
Tales from the Trenches: Modern Malware Requires Modern Investigation Techniques
The Check Point Incidence Response team was called in to assist a company who suffered a severe breach in their network, which was not previously protected by Check Point’s advanced protections. The team began to investigate and was extremely impressed by the malware’s tactics and sophisticated evasion techniques. The malware’s evasive nature required the team to use state-of-the-art investigation techniques to successfully remediate the network.
How it all began – inviting the malware in
The breach originated in a keygen downloaded by one of the employees. While the keygen did actually work, it also contained a malicious component – the malware called Gatak.
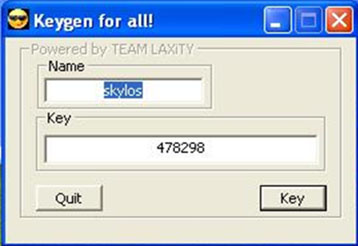
Figure 1: The Keygen Downloaded By The User
Gatak is a Trojan infostealer, designed to infiltrate into an organization’s network and exfiltrate as much information as possible. Gatak was not only bundled inside a benign application, it was also packed and obfuscated to bypass security measures undetected.
The malware goes even further to sidestep security measures through the use of some tenacious evasion techniques. First, the malware conducts several actions to evade VMs by monitoring the cursor movement. If the malware detects too many movements or none at all, it terminates its operation. Additionally, the malware checks if security tools are installed on the machine and terminates its operations if it finds any.
The malware also consists of several components, each of which is downloaded only after the previous step has been executed successfully. This helps the malware stay hidden, since each component draws less attention when executed on its own. In addition, even if one component is detected, the rest of the operation can go on unharmed, while the malware’s aim remains concealed.
Gatak receives commands through payloads hidden inside images. This advanced technique is called steganography and is extremely hard to detect. The actual commands are encrypted and embedded into the image data and decrypted by the malware after they are downloaded from legitimate image storage sites.
The malware managed to spread throughout the network before any red flags were raised. What finally sounded the alarm was when the company’s personnel detected a strange activity – all of the computers in the network were contacting a single IP address in Australia. At this point was when they reached out to the Check Point Incidence Response Team, which was happy to help.
Help arrived!
The team began its operation by setting a plan, removing the outdated protections installed on computers and deploying the next-generation controls based on real-time behavioral analysis. Since all of the computers were infected, the team installed SandBlast Agent on all end points. SandBlast’s automatic forensic analysis was able to detect the malware’s execution flow, as seen in figure 2 below.
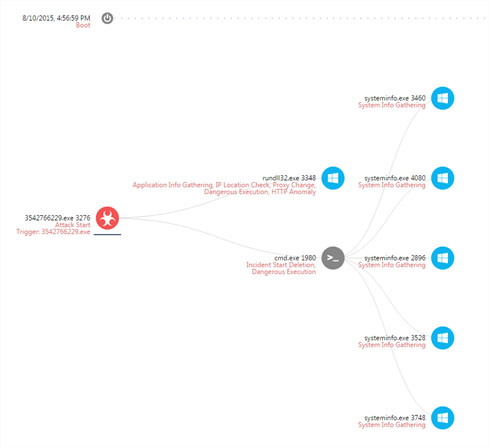
Figure 2: Gatak Forensic Analysis Report
Several key attack chain activities helped us quickly identify the malware:
The malware repeatedly attempted to communicate with the same C&C server, as seen in figure 3 below. In addition, it displayed a repeated behavior through creating a copy of itself, executing a network command, and using ping to check its connectivity. In the remediation process, the team also discovered that the company’s infrastructure was for sale on the Dark Web and that the domain had been compromised.
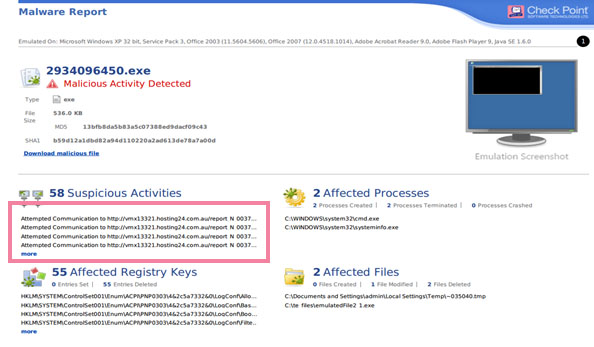
Figure 3: Malware Communication
Takeaways from the attack
There are a few major points which enabled the attack that are worth highlighting. First, as is often the case, the cause of the breach was the user. Users tend to be the weakest link in the security of a network. To combat this, organizations should use advanced threat prevention solutions, which eliminate the need for extensive user education. Second, the network was flat, meaning any user (and malware) could access any place within it. This allowed the malware to spread laterally without hindrances. Network managers should make sure their network is segmented and implement appropriate user access control. Third, no advanced protections were implemented on the network and the archaic protections were no match for the complex malware that attacked it. To stay protected, users must keep up with the swift pace of evolving threats by using the latest protections, capable of blocking both known and unknown threats. Lastly, network administrators should be prepared for the possibility that a malware manages to slip through protections by having a response and remediation plan ready, one equipped with the appropriate security tools to assist them in case of a breach.









