Check Point Forensics: PokemonGo Ransomware’s Hidden Unexpected User
It was inevitable. Given the popularity of PokemonGo, ransomware developers have already attempted to trick users into downloading malware that claims to be PC versions of the popular mobile game. There are currently already two known ransomware variants that attempt to capitalize on the mobile games popularity by naming their executables pokemongo.exe.
BleepingComputer has already named the first of the discovered ransomware the PokemonGo Ransomware and the second is called DetoxCrypto. In this blog, we will show and describe a SandBlast Agent forensics run of the PokemonGo Ransomware and how it attempts to hide the creation of a new user account called “hack3r”.
Click here to view the PokemonGo Ransomware Interactive Forensics Report. Note: The forensic report is best viewed on screen resolutions greater than 1280 x 768. The ideal browsers to view the report are Chrome and Firefox. However, the report should display correctly in Safari, Internet Explorer 11 and Edge. Older versions of IE will not display the report correctly.
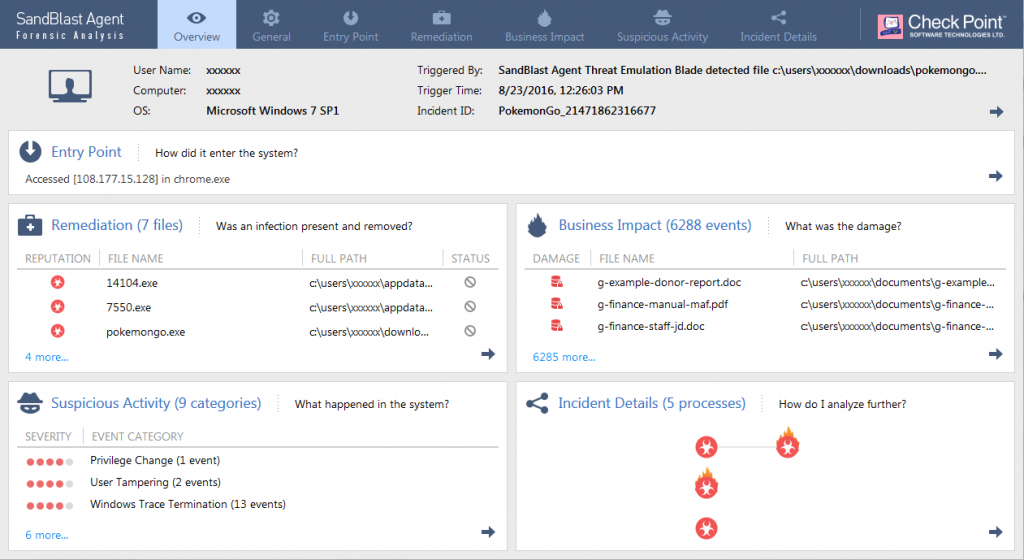
Figure 1: Forensic Analysis Overview. Click to view the interactive report.
BleepingComputer’s analysis of the PokemonGo Ransomware indicates that it is based on the “educational” ransomware Hidden Tear. Figure 2 shows that the ransomware still shows up as Hidden Tear in the Windows Task Manager.
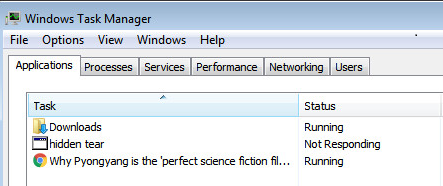
Figure 2: PokemonGo Ransomware’s Hidden Tear Roots Revealed
While one can always debate the rationale for “educational” ransomware given that they can be easily “weaponized”, the truth is that malicious actors can also utilize traditional compression tools like WinRar and WinZip to create ransomware, as shown in our blog Check Point Forensics: CTB-Faker Ransomware.
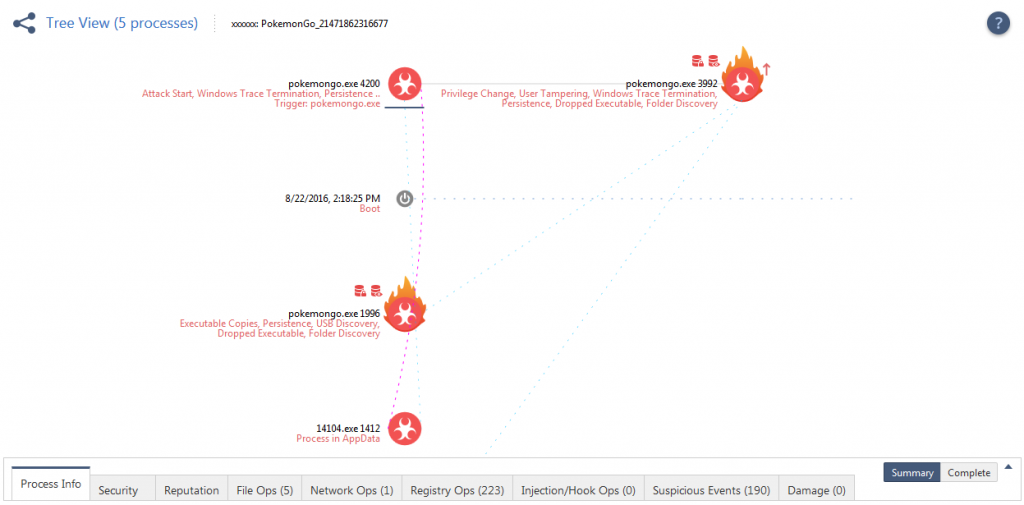
Figure 3: Tree View of the Attack. Click to view the interactive report.
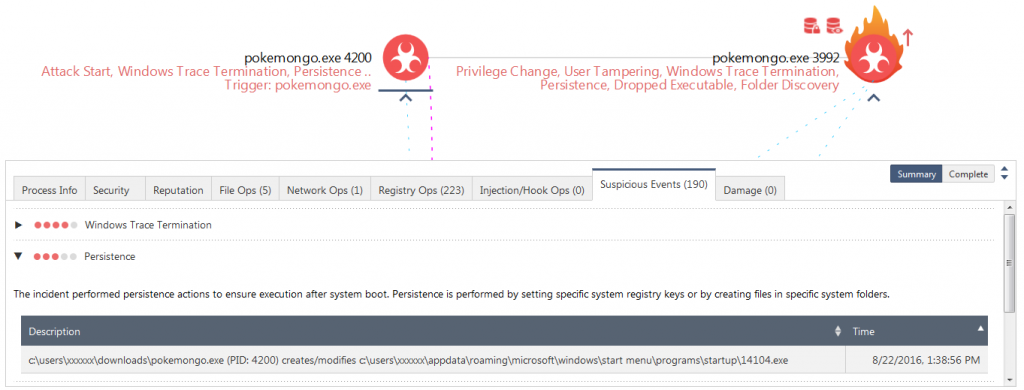
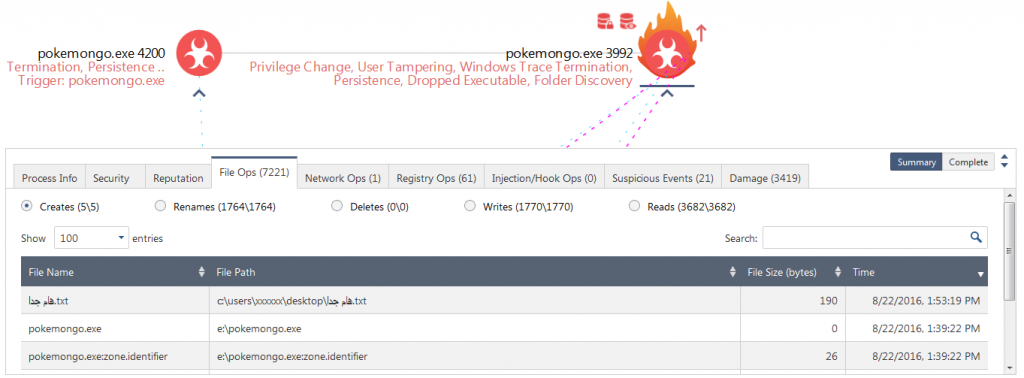
Starting with the analysis of the Tree View on the attack as shown in Figure 3, we see that the pokemongo.exe (PID: 4200) was the first launched executable. It actually creates an executable 14104.exe, which is stored in the windows startup folder in order to run on reboot. This can be seen under the suspicious events for “Persistence” or “Dropped Executable”.
Figure 4: Executable being created in startup folder. Click to view the interactive report.
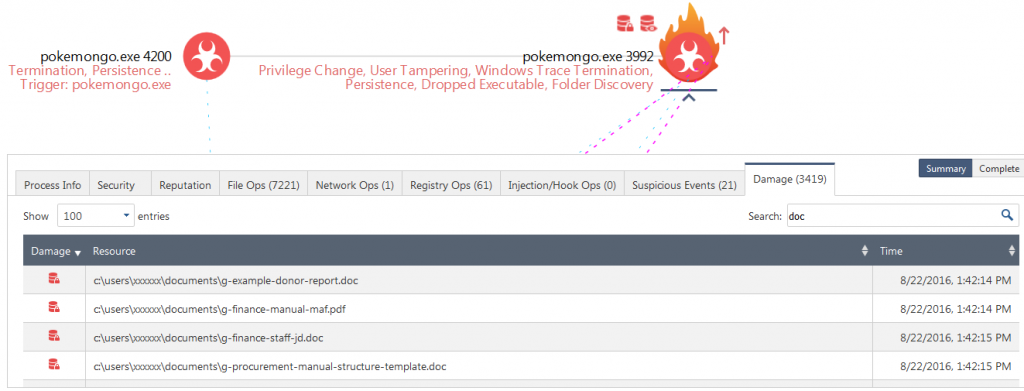
The process pokemongo.exe (PID: 4200) then launches a copy of itself called pokemongo.exe (PID: 3992). It is this process that does the encryption of the users file as can be seen by clicking on the “Damage” tab for the process (Fig. 5).
Figure 5: Docs being encrypted by the ransomware. Click to view the interactive report.
Prior to encrypting the files, the process pokemongo.exe (PID: 3992) also creates a copy of itself to the root of the secondary drive (E:) as shown in Figure 6. This file’s path is added to the Windows registry key (below) in order to maintain persistence. It also creates an executable file called 7550.exe in the Windows Startup folder.
The Windows registry key: “hku\s-1-5-21-1350185060-4047523286-3791768344-1000\software\microsoft\windows\currentversion\run”
Figure 6: Files being created by PID 3992. Click to view the interactive report.
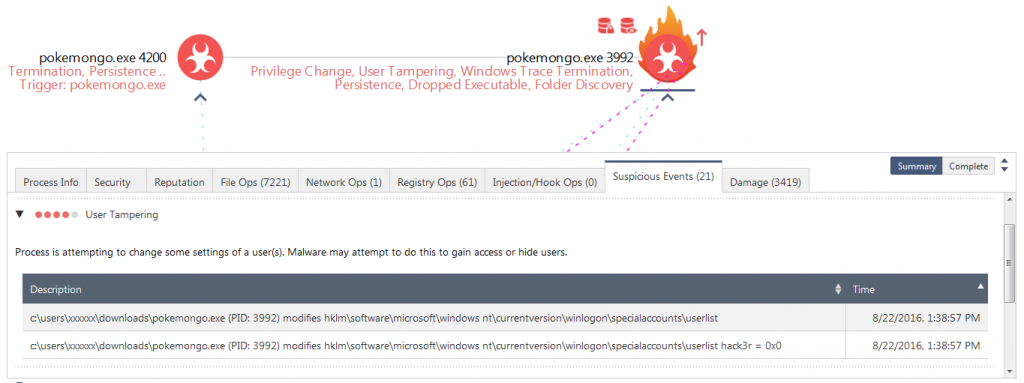
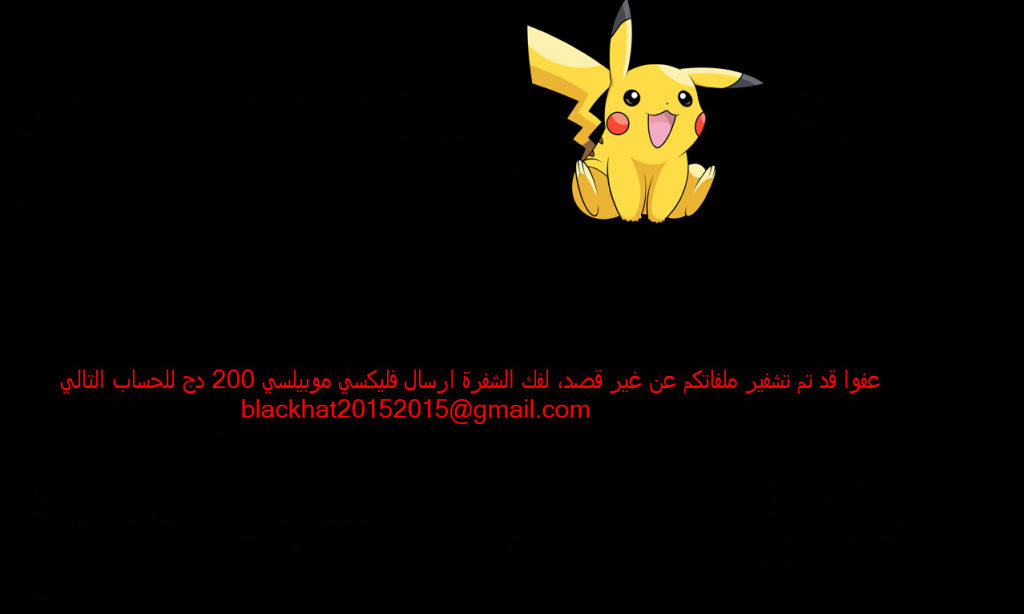
After encryption of the files, the process creates a text file in Arabic, which presumably contains ransom payment information. However, this file is not opened automatically. In addition, a new user called “hack3r” is created on the machine. The user is then removed from the login screen as can be seen in the changes to the registry, shown by the suspicious event “User Tampering” (Figure 7).
Figure 7: User Hack3r being hidden from the login screen. Click to view the interactive report.
We can now analyze the malware behavior on reboot. To recap, prior to the reboot, there were three recorded instances of persistence:
- Windows Startup Folder: c:\users\xxxxxx\appdata\roaming\microsoft\windows\start menu\programs\startup\14104.exe
- Windows Startup Folder: c:\users\xxxxxx\appdata\roaming\microsoft\windows\start menu\programs\startup\7550.exe
- Windows Registry Run Key: hku\s-1-5-21-1350185060-4047523286-3791768344-1000\software\microsoft\windows\currentversion\run pokemongo = E:\PokemonGo.exe
Given this, we would expect to see processes 14104.exe, 7550.exe and pokemongo.exe (located in E) to all start with the reboot of the system. Sure enough scrolling down the graph allows us to see that all three processes did start. What is interesting however is that 14104.exe and 7550.exe are both screensaver executables. They display the real ransom message for the user as shown in Figure 8. Both executables show the same message and in order to stop the screensaver, both have to be terminated.
Figure 8: Ransom Message in Arabic
Lastly, the process pokemongo (PID: 1996) continues to search for new files to potentially encrypt.