In the Wild: Mobile Security Observations from the Check Point Research Team
Time goes by fast, and mobile malware develops faster still. In the past few weeks, our mobile security team encounters several instances of innovative new malware. Whether these are complex chains of action or new methods of communication with C&C servers, it’s clear that mobile cyber threats advance quickly. The Check Point Mobile Threat Prevention research team constantly investigates new malware to stay ahead of threats. Here are some new stories our team thinks are worth a further look.
HummingBad keeps on humming
Researchers have found new instances of malware that closely resemble our recent discovery of HummingBad. The new variant, which is part of the LIBSKIN malware family, achieved widespread distribution in third-party app stores. Like its sibling, LIBSKIN initiates a rooting process through a module called right_core. The malware then pops up ads in changing intervals in order to hide which app from which these pop-ups pop.
Why is this interesting?
Both malwares have complex chains of action they use to root the device, and they use encryption to conceal their malicious intent from security scans. This makes it more difficult for static code analysis to reveal the true nature of the malware. However, dynamic analysis can expose the malware and can alert users, as Check Point Mobile Threat Prevention (Schedule a demo today!) did when it discovered the HummingBad malware.
Mazarbot – a malware from the dark side
This nasty piece of malware is extremely interesting because it introduces a new form of C&C to the mobile world. Mazarbot belongs to the GMBot malware family, like many other bankers, including the . The malware is spread via SMS messages and, once the user installs it, the malware installs TOR on the device. TOR enables the malware to communicate with its C&C server through the DarkNet to avoid detection.
Up until now malware used regular C&C servers which can be shut down once exposed. This new method of communication protects the servers and all of the communications between the attacker and the malware.
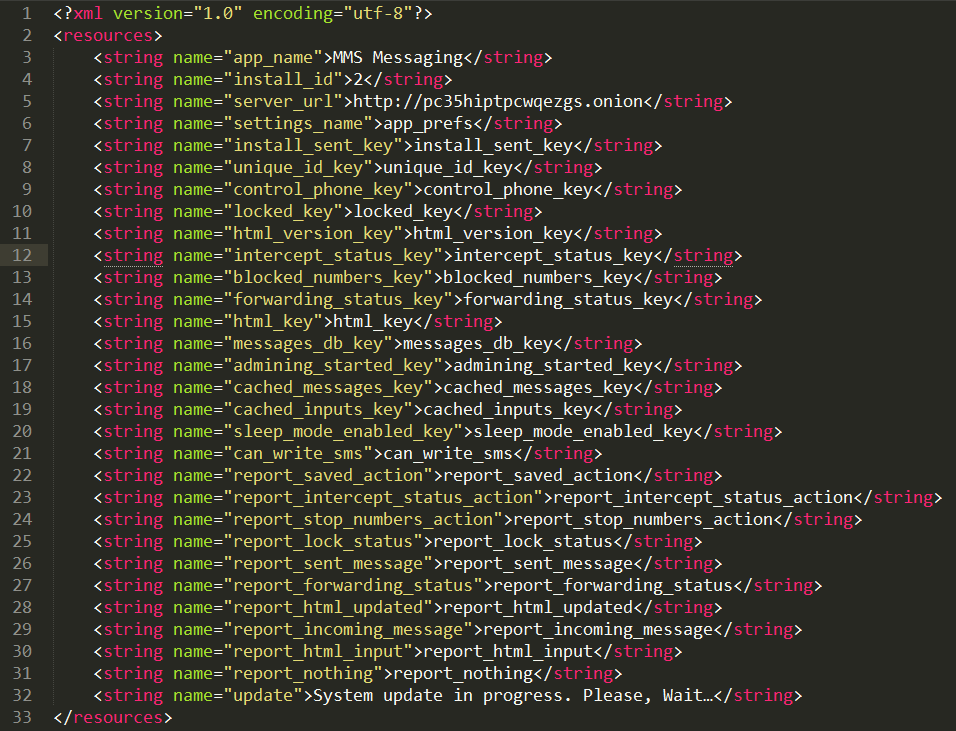
In the following image, you can see the TOR .onion URL the malware uses, as well as other function names the malware can initiate. It is interesting to note that the Mazarbot handpicks its victims. Unlike previous versions of GMBot, the target list is not embedded into its code, but instead downloaded from the C&C server. In addition, the MazarBot has a feature which existed also in previous GMBots. The feature aborts the malicious activity if it detects the malware is running on devices set to use the Russian language. Both features help the malware to keep a low profile and hide its purpose.
MazarBot can read SMS messages and forward calls. By doing so, the Mazarbot can steal two-factor authentications, similar to previous malware we have reported. Moreover, the malware can gain total control of an infected device including configuring a proxy that allows it to become a Man in The Middle to intercept device communications.
Why is this significant?
MazarBot is not the first to introduce C&C communication through the DarkNet. Several malwares have beaten it to it. For example, the infamous Cryptowall uses the Darknet I2P overlay network to communicate with its C&C servers. Other malware, such as the Mevada botnet and the ChewBacca banker use TOR to communicate anonymously. However, MazarBot is the first mobile malware to do so. Like many other malware developments, this technique was first detected in the PC world and later implemented in the mobile world.
The developments portrayed above, as well as many others, stress the need for comprehensive security measures which are capable of detecting not only known malware but also unknown malware innovations that evolve over time.
- MazarBot SHA: 73c9bf90cb8573db9139d028fa4872e93a528284c02616457749d40878af8cf8
- HummingBad Parent SHA: a65f7dcf5eba2c68ef57e162a3de466e762613009c15b21844a572d1a4f1f834
- SHAs of some of the dropped apps:
- a3cf3a96d61fc644faed4dfc54e02997eb954826de11524a094acb17bd1bce22
- 5eafc616b18dce68faa2e3159d08d3997f3a86c8fe710786aa0b262ef6280541
- 946d5d2fba5956f5499c648802d77f1237c3002c056e1c2060ba6482b3585bdd
Learn more:
Check Point Mobile Threat Prevention
See it in action:
Schedule a demo of Mobile Threat Prevention
Oren Koriat is a Mobile Information Security Analyst in the Check Point Mobile Threat Prevention Research Group. He is a technology enthusiast and a polyglot, whose expertise is in the field of Asian mobile software markets. Koriat holds a degree in linguistics from Bar Ilan University.