
A Complex Web: Bitcoin Mixing Services
Check Point’s Threat Intelligence Analysis team often comes across attackers who seek payment from their victims in Bitcoins – especially following ransomware attacks such as Cerber. Once they get paid for their criminal exploits, these actors employ all sorts of Bitcoin mixers and tumblers to cover their tracks. We decided to analyze these mixing services to achieve a better understanding of their operation methods, in an effort to provide organizations with insights into the complex cybercriminal underworld.
About Bitcoin Mixing Services
Bitcoin is often thought of as a payment method that hides both the sender and the recipient, and makes it impossible to identify the user behind the screen. However, Bitcoin is not anonymous. The user behind an address might be revealed during a transaction[1]. Therefore, it’s the user’s responsibility to safeguard his or her identity while trading within the Bitcoin network. There are a number of methods and practices to protect your privacy[2], but the fact still remains – Bitcoin transactions are not private.
Bitcoin anonymity services (and scams) have been around for almost as long as Bitcoin itself. These services use the Bitcoin network in a clever way, making it very difficult to deduce any information from the Blockchain, while the database keeps a record of the transactions.
The idea is simple: combine one user’s funds with other people’s Bitcoins, thereby obfuscating the trail back to the funds’ original source. In traditional financial systems, it’s equivalent to transferring funds through a series of bank accounts. When you mix Bitcoins, you send your money to (and place your trust with) a mixing service, which sends you another person’s Bitcoins through a series of transactions.[3] Therefore, if someone tries to track your activity through the Blockchain, they must sort through thousands, even millions, of transactions. Each transaction leads to more Bitcoin accounts that act as a relay for the mixing service, passing funds through them on their way to the final designated address. Most importantly, the funds that end up there are untainted and have no link to the original address they came from.
Before We Begin
A couple of points to note:
- It’s impossible to tell if an individual Bitcoin address or transaction is legitimate, belongs to an attacker, or is part of a long chain carried out by a mixing service.
- Instead of sorting through transactions by dates, we looked at related transactions, as they tend to provide a broader view with less hassle.
Guidelines for understanding the graphics:
- The red nodes represent Bitcoin addresses.
- Two nodes connected by a link have shared a transaction. The node that the link points to is the one that received the funds.
- Links marked in orange represent incoming links to the selected node.
Tracking mixing services
The easiest way to track mixing services is to follow the money trail from the infection stage, for example from a ransomware attack, into the seeming disorganization of the mixing service.
Explanation:
Step 1: The attacker’s Bitcoin address (marked in pink- let’s call it L0) received the initial payment from the victim and moves it to the first Bitcoin address in the chain (L1).
Step 2: Following the attacker’s Bitcoin trail, we can see that L1 was in contact with 25 different Bitcoin addresses, making it hard to follow the trail.
Step 3: Following the trail for each Bitcoin address we encountered, we ended up with an enormous bouncing scheme where each Bitcoin Address is in relationship with a random number of other Bitcoin addresses.
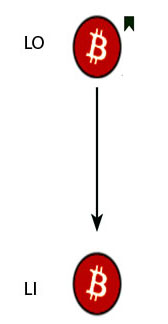
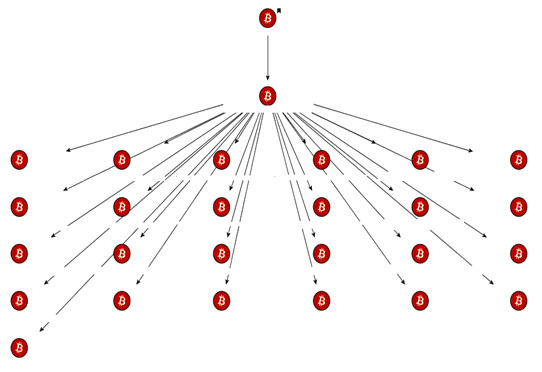
Step 1 Step 2
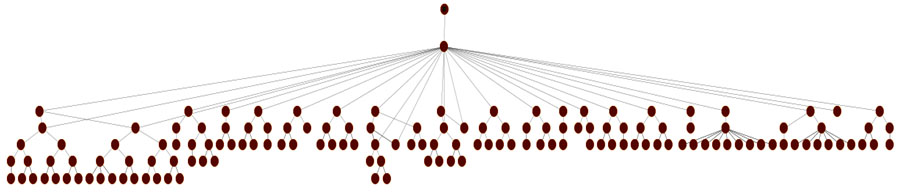
Step 3
At a first glance, these patterns appears to be a mess. After a second look, however, the image becomes clearer and patterns begin to emerge.
Bouncing between pools
All mixing services operate pretty much in the same way, with each service having specific variations. Once the funds are moved from the attacker to the mixing services’ first account (called the mixing service gate), they bounce around to multiple accounts and at some point pass through one or more massive nodes (called pools).
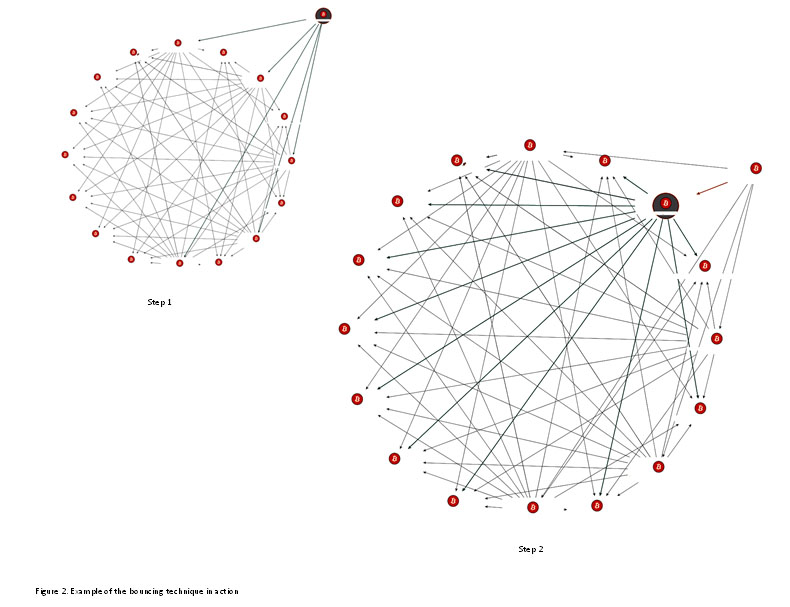
In figure 2, we witness the bouncing technique in action.
Step 1: A control node transfer funds to five other nodes (the bold links).
Step 2: Each of those nodes spreads its funds between additional nodes, which in turn keep this wheel spinning.
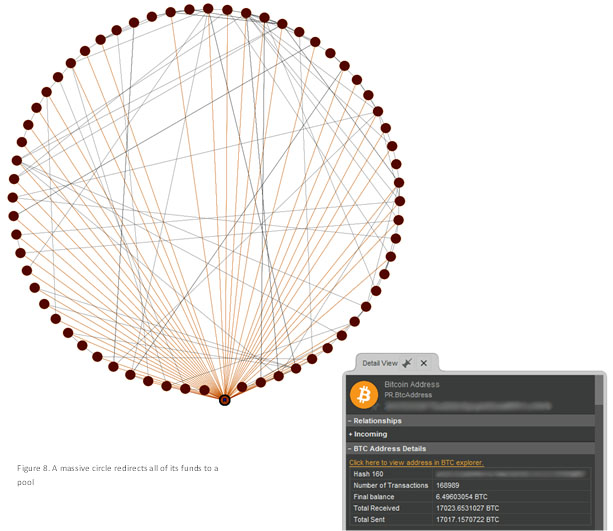
Every now and then we came across pools, massive nodes where large amounts of funds are collected and then redistributed to other smaller nodes, eventually reaching their final destination. Below is an example of a pool. Note the volume of Bitcoins that pass through it over time, indicated by the Total Received and Total Sent.
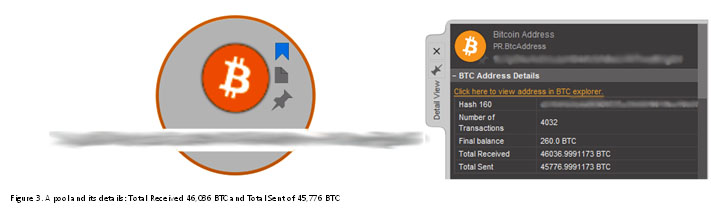

We are able to draw some conclusions from the data.
- The “bouncing” is used to cover the tracks and confuse anyone trying to follow the money trail. Thousands of transactions with thousands of “fresh” Bitcoin accounts are produced.
- The pools increase fungibility (that is, each element is capable of being substituted for another), and they eliminate any link between the attacker’s first account and his last. Funds are swapped between so many different users that any attempts to link accounts are futile.
This is all very nice, but we already knew that mixing services are used by malicious actors and that they employ thousands of transactions and mix funds together. At the end of the blog, we’ll show you some of the techniques we encountered and provide possible explanations for what we’ve seen.
The Tea Party’s Mad Hatter
Just like the Mad Hatter pours his tea with elegance into cups, the mixing service “pours” (distributes) the Bitcoins with ease. The following figures show another technique used by mixing services, which is to “drip” small amounts of Bitcoins into a massive node, and then dump the rest into a new node, which in turn does exactly the same. To continue our cup analogy, it’s as if each cup drips a small portion of their tea into a very large cup, and pours the rest of the tea into the appropriate descendent cup below it.
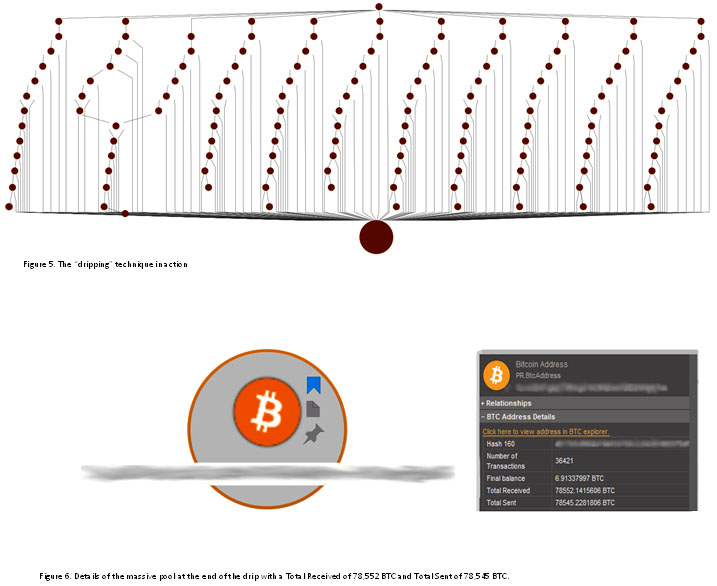
Deciphering the patterns
Using graph analysis on the Blockchain, we found rather quickly that it is better to look for circular relationships. Unlike a ‘tree’ form, where the nodes are placed in different orders, many Bitcoin addresses are in direct relation (received or sent funds) with various addresses from all levels of the tree. For example, a remote node could receive a payment from a massive node three levels above it.
When examining the graph in a circular view, interesting formations appear.
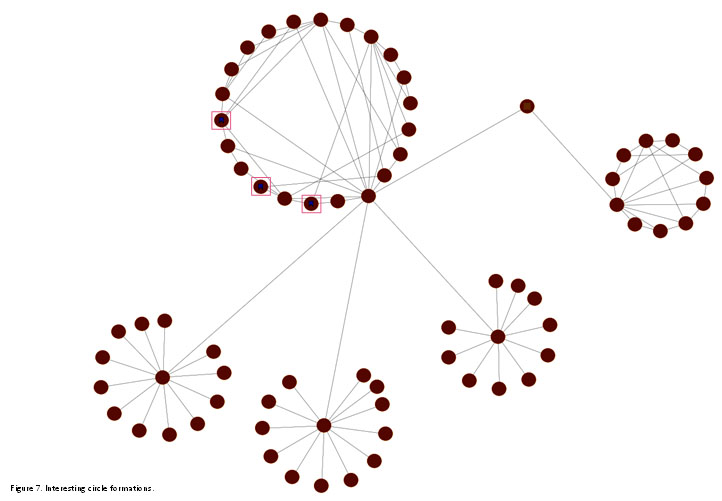
In the above figure, we see two main circles formed from the same node (marked in a blue square). The left circle bounces the received funds between its members, as well as outsourcing some of it to form new circles.
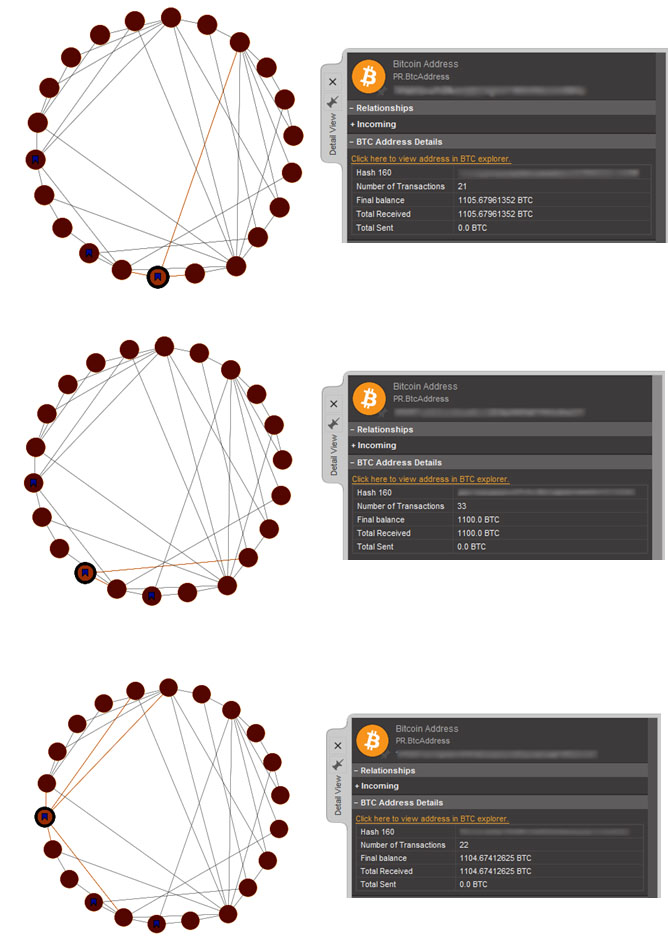
Can you see the three nodes in the upper left circle that are marked with pink squares? These nodes are most likely “Exit nodes” where the funds end up and wait for their owner. The following images show that each of these nodes has been receiving Bitcoins while not sending any.
Another interesting example is the following circle, which eventually directs all of its funds to a single node. This node happens to be a massive pool, as shown in the image below.
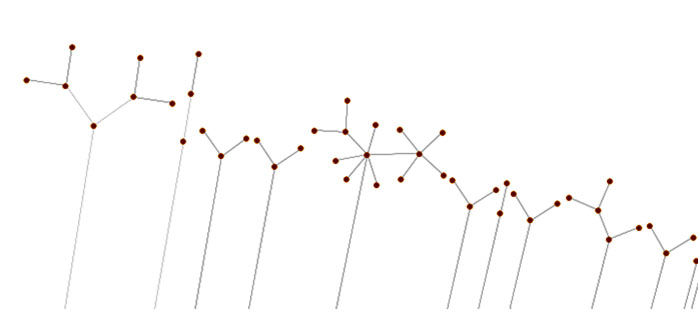
We discovered another pattern that looks closely like a snowflake.
Conclusion
Our goal in this investigation was to analyze the way mixing services operate, to gain an insight into how cybercriminals try to conceal their tracks and avoid identification following receipt of ransoms, or other illegal payments from victims, and when distributing the profits from these exploits. It’s important to note that although mixing services can be used for malicious purposes, they also play an important role in today’s crypto-currency trade. We will continue to investigate the various mixing techniques and welcome questions and feedback on our blog.
[1] https://bitcoin.org/en/you-need-to-know#anonymous
[2] https://bitcoin.org/en/protect-your-privacy
[3] https://en.bitcoin.it/wiki/Mixing_service









