
New Locky Variant Implements Evasion Techniques
Following Check Point’s recent discovery of a new communication scheme implemented by the Locky ransomware, our research teams decided to take a closer look at the inner workings of this new variant and map any new features it introduces.
When Locky first appeared, we thoroughly analyzed its logic, like many other industry researchers. Our analysis showed that while not very sophisticated, Locky is a very efficient malware with a solid functionality and encryption algorithms. Judging by the amount of victim reports and detections generated by Locky in the past month alone, it is safe to say our observation was indeed correct.
Locky’s major drawback is not in its code, but rather in the quick and effective response by the security industry. Many successful security detections, on almost any possible security platform, caused the actors behind Locky to miss out on potential victims, as the malware was blocked from execution or even blocked altogether by internet gateways, not reaching the victim’s computer at all. The changes we observed in this new Locky variant clearly show the Locky creators are very much aware of this fact, and therefore increased their efforts to evade security controls to gain a higher infection rate.
Infection Vector
Unlike previous Locky variants, which were spread mainly via email and documents containing malicious macros, this new variant is spread mainly through the Nuclear exploit kit, making the infection process more efficient while bypassing any email or document security inspections. Using an Exploit Kit for infection makes it much easier to infect victims with Locky, since the malware is delivered to the system using known browser exploits and does not require any user interaction at all.
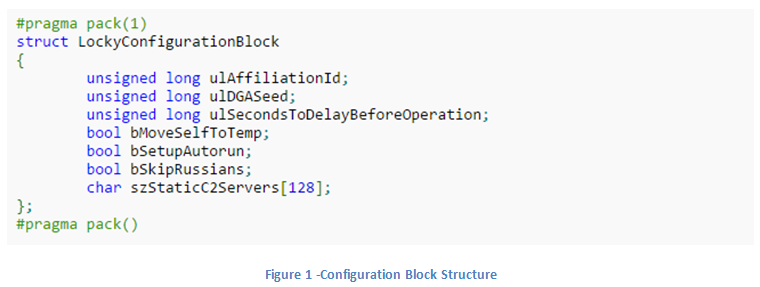
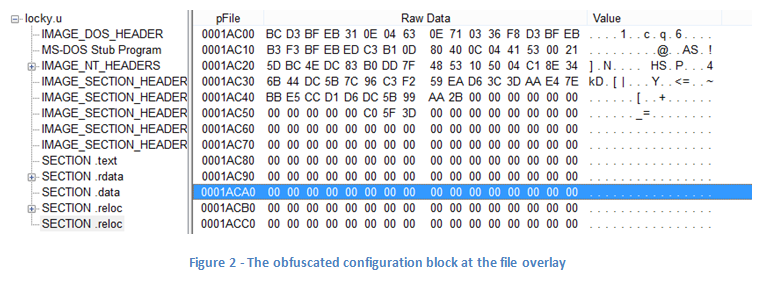
Configuration Block Obfuscation
The previous versions of Locky contained an embedded configuration block. This configuration block contains information about the current sample as well as a list of static C&C server addresses.
Shadow Execution
Prior to execution of any of its original logic, the new Locky variant attempts to place a shadow copy of itself in a newly allocated memory region. It then passes execution to this region by pivoting the process’s stack while deleting the code from the originally allocated memory pages. This technique is probably used to try and avoid common sandboxes, memory detections, or other naive dynamic analysis methods.
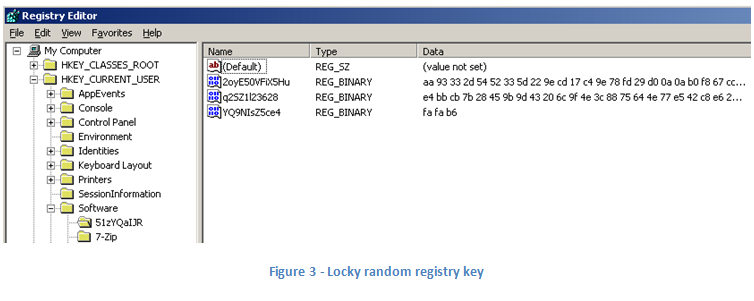
Random Registry Keys
In its previous version, Locky saved its persistent configuration data, including the unique computer ID, public-key, and payment text in the fixed registry key HKCU\Software\Locky. This made it easy to identify Locky with dynamic execution methods by simply looking for the presence of this registry key.
The new Locky variant, however, chooses a random registry key and values (per-host), making it harder to anticipate the exact registry key and values used.
Communication
As detailed in our previous blog post, several changes were made in the new variant’s HTTP communication. These changes reside mostly in the addition of several new HTTP headers, as well as in the change of the main C&C URI. Additionally, as opposed to previous variants, Locky first attempts to use the default system Internet Explorer User-Agent. If Locky fails to retrieve the default user agent value, a hard-coded user agent is used instead. The value of the hardcoded user-agent is: “Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET4.0C; .NET4.0E)”
DGA
The DGA algorithm is the main pillar of Locky’s evasive communication methods. It is responsible for the daily domain generation process, which renders C&C detection almost useless.
The previous Locky variant introduced several changes in its DGA algorithm within its relatively short lifetime. These changes were made either by introducing slight bit-wise changes to the algorithm or by changing the random seed value used by the algorithm. The new variant, however, made more substantial changes to the algorithm with modifications to the DGA algorithm flow and overall behavior. Some of these changes include:
- A change in the possible top-level domains for the generated domains.
The new top-level-domain list contains “ru, info, biz, click, su, work, pl, org, pw and xyz” extensions. - A prolog routine within the DGA algorithm responsible for value calculation has significantly changed from a single iteration to multi-iteration while adding additional XOR operations and constants into its operation.
System Artifacts
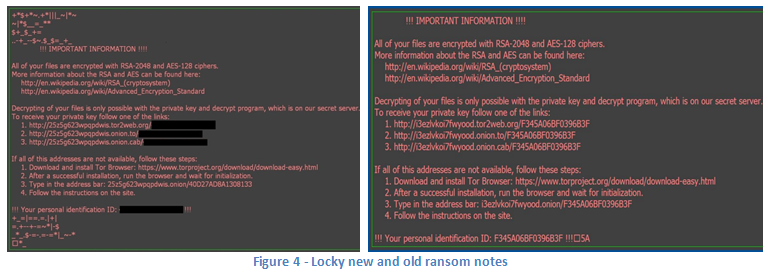
System artifacts are always a key factor used by security vendors to detect the presence of any type of malware. One of Locky’s most famous, consistent and apparent artifacts is the presence of text and image files, which contain the payment and decryption instructions. In previous Locky variants, the file name was “_Locky_recover_instructions”. In the new version, the file name is “HELP_instructions.txt”. This small change may seem irrelevant, but is probably the reason for many missed detections of the new variant.
The message containing payment instructions remains mostly the same.
Conclusion
The new Locky variant was first detected a week prior to the writing of this post and the evasive changes it introduces make its current detection rate much lower than its predecessor. While Check Point’s ThreadCloud has not reported a very large number of detections for this new variant, this can be explained by the sudden shift of infection infrastructure to a new, less-popular exploit kit. Based on the high profit potential it holds, we expect to see many more infections by this new variant in the future.
Detection
Check Point’s customers using SandBlast, IPS blade and Anti-bot products are protected against this new Locky variant.
Indicators of Compromise
| SHA-256 |
| 8f708c299215e2d0e8ce557c96ec771acdbbfffa46a25330caa61fe841e23877 |
| 003d28f180472b832722435d27e216835a8a330f992797006d307f8f14c4a2d3 |
| 2674aebd85c3d0a384edf57c82ef22b3de5fa8aaa1217f80a1d47f71d71ae87d |
| 5780dde27ff31a38c269e763f3648bdabcad25d5db083c43c55502fdefe9f051 |
| 588dfcfe90feaedc724b80919b580e4398f1b8474f5aae979de0e76e7c6c07e4 |
| 64d51aaf4abe4e87013056277277f05c55c6554d2a7005374f254983ac846c4d |
| a2e965cde2b734cc99a8f69ad1a7549ba740c5983a90490f6a3701ca2bca966c |
| a5dc65cbe073898d09d2e07480f430a585cb309316cb4a32e3548b68c7416518 |
| abf1caa982e32c8eb73916083504d42e6851fcbc09772a52e815df0e4fbdcdb5 |
| e608637e38fc964bee96984ed568e5095451787030d6a8f75bf9be8511a91691 |
| f229c3ffa4de0bd43eaf1f7cbad920147982dd79f6032027117e23d5f6369f7e |
| Downloader URLs |
| http://sd[.]alexandrepioto[.]com[.]br |
| http://dev[.]reflexiondeunamujer[.]com[.]ar |
| http://ekotrade[.]pl |
| http://iq[.]loanemperors[.]com[.]au |
| http://our[.]shresthasanjay[.]com.np |
| http://git[.]futvenennumeros[.]com.ve |
| http://goldish[.]dk |
| http://vtdrive[.]kz |
| http://greenellebox[.]com |
| http://downloadroot[.]com |
| http://psxshop[.]hu |
| http://www[.]stopeugenicsnow[.]eu |
| C&C Servers |
| 45.55.192.133 |
| 88.198.119.177 |
| 91.200.14.73 |
| 109.234.35.128 |
| 82.146.37.200 |
| 91.209.77.86 |
| 88.198.119.177 |
| 31.148.99.241 |









