosted alongside the campaign that generated our RTF file, targeted 1,149 machines worldwide.
For example, campaign 1133 from Group 2 targeted a total of 25 machines – 24 in Ukraine and one in Russia – and infected them with LiteManager, a Remote Administration Tool. The LiteManager installer used hardcoded credentials to contact its C&C server, probably to inform the operator of successful installations. That campaign turned out to be targeting a variety of companies belonging to the banking, telecom and hosting sectors, as well as several information security vendors. A single IP address had been recorded logging in to the server’s web interface; this address was probably associated with the campaign’s manager. The IP address belonged to a German-based hosting company, and is currently inactive.
The log files recovered from the server allowed a closer look at the list of IP addresses targeted by the same campaign as the original malicious RTF file we acquired (3122, Group 1). Upon closer inspection, it became apparent that it was not a coincidence that the original client that filed the complaint was from Israel.
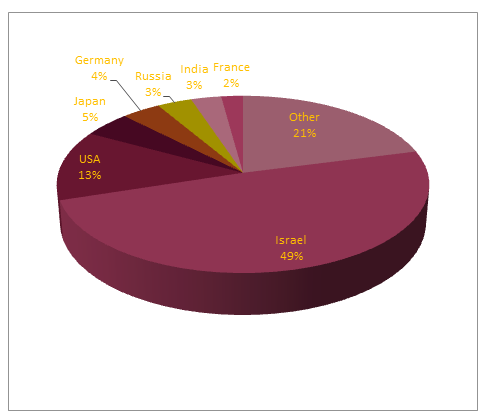
Figure 5. Breakdown of target IP addresses by geographical region for campaign 3122 from Group 1. This campaign targeted 250 different machines using a variant of the Zeus Trojan. Nearly half of all targets of this campaign were located in Israel.
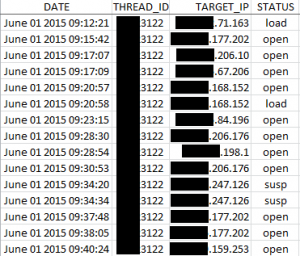
Figure 6. Logs recovered from the server, documenting the targeted machines “phoning home.” The “THREAD_ID” column lists the campaign ID. The “STATUS” column reports on the infection state: “open” means the malicious document has been opened, “load” means the payload has been executed, and “susp“ means MWI suspects the connection did not come from an actual infected machine.
There are many reasons campaigns can end up with a lopsided geographical distribution of infection victims; that, alone, does not necessarily imply a “targeted campaign” scenario. Sometimes attacks on a particular location just happen to be the most convenient to carry out, or the most successful. However, this case was different. Israeli targets were not just over-represented; the list of targeted IPs contained a number of Israeli government agencies, security industry firms, municipal agencies, research institutions and even hospitals. In total, over 200 machines and 15 distinct Israeli firms and institutions were targeted.
Who orchestrated the campaign, and for what purpose? At this stage, we cannot be sure of the answer. Still, we can say that this campaign appears to be politically motivated, instigated against a particular nation-state. Such campaigns are usually orchestrated by adversaries which are themselves nation-states or political organizations. On the other hand, campaigns launched by such adversaries tend to make use of dedicated tools that are specifically tailored for the occasion. It is unusual for such a campaign to rely on “off-the-shelf” materials such as MWI and vanilla Zeus.
Regardless of the campaign’s origins, the advice for defending against exploit kits as an attack vector remains the same: update your software; update your AV & IPS signatures; audit files with sandbox analysis before they enter your network; employ anti-bot and post-infection technology to assist in identifying hosts that have been compromised; use a script blocker for your web browser; and be wary of any web links or documents that came unsolicited or from a party you don’t fully trust.