Ransomware: what you need to know
In recent years, there has been a surge of ransomware attacks. It’s been reported all over security blogs, tech websites and in the news. Unfortunately, these attacks show no signs of slowing. If anything, they are getting worse.
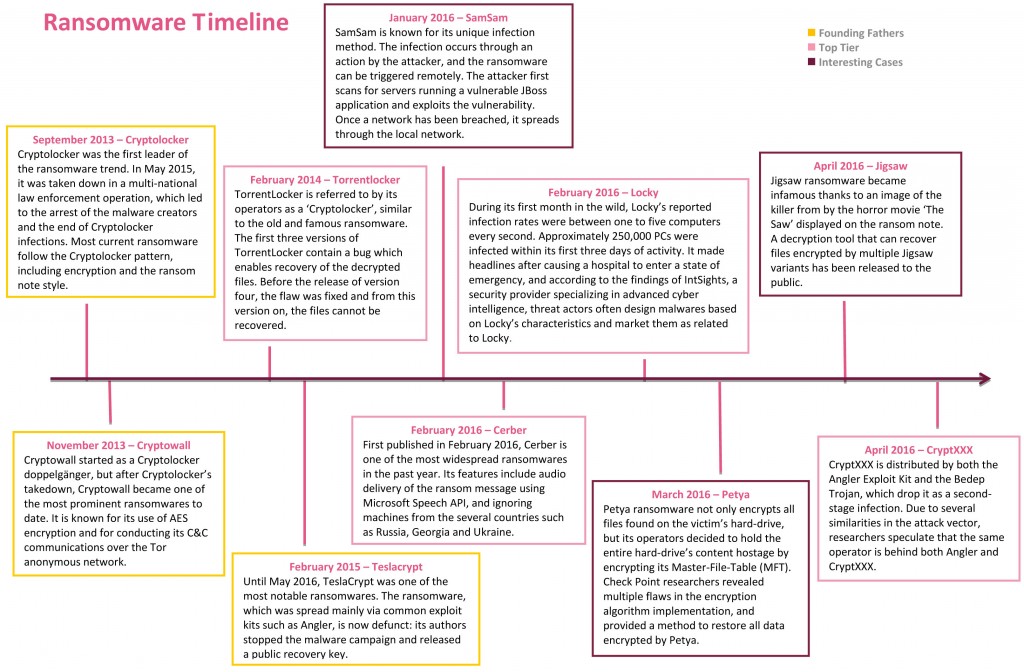
Cryptolocker, the first famous ransomware, was observed in the wild in 2013. From then until mid-2015, there were only a few active ransomware variants and their infection methods were limited. Some of these variants were even weak enough that it was possible to decrypt files without paying ransom.
While quite a lot of variants have been created since then, many of them either don’t effectively infect users or run a low profile campaign. A good example is TeslaCrypt, an infamous ransomware whose authors released a master key for anyone to use. In other cases, new ransomware variants – even ones that are widely distributed and constantly make headlines – are quickly found to have bugs when it comes to implementing the encryption itself, such as the recently published decryption tool for Jigsaw ransomware. These flaws are either fixed in a newer version or the ransomware is abandoned.
There seems to be a fairly large difference between the top-tier of ransomware, which usually maintain several active campaigns, and trendy new ransomware variants that come and go. In our report, Ransomware: What You Need to Know, we provide an overview of the evolving world of ransomware, highlighting the differences between the most prevalent ransomware families, and present several smaller yet unique ransomware variants. We also present several methods for protection and mitigation.
(click on image to enlarge timeline)
How to protect yourself
We highly recommend you take the following steps to protect yourself from ransomware, or at least mitigate its effects:
- Backup your most important files – Make an offline copy of your files on an external device and an online cloud stage service. Note: external devices should be used for backup ONLY and be disconnected immediately after the backup is completed.
- Exercise caution – Don’t open e-mails you don’t expect to receive, and if you are asked to run macros on an Office file DON’T! The only situation in which you should run macros is in the rare case that you know exactly what those macros will do. Additionally, keep track of the latest major malware campaigns to ensure that you do not fall victim to a new unique phishing technique or download a malicious app.
- Have a comprehensive, up-to-date, security solution – High quality security solutions and products protect you from a variety of malware types and attack vectors. Check Point Sandblast Zero-Day Protection efficiently detects and blocks ransomware samples, and extracts malicious content from files delivered by spam and phishing campaigns.