From HummingBad to Worse: New In-Depth Details and Analysis of the HummingBad Android Malware Campaign
For five months, Check Point mobile threat researchers had unprecedented access to the inner-workings of Yingmob, a group of Chinese cyber criminals behind the HummingBad malware campaign. HummingBad is a malware Check Point discovered in February 2016 that establishes a persistent rootkit on Android devices, generates fraudulent ad revenue, and installs additional fraudulent apps.
Yingmob runs alongside a legitimate Chinese advertising analytics company, sharing its resources and technology. The group is highly organized with 25 employees that staff four separate groups responsible for developing HummingBad’s malicious components.
Download our report “From HummingBad to Worse” to learn more about the research team’s findings.
Other research firms have associated Yingmob with an iOS malware called Yispecter, but the evidence Check Point researchers found confirms the same group is also behind HummingBad:
- Yispecter uses Yingmob’s enterprise certificates to install itself on devices
- HummingBad and Yispecter share C&C server addresses
- HummingBad repositories contain QVOD documentation, an iOS porn player targeted by Yispecter
- Both install fraudulent apps to gain revenue
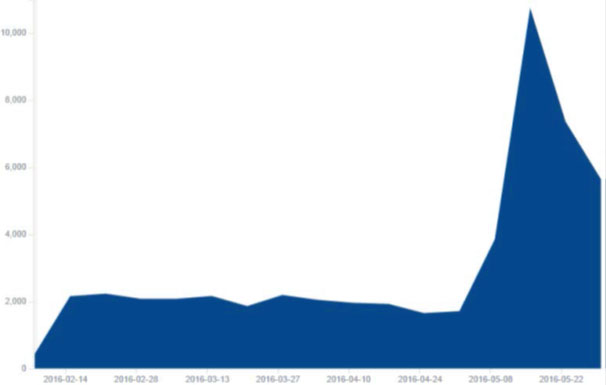
Figure 1: Number of HummingBad instances seen in the wild
Yingmob uses HummingBad to control 10 million devices globally and generate $300,000 per month in fraudulent ad revenue. This steady stream of cash, coupled with a focused organizational structure, proves cyber criminals can easily become financially self-sufficient.
Emboldened by this independence, Yingmob and groups like it can focus on honing their skill sets to take malware campaigns in entirely new directions, a trend Check Point researchers believe will escalate. For example, groups can pool device resources to create powerful botnets, they can create databases of devices to conduct highly-targeted attacks, or they can build new streams of revenue by selling access to devices under their control to the highest bidder.
Without the ability to detect and stop suspicious behavior, these millions of Android devices and the data on them remain exposed.
Learn more about Check Point Mobile Threat Prevention, the solution that first discovered the HummingBad malware. Schedule a demo today.