Lessons learned from the uKnowKids breach
Nothing is as important as our children. We will do anything we possibly can to protect them. Some parents even use apps to make sure their kids are safe, but this can turn out to be a double-edged sword.
Recently, the database of the uKnowKids app was breached, and sensitive user information was leaked. But while the app is intended to protect kids, there’s no way to ensure it’s used for this purpose. In the past, we’ve seen various legitimate “spy phones” apps sold and abused by malicious actors.
Many apps, uKnowKids among them, can collect tons of sensitive information about devices and users. In fact, according to a report published in Dark Reading, out of over 315,000 apps, 62% of iOS and 86% of Android apps display invasive behavior like collecting data from users these apps don’t need.
This is a strong indication of a much bigger problem, especially since many users install applications that collect different types of data about devices and users. One can arguably ask, “So what? Why should I care if an app gathers some information about the device and stores it somewhere?”
From an enterprise point of view, the answer is quite simple. Any app that behaves maliciously on an employee’s device is a potential security risk. Whether the information is used to attack the device or to prepare for an intrusion from a different angle, it’s a dangerous tool in the hands of an attacker.
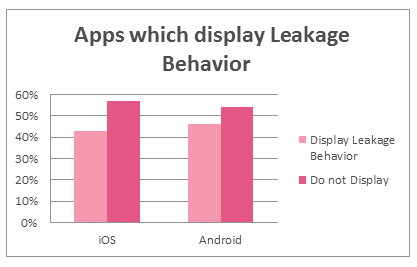
Moreover, many apps leak data from devices. According to research conducted by Check Point of more than 1.5M different apps, up to 43% of iOS and 46% of Android apps leak data. Leaking data can end up in malicious hands, even if the app developers did not intend it.
While some data leaks have become expected and are not very threatening, others can cause severe damage. Therefore, it is important to analyze app behavior to detect which apps are potentially harmful. Even if these aren’t malware, they can be just as damaging to an organization.
That said, app behavior analysis by itself isn’t enough. Many legitimate and widely used apps exhibit malicious behavior. For example, the Facebook app has been criticized for malware-like behavior in the past. So to create a wider and more comprehensive solution, one should analyze not only app behavior but also context.
Policies which ban any app that displays malicious behaviors are not effective, and even less enforceable. Security solutions need to take more threat indicators into account, such as an app developer’s reputation.
Clearly, an app with no reputation, or developed by an anonymous developer is not equivalent to Facebook and shouldn’t be treated the same. Only a comprehensive security solution that provides a holistic view the mobile threats organizations face can keep mobile devices and data safe.
Learn more:
Check Point Mobile Threat Prevention
Learn more:
Schedule a demo of Mobile Threat Prevention
Oren Koriat is a Mobile Information Security Analyst in the Check Point Mobile Threat Prevention Research Group. He is a technology enthusiast and a polyglot, whose expertise is in the field of Asian mobile software markets. Koriat holds a degree in linguistics from Bar Ilan University.