Threat Alert – KeRanger MAC OSX Ransomware
Research by: Ofer Caspi
Overview
- A new ransomware dubbed ‘KeRanger’ was discovered on March 4, 2016. The malware is distributed via the Transmission BitTorrent installer version 2.90 for OSX. Unlike most ransomwares, the targeted operating system is Mac OSX, which makes KeRanger the first active ransomware to target this operating system.
- The compromised Transmission installer includes an executable disguised as an .rtf file. When the application is launched, the malware is copied to a file in the user Library folder. The process runs silently on the machine for three days, after which the malware begins encrypting files.
- KeRanger encrypts not only all files in the /Users folder, but also files found in the /Volumes folder – files stored in external hard drives and servers, which are in many cases backups needed in case such an incident occurs.
- Apple has added a relevant signature to its XProtect anti-malware and revoked the Mac app development certificate which was illegally obtained and used by the attackers to bypass Apple’s Gatekeeper protection. The Transmission Project has removed the malicious installers from its website.
Background and Analysis
KeRanger, the first fully-functioning ransomware targeting the Mac OSX was first detected on March 4, 2016.
The malware was distributed via the Transmission BitTorrent installer version 2.90 for OSX. The application was signed with a different code signature than the one previously in use.
Unsuspecting Mac users downloading the infected Transmission installer also download an executable disguised as a rich-text-format file named general.rtf.
When the application is launched, the executable is copied to a file named .kernel_service in the user Library folder.
OSX file and folder names which begin with a dot are hidden. This allows the executable to run on the machine for three days, during which time additional files, named .kernel_pid and .kernel_time, are created in the user Library folder.
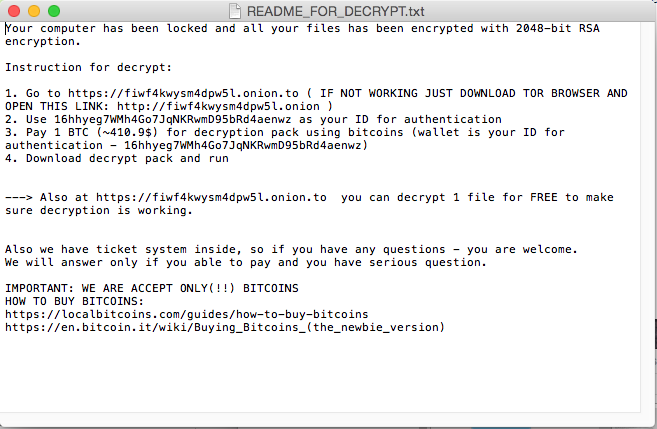
The malware waits three days before beginning to encrypt files. During that time, it notifies its C&C server every 40 minutes that it is alive. In response, it receives a message encoded with base64 which contains an encryption key, and a text file called ‘README_FOR_DECRYPT.txt’ which contains the payment instructions. The attackers offer to decrypt one file ‘for free’ to make sure the decryption process works.
The instructions file – ‘README_FOR_DECRYPT.txt’
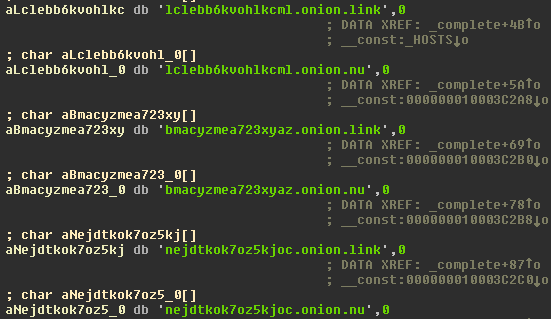
The C&C connection is based on websites used as proxy servers to the TOR network (onion.link, onion.nu). The domains are hard-coded identically for all infected machines.
As of March 8, the C&C server is still active.
The C&C server response
The hardcoded C&C domains used by the ransomware
Note – The malware is not persistent. Therefore, if the victim restarts the computer, the kernel_service process only runs if the infected Transmission file is opened again.
KeRanger ransomware encrypts files in the /Users folder as expected, and in addition, it also encrypts files in the /Volumes folder – external hard drives and servers which are connected to the machine.
Although not unique, this is a concerning capability of the malware as external drives usually contain the backups to the files stored on the computer.
Recommended Protections
Apple added a signature detecting the malware to its XProtect anti-malware and revoked the developer certificate used to sign the malicious copy of Transmission.
There should be no new infections unless the attackers release an updated variant of the malware.
However, users who downloaded the infected installers between 11:00am PST March 4 and 7:00pm PST March 5 can still run the executable file and the Mac will not prevent that as the file was already successfully opened on the machine. Therefore, users are suggested to take the following steps –
- Check whether the executable file (rtf) is present in your user Library folder and if so, delete it as well as the Transmission application currently installed.
- Check whether a process named ‘kernel_service’ is running. If so, check whether there is a file named ‘kernel_service’ in your user Library folder and if so, terminate the process with ‘Force Quit’ in the Activity Monitor. By doing that you can prevent KeRanger from beginning the encryption process even if you already run the ‘general.rtf’ executable.
- Check whether the infected files (.kernel_service, .kernel_pid, .kernel_time) are present in your user Library folder and if so, delete
Check Point Protections
Check Point protects its customers from KeRanger ransomware with its Anti-Virus and Anti-Bot blades –
- Anti-Bot Signatures
- Network signatures for the malware’s behavior
(Trojan-Ransom.OSX.KeRanger.A-B)
- C&C domains signatures have been added
- AV Reputation signatures
- Infected files signatures have been added
Additional Technical References