Jigsaw Ransomware Decryption
The Jigsaw ransomware was first spotted in April 2016, and has since received a bit of traction. It became infamous thanks to an image of the Jigsaw killer from the movie ‘Saw’ displayed on the ransom note (hence its name), and its unique way of persuading victims to comply – if payments aren’t made within an hour, Jigsaw starts deleting files from the infected machine.
While investigating the latest Jigsaw Ransomware variant (SHA256: 61AA800584B170FFE9959ACD057CCAF784BF3088E1D3AAB39D07C0793F6C03DF) and its false claims to steal users’ credentials and Skype history, we came across the mechanism the ransomware uses to check whether payments have been made.
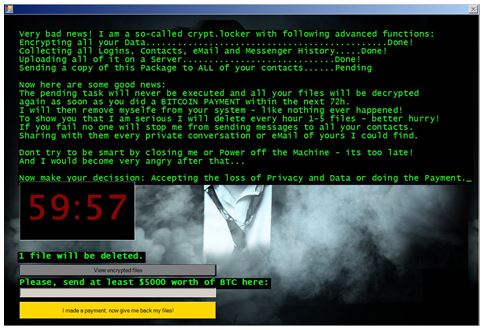
Jigsaw provides the user with a convenient GUI:
When the user presses the “I made a payment, now give me back my files!” button, the program makes an HTTP GET request to:
btc.blockr[.]io/api/v1/address/balance/<bitcoin-account>
and as a response, gets the following json:
{“status”:”success”,”data”:{“address”:”<bitcoin-account>”,”balance”:0,”balance_multisig”:0},”code”:200,”message”:””}.
This got us thinking – what if we change the request, so it queries a different account? Perhaps one that holds the necessary amount of Bitcoins to decrypt our files? Or even better- what if we change the response to say we have the necessary amount?
So we did.
And it worked.
By changing the variable “balance” in the response from 0 to 10, the ransomware believes the payment was made, and starts the process of decrypting the files and removing itself from the victim’s computer.
This simple remedy seems to work on older Jigsaw ransomware variants as well, and leaves no trace of the malware on the infected machine.
The decryption tool which was developed based on the above findings can be downloaded here
User manual –
- Unpack the JPS.zip file.
- In the Jigsaw Puzzle Solver folder, right click ‘JPS.exe’ and click ‘run as administrator’.
- Follow the instructions displayed on the screen.