
Zcrypt: The Ransomware Virus Hybrid
A recent piece of ransomware has emerged that is causing quite the stir. The reason – it is in fact a virus and can infect users even through USB devices. The technology itself is not new, but when implemented by ransomware the results could be severe. Given this, now is a good time for people that are not running port protection software to disable automatic execution.
Using the Check Point SandBlast Agent automatic forensic analysis, we were able to reveal further details about this new strain of ransomware. Zcrypt manages to infect users through USBs by creating autorun.inf and automatically launching a file called “invoice.exe” when the USB key is plugged in. Zcrypt displays different behavioral patterns than most ransomware we have encountered so far. It does not delete shadow copies or its own executable, and does not perform directory traversal when looking for files to encrypt. To accomplish this, it first uses the registry shell folder description to find folders of interest, without querying the file system itself, and then it watches for changes to the file system, encrypting any new file that is added or changed in the system.
In addition, it writes using a DLL file (dynamic-link library), which is a type of a shared library; meaning it contains files that can be used by multiple programs simultaneously. While the malware executable was reported by various security vendors, the DLL file appears to be clean according to VirusTotal. To unpack the DLL file, Zcrypt uses NSIS (Nullsoft Scriptable Install System), a well-known process widely used by legitimate applications as well. To unpack the DLL, the initial malware executes a copy of itself and loads the DLL dynamically from the initial calling process, creating a very wide execution tree, which is hard to follow. The DLL is deleted immediately after usage and created again as many times as required. This process can was repeated more than ~1000 times.
A Greedy Ransomware
Zcrypt overrides the targeted files twice. First it corrupts them and then it encrypts them. This is done to prevent the users’ ability to use disk recovery tools. This extra step makes it much stronger than deleting shadow copies. Zcrypt does not stop after it encrypts all existing files. It goes even further and monitors any file changes and encrypts any new file the user creates. This means that even if the user gives up on his files he still cannot use his computer until the malware is completely removed. Any new file will be encrypted within a few seconds.
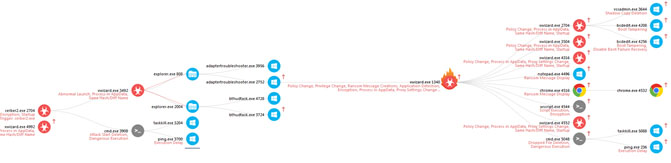
Figure 1: Zcrypt SandBlast Agent Forensic Analysis
The above image displays the malware’s flow of operation, from the initial infection via a USB drive to the actual encryption of the files. All of the samples we analyzed used the same C&C server, located in the Netherlands.
Combining The Old And The New
Zcrypt is a great example of implementing old tactics in new vehicles. The creators of this ransomware did not have to invent the wheel; they simply used old ones on a new car. Most of the techniques used by Zcrypt clearly point to a new emerging ransomware trend, also used by others like CryptXXX, which has learned from the previous trend of what techniques detectors use By straying away from the “traditional” course of action used by ransomware, Zcrypt was able to evade tools targeting their common traits. We will probably be seeing more examples for such usages in the future, as security vendors invest more and more in stopping the ransomware epidemic.









