
KOVTER RANSOMWARE – THE EVOLUTION: From Police Scareware to Click Frauds and then to Ransomware
In terms of cyber security research, the Kovter malware family is very interesting. A wide-spread malware found in different parts of the cyber landscape, Kovter underwent extensive changes both in its purpose and in the methods it uses.
During 2013, Kovter acted as a police ransomware. In 2014 and 2015, it conducted “click fraud” attacks. Now in 2016, it’s evolved again. However, this final transition appears hasty, revealing Kovter’s ransomware encryption as relatively simple and easy to break – it’s a quick way for hackers to make “extra” money once a system is infected.
In all of its variations, Kovter retains its legacy capabilities, including listening to the user’s traffic and personal information. Increasingly persistent and difficult to detect, systems can still be compromised by Kovter’s other “features” – even after the victim pays the ransom to recover their files. Constantly evolving evasion techniques, and tools such as corebot, completely change the host’s behavior keeping detection rates relatively low over a long period of time.
Below, we focus on the technical side of Kovter and the different stages of its evolution. Using SandBlast Agent’s forensic signatures, we analyze Kovter’s behaviors and its ability to completely switch technologies.
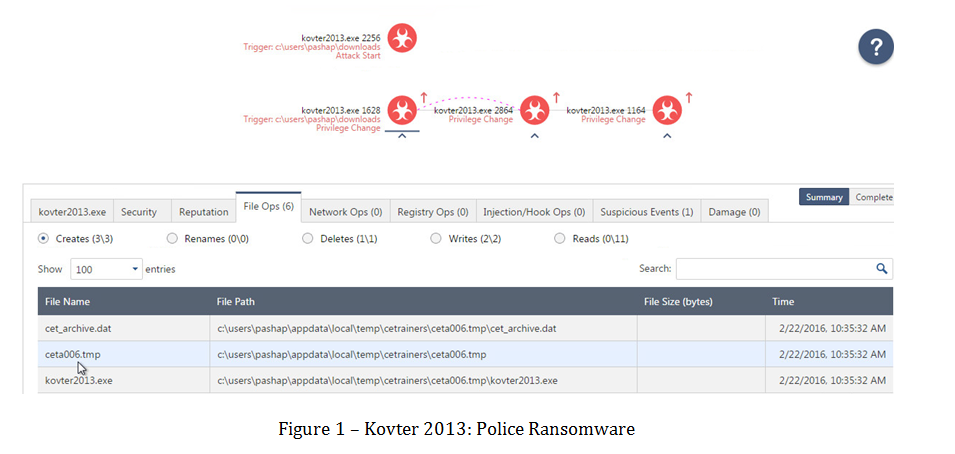
Kovter 2013: Police Ransomware
During 2013, Kovter acted as a police ransomware –remaining on the device, listening to the user’s traffic, “waiting” for something to happen. Once a user enters their account credentials or uses file sharing applications to download unsolicited files, Kovter pops up a message stating the user violated the law, demanding they pay a fine. This activity requires a lot of time – and may never occur, and Kovter can still be detected before it manages to fulfill its intention. Technically, Kovter uses a polymorphic executable that persists in the infected machine, learning the user’s activity through observation. The following SandBlast Agent forensic report shows Kovter’s activity.
Kovter 2014: New Business – Click frauds
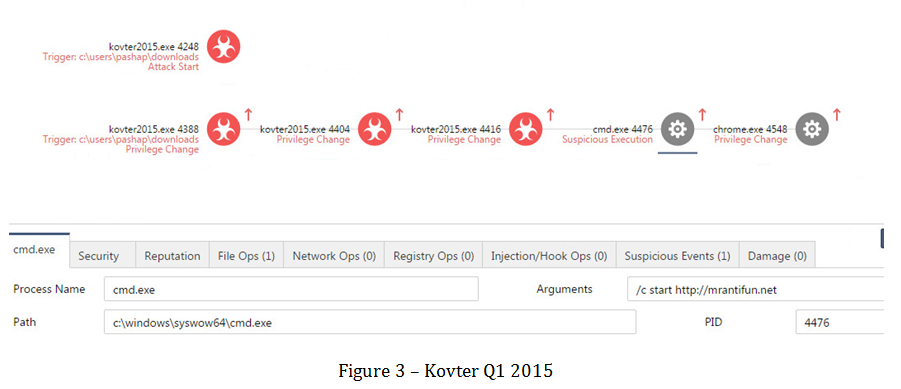
Similar to the 2013 version but with a different goal, Kovter 2014 calls different instances to evade detection. While watching traffic, Kovter 2014 performs click fraud from the user’s machine.
Strangely, it uses cmd.exe to call domain MrAntiFun.net –a non-registered domain sharing information on how to cheat in on-line gaming. This site remains very much alive, even today.
When called in this way, Windows will actually start the default browser. In the case below, Chrome.exe is started, and it finds data regarding the infected computer and its location. The following figure describes Kovter’s activity:
Kovter 2015 – Becoming Fileless
In the middle of 2015 a completely new version of Kovter appeared using the same techniques as those used by the very first detected script malware Poweliks.
Kovter launches an almost fileless registry resident version:
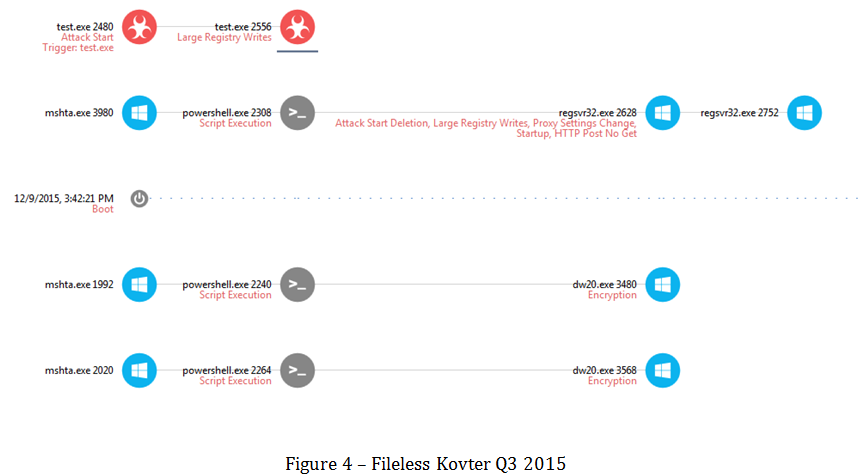
Infiltration, penetration, reconnaissance, persistence across boots and exfiltration are all achieved by storing data on registry. Kovter 2015 uses registry keys and PowerShell, mshta.exe, and dw20.exe to execute without a single file on the disk.
Only Windows executables are part of the attack chain. There are no “private” executables or simple Indicators of Compromise (IOC). Registry keys used for persistence are completely polymorphic and hard to detect by a signature-based system. The goal for the attack could be either click fraud or scareware.
These samples initiate calls to Microsoft registered domains, in addition to private low reputation IPs located in Russia reversed as mailer.teplokomfortvam.ru. It calls the IPs: 78.24.220.229/upload.php, apparently for data exfiltration. Needless to say, these sites are still alive after almost a year.
Kovter 2016: Ransomware
In the past few months of 2016, we saw another shift – Kovter delivering ransomware.
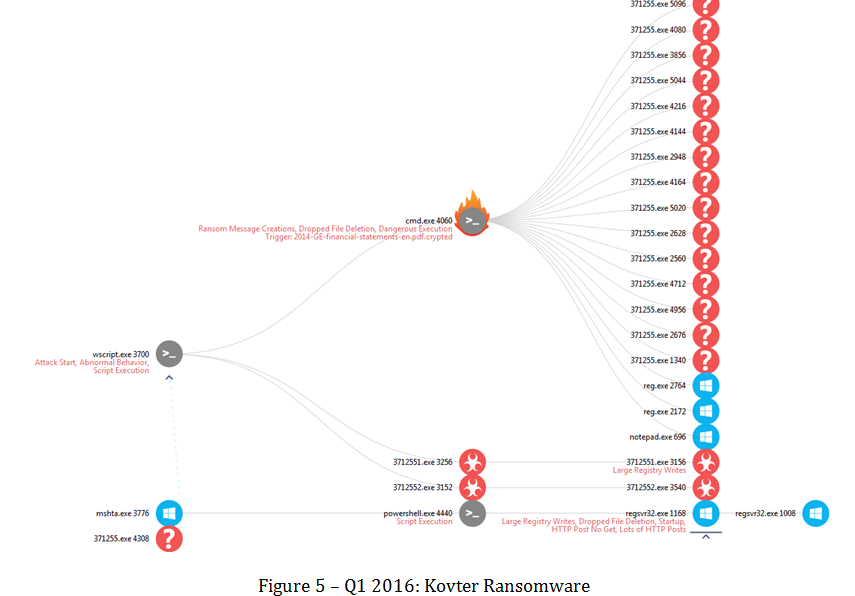
As a ransomware, Kovter chooses a slightly different approach than other ransomware, investing much more effort in evasion rather than in the encryption itself.
By obfuscating only the first part of the file, the ransomware quickly “encrypts” the majority of the files it finds interesting. The first bytes of a file, serving as a magic number to encapsulate the file format, are always encrypted, meaning you won’t be able to open the file as you usually do.
However, the key used to encrypt is local, making Kovter’s encryption very easy to break.
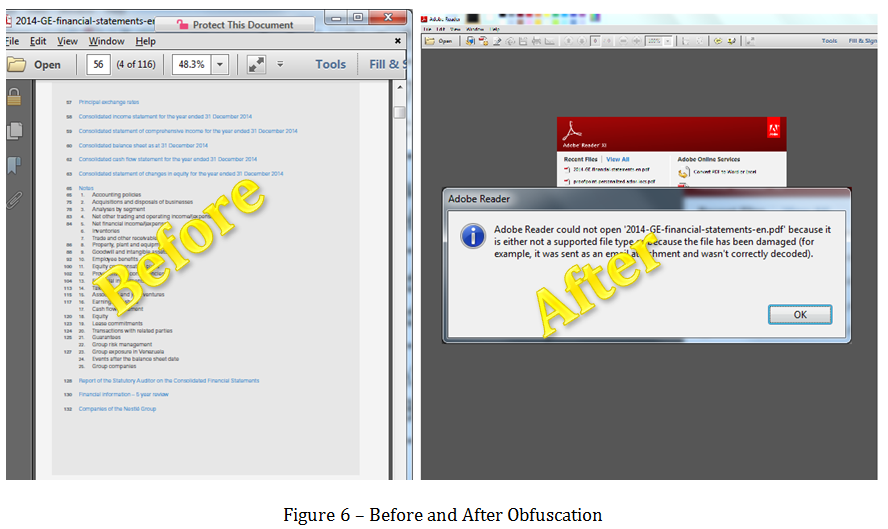
When using a text comparison editor, we can see that only the beginning of the file was changed.

The red part of the picture is the original file; the yellow part is the obfuscation. After that, both files remain exactly the same.
These tricks for evasion are fascinating in their simplicity and high level of success:
- Using cmd.exe script for directory traversal, it looks for files to encrypt. This is the most common way for directory traversal, so this activity doesn’t raise any suspicion.
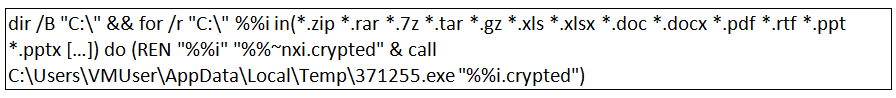
This translates into:
- Create a list of all the files of interest in drive c:\
- Rename each of them to [filename].crypted
- Call 371255.exe with file name as a parameter. Call exe actually does the obfuscation
- Add persistence registry keys
- Display the ransom letter as a text file using notepad.exe
This encryption is done for every drive letter, including network shares that the user has writing permissions for.
As an evasion technique, 371255.exe always uses a different size and md5. Even simpler and more effective is Kovter’s usage of parameters. If the first parameter is a file name, 371255.exe encrypts the file. Otherwise, it doesn’t do anything. For this specific sample, the virus total detection rate when first seen was 2/57 vendors.
The scary part of the report is the lower part, reminding us that this is still Kovter, and it will take additional action:
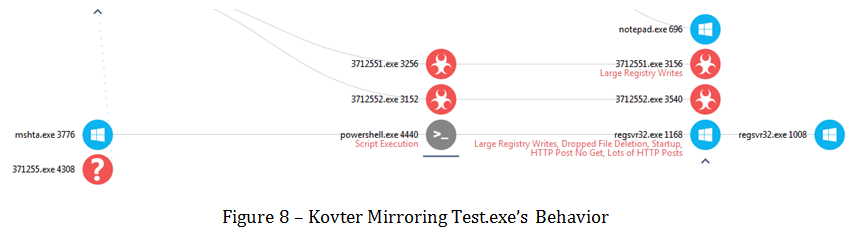
3712551.exe behaves exactly as test.exe did in the previous example. Installing a fileless attack using the registry to persist and execute, it injects code into other applications.
The network operations remain similar as well:
178.33.69.66/upload.php
66.192.173.11/
A huge list of ~700 network addresses as seen in Appendix 1 are contacted, unblocked and undetected.
Evolution is the Key to Survival
Kovter has changed significantly over time. Although different samples have different goals and use alternate techniques, some traits remain consistent across all samples. All of Kovter’s variations emphasize evasion. There is no doubt Kovter will continue to evolve, but we will be there –understanding the next evolution and protecting you from infection.
To learn more about how you can understand, detect, and defend your organization against ransomware, register for our Evolution of Crypto Attacks webcast on May 11th.
Appendix 1 – Network addresses being contacted by Kovter sample from 2016
| 50.7.56.91 | |
| 43.1.91.197 | |
| 84.237.242.132 | |
| 102.126.138.17 | |
| 214.183.121.64 | |
| 13.43.232.149 | |
| 178.33.69.66 | |
| 66-192-173-11.static.twtelecom.net | 66.192.173.11 |
| 178.109.98.143 | |
| 55.105.222.27 | |
| generic-host.mmcs.army.mil | 143.69.138.131 |
| 152.26.132.216 | |
| 41.163.139.83 | |
| 12.78.195.76 | |
| a8.96.33a9.ip4.static.sl-reverse.com | 169.51.150.168 |
| 64-8-202-55.client.dsl.net | 64.8.202.55 |
| a104-98-200-15.deploy.static.akamaitechnologies.com | 104.98.200.15 |
| net-188-153-184-22.cust.dsl.teletu.it | 188.153.184.22 |
| 205.160.187.162 | |
| 215.227.63.44 | |
| ip-89-102-116-34.net.upcbroadband.cz | 89.102.116.34 |
| 27.14.252.13 | |
| 76.60.89.35 | |
| user-38lcj5t.dialup.mindspring.com | 209.86.76.189 |
| 167.190.39.70 | |
| nothing.attdns.com | 135.54.92.29 |
| 61.125.142.134 | |
| 99-118-12-51.lightspeed.gnvlsc.sbcglobal.net | 99.118.12.51 |
| 19.180.121.230 | |
| 160.255.27.65 | |
| 59.41.223.254 | |
| mk-66-62.mk.psu.edu | 146.186.66.62 |
| 214.97.128.10 | |
| 42.253.216.229 | |
| 46.93.97.70 | |
| 115.243.179.178 | |
| hsi-kbw-5-56-215-148.hsi17.kabel-badenwuerttemberg.de | 5.56.215.148 |
| 29.47.211.197 | |
| 141.126.45.95 | |
| pc167h176.vscht.cz | 147.33.167.176 |
| 101.221.181.224 | |
| 35.181.131.94 | |
| 49.211.178.128 | |
| 65-125-113-11.dia.static.qwest.net | 65.125.113.11 |
| 69.27.108.12 | |
| 137.145.10.111 | |
| rdn-culidor01.vpn.ne.qinip.net | 195.18.112.140 |
| 155.west-palm-beach-07rh16rt-08rh15rt.fl.dial-access.att.net | 12.78.14.155 |
| 105-237-153-151.access.mtnbusiness.co.za | 105.237.153.151 |
| 56.154.232.96 | |
| 30.33.195.27 | |
| 46.235.131.177 | |
| 1cust5295.an3.nyc41.da.uu.net | 63.24.180.175 |
| 1.86.191.252 | |
| 220.198.79.95 | |
| 159.72.68.152 | |
| 94.205.161.244 | |
| 176.153.169.67 | |
| c-73-244-13-59.hsd1.fl.comcast.net | 73.244.13.59 |
| cpe-98-25-8-68.sc.res.rr.com | 98.25.8.68 |
| 95.84.82.132 | |
| 134.130.159.185 | |
| 90.6.8.109.rev.sfr.net | 109.8.6.90 |
| 145.161.early-registration.of.surfnet.invalid | 145.161.59.169 |
| 55.35.149.132 | |
| 42.50.156.96 | |
| accc0ac2.ipt.aol.com | 172.204.10.194 |
| 185.9.84.229 | |
| p4FE81EE7.dip0.t-ipconnect.de | 79.232.30.231 |
| 67-41-140-220.hlrn.qwest.net | 67.41.140.220 |
| 49.255.41.224 |









