CerberRing: An In-Depth Exposé on Cerber Ransomware-as-a-Service
Check Point researchers have uncovered the sophisticated infrastructure of Cerber, a Ransomware-as-a-Service, including the business model and money trail. For the full CerberRing Report click here.
The ransomware epidemic continues to rage on, encrypting files of private and enterprise users alike. Ransomware has become a global problem. According to the FBI, the accumulated revenue in the first three months of 2016 was over $209 million. One question that naturally arises is – where does all this money go?
In some cases, the operation is run by a single attacker, with the malware developer also serving as the distributor and the only one to profit from the campaign. However, the growing ransomware-as-a-service (RaaS) trend operates differently. The malware developer recruits affiliates who spread the malware in return for a percentage of the profits. This tactic allows the malware to achieve a wider reach and generate greater revenue. More importantly, it enables non-technical actors to take part in the highly profitable business and run independent campaigns, using a set of assigned Command and Control (C&C) servers and a convenient control panel.
Until now, the ransomware-as-a-service industry remained an uncharted region of cybercrime. Very little was known about the operation of such franchises, making it harder for defenders to trace them effectively. In research conducted by Check Point and IntSights, we shed new light on the Cerber ransomware, one of the most prominent ransomware variants. Our report, CerberRing: An In-Depth Exposé on Cerber Ransomware-as-a-Service, discloses not only the technical details of the operation, but also the franchise’s business operation from end-to-end.
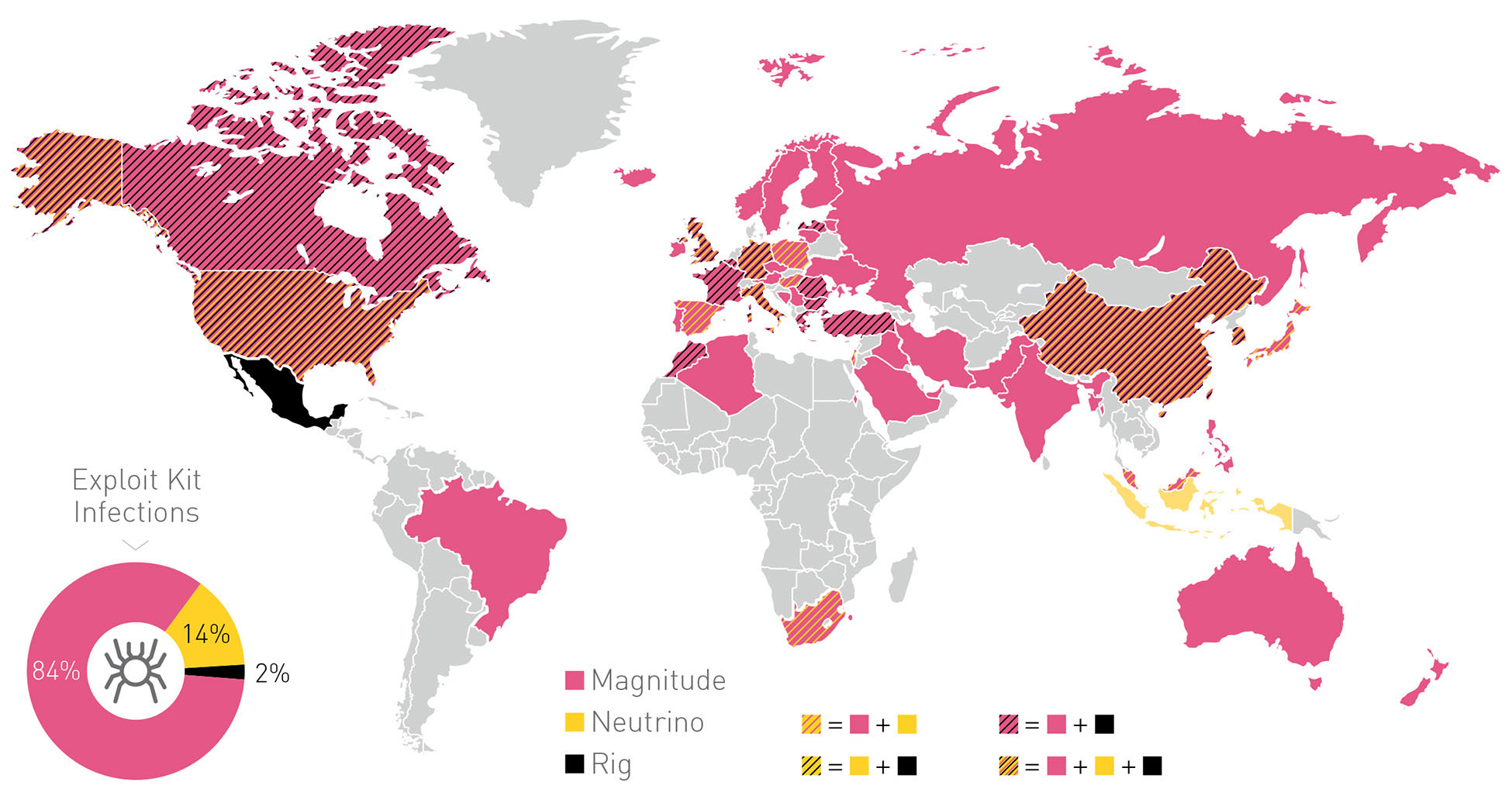
Cerber has a wide distribution, due in part to its successful use of leading exploit kits. By monitoring the actual C&C communications, we were able to create a complete view of the ransomware’s activity. Cerber is currently running 161 active campaigns, launching an average of eight new campaigns daily, which have successfully infected approximately 150,000 users worldwide in 201 countries and territories in the past month alone.
Exploit Kit Country Distribution Map
Perhaps the most intriguing aspect of the Cerber RaaS is its money flow. Cerber uses Bitcoin currency to evade tracing, and creates a unique Bitcoin wallet to receive funds from each of its victims. Upon paying the ransom (usually 1 Bitcoin, which is currently worth approximately $590), the victim receives the decryption key. The payment is transferred to the malware developer through a mixing service, which involves tens of thousands of Bitcoin wallets, making it almost impossible to track the transactions individually. At the end of the mixing process, the money reaches the developer and the affiliates receive their percentage.
By monitoring the data provided by the C&C servers, we were able to identify actual victim wallets, allowing us to effectively monitor payments and transactions involving each of these wallets. Our research also allowed us to track the actual revenue gained by the malware, as well as the path of financial transactions.
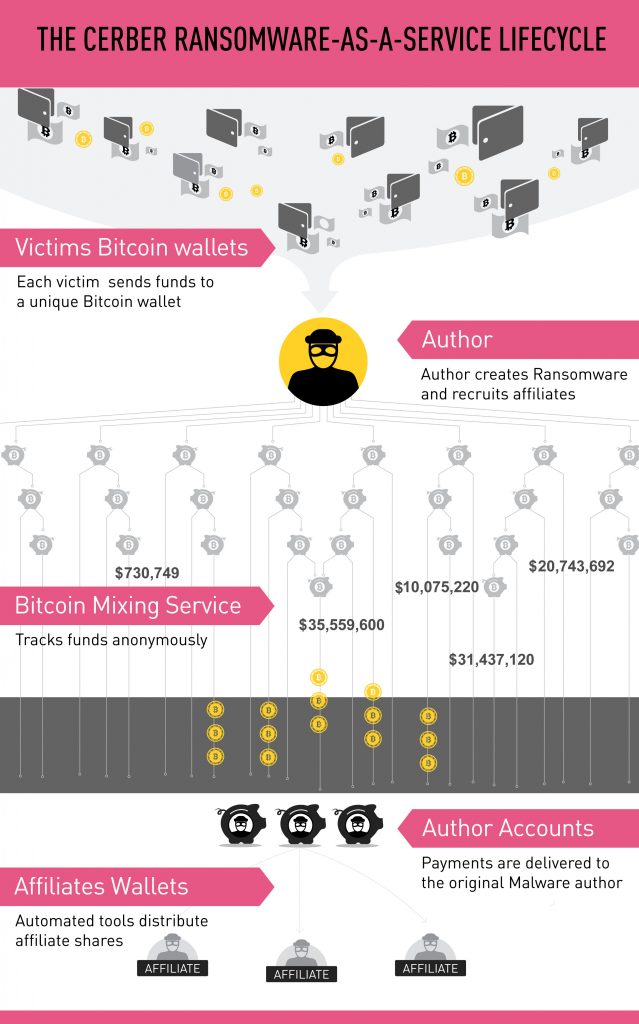
The overall profit made by these Cerber RaaS campaigns in July 2016 was $195,000. The malware developer received approximately $78,000 and the rest was split between the affiliates, based on the amount of successful infections and ransom payments each campaign achieved. On an annual basis, the ransomware author’s estimated take is $946,000 – a hefty sum with few direct costs.
For more information about Cerber ransomware visit www.checkpoint.com/resources/cerberring.
Check Point customers are protected from Cerber by the following security technologies:
- SandBlast detects and blocks both known and unknown Cerber variants using Threat Emulation. For more information visit SandBlast Zero-Day Protection.
- The IPS and Antivirus Software Blades block every currently known variant of Cerber. For more information visit IPS Software Blade.
- The Anti-Bot Software Blade detects and blocks any attempt to communicate with Cerber’s C&Cs. For more information visit Anti-Bot Software Blade.