Love is in the air (along with malware in your email): Facebook email redirection used to overcome spam filtering
Every year in the middle of February, much of the world takes a brief moment to focus on love. I’m pretty sure there is an element we could trace back to greeting card suppliers, florists, or purveyors of fine chocolates, but maybe that is just the cynic in me.
But what strikes me as interesting (as a security guy), is how much the concept of love seems to be front and center in the security world. Anyone remember the “I LOVE YOU” email worm, which wreaked havoc in 2000? And still fresh in our minds is Heartbleed, which had little to do with love, but I think the nifty logo got it much more coverage than if they had called it the OpenSSL crypto buffer over-read vulnerability.
So, on that theme, I thought I would share a recent experience. I was just contacted by my could-be soul mate in an email saying:
“Hi, i am Mary, am happy the time i saw your profile on Facebook and i love it,i will like to be your friend like they say a day begins a story,but the issue is that i don’t normally have much access in Facebook due to some personal reason. please contact me with my email address i will like to show you my photo and at the same time you will know more about me. email address. (maryboldeng@hotmail.com )”
Sure, the spelling and grammar are a pretty good hint that this is unlikely to result in a meeting with my soul mate, but the idea of starting a “story” was too enticing.
That, and the fact that I was wondering how this email made it all the way to my inbox, given a range of defenses that should have prevented that.
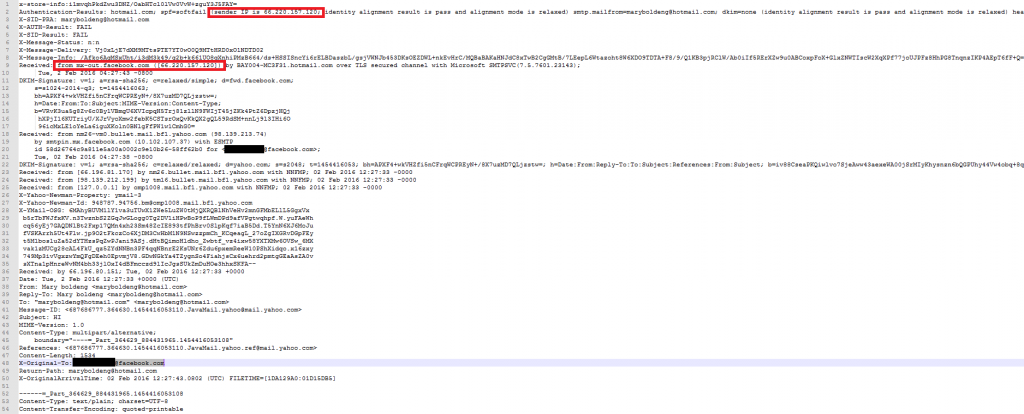
As a security expert, I did open the email headers first, just in case Mary’s intents were not genuine. What I found surprised me… The email comes from Facebook servers and while I would expect this to be spoofed this is indeed genuine and the cause for the spam filter bypass.
Mary sent the email to my Facebook email address which redirected this to me. I almost forgot about that, but a few years ago Facebook offered to save a name for email services using Facebook. I guess Facebook decided to sunset this feature and they redirected email’s destined to my Facebook address to the email address I signed in with.
So, now my email provider gets this email coming from Facebook, which somehow has a good enough reputation for not spamming (really?!), and trusts the message to be genuine.
If I would answer Mary, “she” could then return an email with malicious attachments, which will likely pass through less restrictive spam filtering due to conversation reputation as I interacted with “her”. And if Mary, or whoever is really behind this is any good, there’s a decent chance they could sneak through something malicious. Yet another reminder that we all need to remember to stay alert, and just because our email providers are doing a better job blocking spam, doesn’t mean “advanced” social engineering attacks won’t get through.
So though I was hoping to find my love just in time for Valentines, I am yet again left with a valentine broken heart returning home to my old lady…
Just kidding, I LOVE YOU hon <3
GN
Gad Naveh and Ofir Israel are security researchers for Check Point Software. They are based in Tel-Aviv, Israel.