Adwind – Malware-as-a-Service Reincarnation
Executive Summary
Adwind Remote Access Tool, known by various names due to its many reincarnations, is a backdoor fully implemented in Java and therefore cross-platform. It is a highly popular tool used in both massive spam campaigns and targeted attacks against financial institutions worldwide. In all versions (Frutas, Adwind, AlienSpy, UNRECOM and JSocket), it has been available for purchase based on registration on an official website – a concept known as malware-as-a-service.
As a backdoor, Adwind RAT does not infect computers and spread independently, but relies on the user, who must double-click the .JAR attachment or open the file.
Currently, the malware is distributed under the name JSocket via an official website with various subscription packages offered to potential customers, including basic technical support.
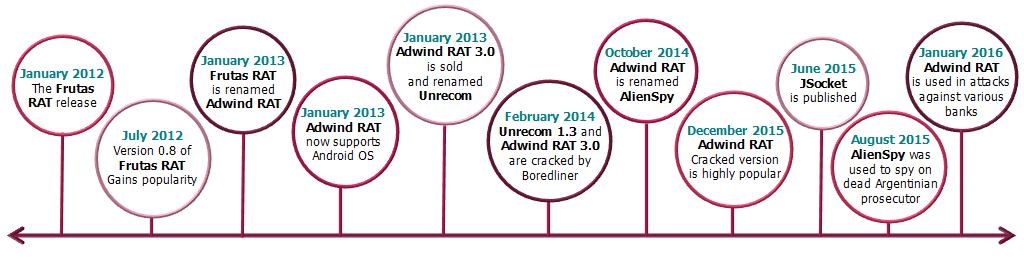
Reincarnation Timeline
Known Attacks
Adwind RAT is mostly used by standalone attackers and distributed in large-scale spam campaigns. However, there are also indications that various versions of the tool have been used in targeted attacks.
In August 2015, an extensive investigation found that AlienSpy was used in an espionage campaign against an Argentinian prosecutor who died in January that same year under mysterious circumstances.
At the end of 2015 and beginning of 2016, after UNRECOM and Adwind RAT were cracked, Kaspersky reported that a sample obtained by the security company indicated a targeted attack against banks in Singapore. Attacks against banks in the United Arab Emirates, Thailand, Sweden and even Russia were observed as well. Most of these attacks were based on spear-phishing techniques.
It has been reported that between 2013 and 2016, 443,000 attacks against private users were conducted by various reincarnations of the RAT.
Check Point Observation
Check Point Threat Intelligence analysts have noted numerous attack attempts worldwide by known variants of the RAT. Attacks were directed at machines in Canada, Europe, the United Arab Emirates, United States and Russia.
Background
Adwind RAT was first identified in January 2012, in the form of a backdoor Remote Access Tool dubbed Frutas RAT and most likely originated in Mexico. The tool, written in Java and cross-platform, was published on a Spanish-speaking hacking forum by its developer, a user with the name of ‘Adwind.’
During the months that followed, several versions of the malware were released by the same user. Within a year of the malware’s first publication, it was distributed on underground forums, free-of-charge for registered members.
The version released in July 2012 included these functions:
- Run and download selected files
- Open a selected webpage in a browser
- Screenshot capture via right click
- Send popup messages
- Password capture of various services such as MSN messenger, Internet Explorer, Google Chrome and Yahoo Messenger
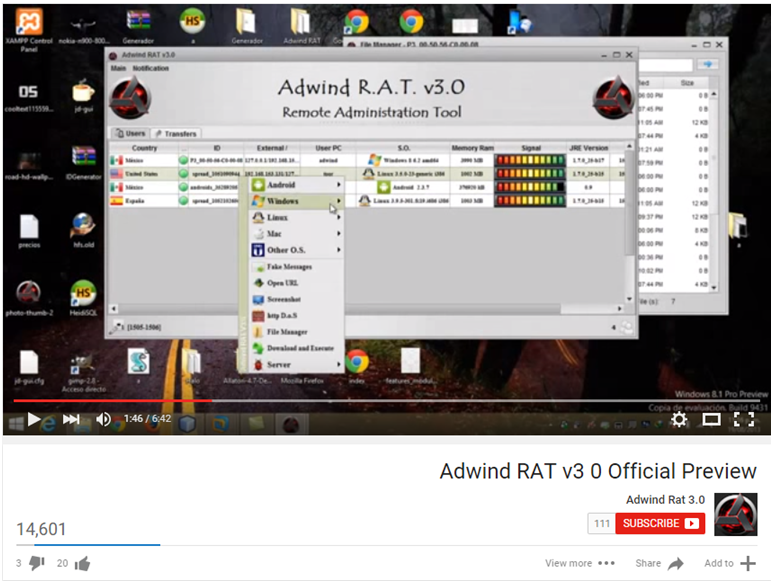
In January 2013, the developer changed the malware name to Adwind RAT as another version had been released and was already gained popularity among Spanish-speaking cybercriminals. The newly-branded malware gained worldwide publication which reached its peak around May 2013. By that time, the malware became a highly popular tool among non-Spanish-speaking attackers. Version 3.0 of the Adwind RAT, which included support for Android OS, was announced by its author on YouTube, which created a channel for publishing tutorials.
The use of the Adwind RAT in targeted attacks was first observed in the summer of 2013 in the Asia-Pacific region.
In November 2013, the malware’s name was changed again, to UNRECOM. The name stands for UNiversal REmote COntrol Multi-Platform. UNERCOM has all of the Adwind RAT capabilities, including remote desktop control and an extendible plugin system. In addition to the rebranding, the ownership of the malware was sold to Unrecom Soft, according to a note on the webpage adwind.com.mx, owned by the original developer.
According to an explanation provided by a Mexican re-seller, the new owners are a company called Lustrosoft, behind which is a single developer who would continue constantly updating and improving the malware. The re-seller also claimed that the original owner sold the malware due to legal issues.
In February 2014, both UNRECOM malware and Adwind RAT version 3.0 were cracked by a hacker dubbed Boredliner and became open to the public. The two cracked versions, which are based on the same source-code, were highly popular among cybercriminals during 2014-2015.
The availability of the two free Java-based RATs led the original author to issue a new RAT dubbed AlienSpy, released in October 2014. Compared to its predecessors, AlienSpy is a more sophisticated and complex RAT whose capabilities include a sandbox detection tool, the use of Transport Layer Security cryptographic protocols to secure C&C communications, and detection and disabling of Antivirus packages. The tool has been used in worldwide campaigns, including targeted attacks against finance, government and energy sectors. It is most likely that AlienSpy is based on the source code UNRECOM, rather than Adwind. Around April 2015, after a thorough report was published by the security vendor Fidelis, the malware’s activity was suspended.
In June 2015, JSocket RAT, the latest known reincarnation was published.
The tool is available for sale on a subscription basis on the website JSocket.org; this concept is known as malware-as-a‑service. Offered services include various subscription plans, basic technical support and additional paid modules. All services are available for registered users only. As of January 2016, the registration is open to all.
Check Point Protections
Check Point protects its customers against all known variants of this threat at each stage of the infection chain. The protections relevant to this campaign are:
- Anti-Virus blade includes hashes signatures for the RAT.
- Anti-Bot blade includes network signatures for the RAT’s behavior, as well as C&C domains.
(Backdoor.Win32.Adwind.A-E; Backdoor.Java.Adwind.A-C)
References
- http://www.kaspersky.com/about/news/virus/2016/Adwind
- https://securelist.com/securelist/files/2016/02/KL_AdwindPublicReport_2016.pdf
- http://www.symantec.com/connect/blogs/cross-platform-frutas-rat-builder-and-back-door
- https://www.fidelissecurity.com/sites/default/files/FTA_1015_Alienspy_FINAL.pdf
- http://motherboard.vice.com/read/malware-hunter-finds-spyware-used-against-dead-argentine-prosecutor