Cerber Ransomware Targets U.S., Turkey and the UK in Two Waves
New ransomware families appear on a regular basis, each with a different method of operation. The Cerber ransomware, which has a sophisticated implementation process, uses a very interesting tactic in its attacks. It operates in surges with relatively low activity in between them.
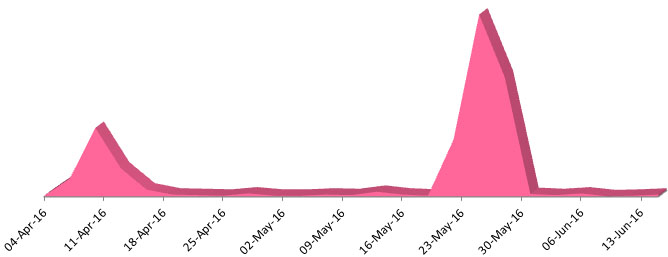
We have detected two such spikes in Cerber’s activity, the first in April and the second in May, each accumulating a substantial amount of victims, as seen in figure 1 below.
Figure 1: Cerber Attacks per Day
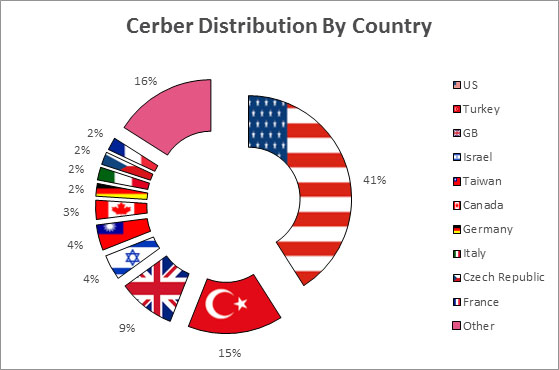
Cerber targeted users in large numbers mainly in the U.S., Turkey and Great Britain, but also a wide array of other countries in smaller amounts.
Figure 2: Cerber Distribution by Country
Similar to the Locky ransomware, it spreads via phishing emails, which contain malicious attachments. Once the user opens the attachment, they become engaged in a social engineering scheme, persuading them to activate the embedded macro commands that allows the malware in.
Cerber displays a “classical” ransomware behavior. It creates a copy of itself in many different locations and communicates to them with different parameters. It launches its attack by using Windows binaries without any parameters. This is done by injecting code into explorer.exe and calling the following Windows apps:
- adaptertroubleshooter.exe.
- bthudtask.exe, a task meant to uninstall a Bluetooth device, often associated with malware.
Cerber then uses another common tactic, loading a DLL (Dynamic Link Library), which is a type of a shared library; meaning it contains files that can be used by multiple programs simultaneously. Once the encryption begins, Cerber makes sure to erase the shadow copies to prevent file recovery. Additionally, it tampers with the boot process to make sure the user has no way to recover their files. The files are encrypted with the AES-265 and RSA encryption method, which is currently unbreakable.
Cerber presents its ransomware message using Notepad and Google Chrome. Another common feature used by Cerber is its self-deletion at the end of the process. To ensure persistency, Cerber initiates a watchdog preventing any uninstall attempt. Cerber also starts a network search, calling a very long series of IP addresses mostly located in France.
The entire execution of Cerber is displayed below, as seen in SandBlast Agent’s forensic analysis report:
Figure 3: Cerber Execution Tree
We have no doubt that we will continue to see spikes in Cerber’s activity. Check Point users are protected against this threat (Trojan-Ransom.Win32.Cerber; Trojan-Ransom.Win32.Zerber) by SandBlast Agent and Check Point’s Antivirus and Anti-Bot software blades.