Beware of the Trident Exploits
Researchers from The Citizen Lab at the University of Toronto last week revealed a sophisticated zero-day attack on the iPhone of Ahmed Mansoor, a human rights activist in the United Arab Emirates. The Citizen Lab discovery exposed three zero-day exploits used by “Pegasus,” a lawful interception cyberespionage tool developed by the Israeli-based NSO Group and sold to government agencies. The attack was initiated by a spear phishing SMS sent to Mansoor’s iPhone 6. Had Mansoor clicked the infected link, the exploits would have been activated, jailbreaking his device and installing the Pegasus spyware.
Webinar: Pegasus & Trident – Government-grade Espionage on iOS in the Wild
iOS devices are increasingly targeted by cybercriminals with new, sophisticated ways of stealing sensitive information. Pegasus, a lawful government spyware tool being misused by entities beyond the law enforcement community, and Trident, a series of three iOS exploits cybercriminals use to install Pegasus are the latest examples. Users of iPhone and iPad devices assume their data is secure, but these new threats clearly prove how you and your business can be exposed to significant risk. Join our webinar to learn how threats like this work, what data could be exposed, and how Check Point Mobile Threat Prevention detects and remediates attacks.
>Register for Americas Session on Wednesday, August 31
>Register for Europe Session on Thursday, September 1
Apple introduced a software patch on August 25 to mitigate the three vulnerabilities, which has been named Trident. While these are not the first exploits targeting iOS devices, the combination of three zero-day remote exploits is unique. Each vulnerability has a separate operation and objective:
- CVE-2016-4655 – Leaks information to the attacker, which allows him to calculate the kernel’s location in memory.
- CVE-2016-4656 – A kernel memory corruption vulnerability which allows the attacker to silently jailbreak the device and install the surveillance payload.
- CVE-2016-4657 – Exploits the Safari WebKit to allow the attacker to compromise the device once the victim clicks on the infected link.
Jailbreaking allows attackers to achieve complete control over the device and conduct extensive surveillance, such as making audio recordings, taking screenshots, and monitoring phone calls and SMS messages. The combination of the three vulnerabilities allows the attackers to target remote victims without relying on physical contact or an app installation by the user.
Like previous state-sponsored attacks, such as the Xsser mRAT, which targeted Hong Kong activists using iOS devices, and was discovered by the Check Point research team, Pegasus utilizes the most advanced tactics in the mobile malware world.
Who is at risk?
The Pegasus malware and the Trident exploits are classified as “Intrusion Software” by the Wassenaar Arrangement and a strict export control is imposed by the US Bureau of Industry and Security and the Israeli Defense Export Control Agency. Theoretically, this means that the Pegasus spyware was sold to authorized law enforcement agencies and intelligence organizations to fight criminals and terrorists. In practice, Pegasus was most likely misused, leaked, or sold to other entities beyond the law enforcement community. The recent disclosure of these new vulnerabilities may lead cybercriminals to use the same tactics for corporate espionage.
Can Pegasus and Trident impact other platforms other than iOS?
While the recent discovery unveiled the Pegasus iOS variant, Check Point’s threat intelligence indicates that similar tactics are also possible on Android and BlackBerry devices.
How can an iPhone get infected by Pegasus?
- If the attacker knows the mobile phone number of a target, he can send a link via SMS. Clicking the link will initiate the attack.
- The attacker may post a link over social media or send a spear-phising email. Once the link is clicked, the attack will be initiated.
- The attacker can stage a man-in-the-middle attack over a Wi-Fi® or cellular network. In this scenario, once the user initiates a web browsing session, the attacker can serve the exploit chain, which wouldn’t require clicking a link.
Check Point Mobile Threat Prevention prevents, detects and remediates Pegasus attacks
Check Point Mobile Threat Prevention is designed to manage the complete life-cycle of the Pegasus infection, as well as similar exploits.
Prevention
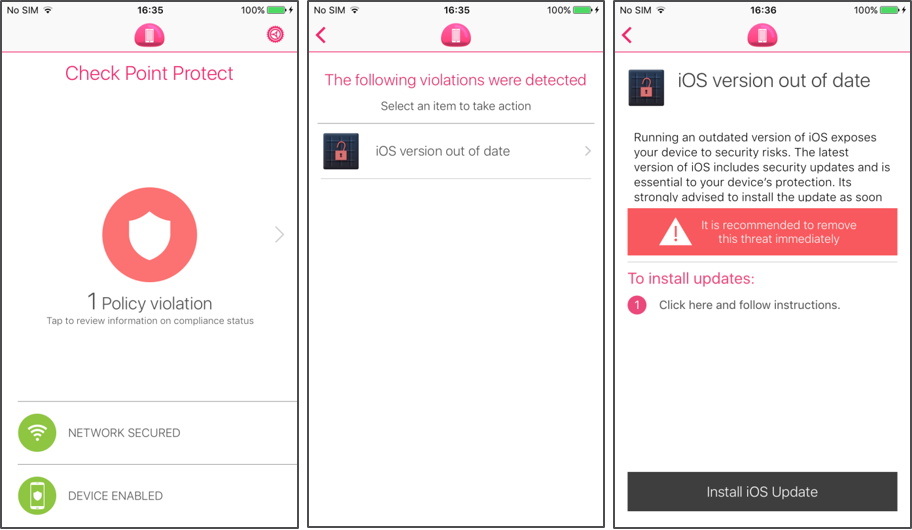
The best way to prevent attackers from using the Trident exploits on devices connected to your enterprise network is to make sure employees update their iOS operating system to 9.3.5. The Mobile Threat Prevention solution assists and guides administrators in patching 100% of the devices throughout an enterprise.
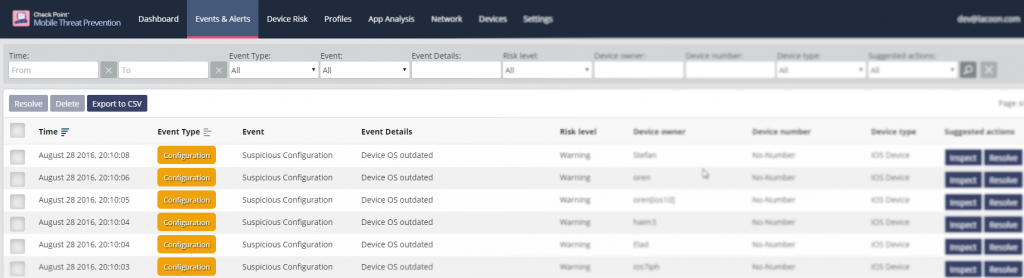
Dashboard reporting
System administrators can view all unpatched devices under the medium risk score. It’s possible to filter the devices with the vulnerable OS version and export the report containing the details of exposed employees. Check Point recommends continuously monitoring the patching progress within your organization and emailing employees with the outdated OS until every device in your organization is updated.
Home screen notification
A notification reminder is pushed to users that have yet to update their iOS version
In-app alert
The Check Point Mobile Threat Prevention app, beginning with version 2.47.2347, which is currently awaiting App Store approval, notifies the user that their device is out of compliance and that it should be updated to the latest iOS version.
Detection
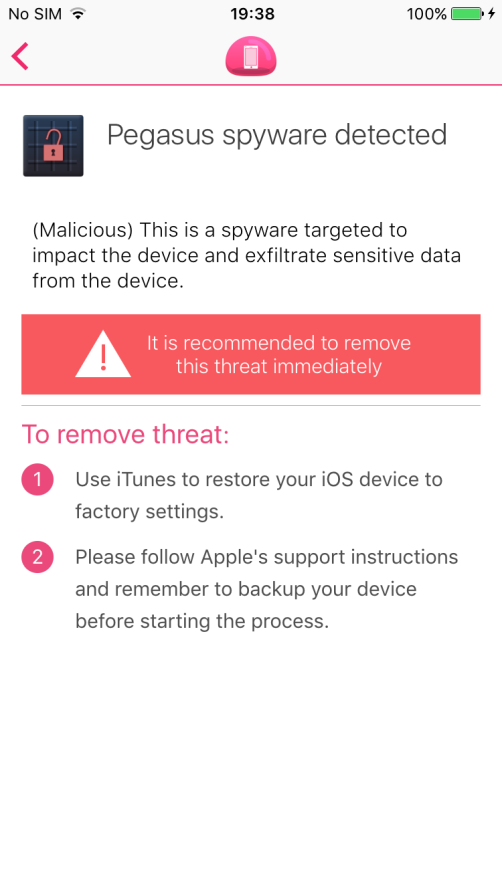
Installation of the Pegasus spyware on an iOS device will be detected by the Check Point Mobile Threat Prevention app and will be reported to the user and the device administrator.
Remediation
Once a mobile device is compromised with the Pegasus malware, the only option for full remediation is a complete re-flush of the operating system.