SQL Slammer Comeback
SQL Slammer is a computer worm that first appeared in the wild in January 2003, and caused a denial of service condition on tens of thousands of servers around the world. It did so by overloading Internet objects such as servers and routers with a massive number of network packets within 10 minutes of its first emergence.
The worm exploits a buffer overflow vulnerability in Microsoft SQL Server 2000 or MSDE 2000 by sending a formatted request to UDP port 1434. After the server is infected, it attempts to spread rapidly by sending the same payload to random IP addresses, causing a denial of service condition on its targets. This vulnerability was discovered by David Litchfield several months before Slammer first launched. Accordingly, Microsoft released a patch, but many installations had not been patched before Slammer’s first appearance.
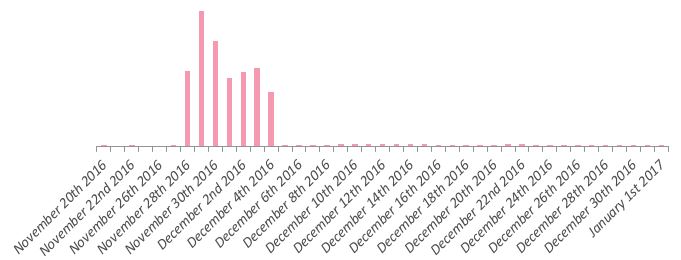
Now, more than a decade later, Slammer is hitting again. During a routine analysis of global data collected by Check Point ThreatCloud, we detected a massive increase in the number of attack attempts between November 28 and December 4, 2016, making the SQL Slammer worm one of the top malware detected in this timeframe:
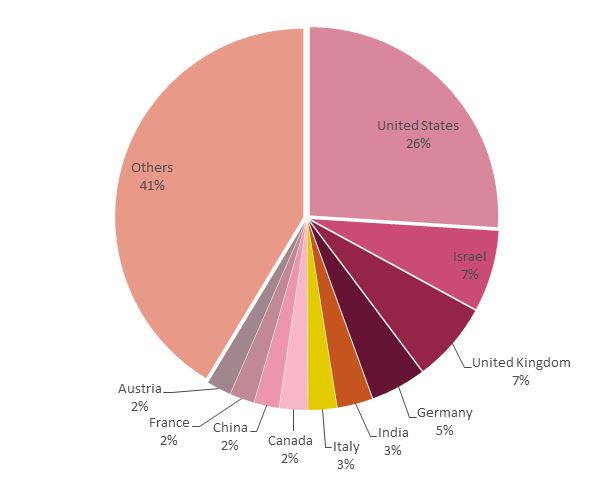
The attack attempts detected by Check Point were directed to a large variety of destination countries (172 countries in total), with 26% of the attacks being towards networks in the United States. This indicates a wide wave of attacks rather than a targeted one.
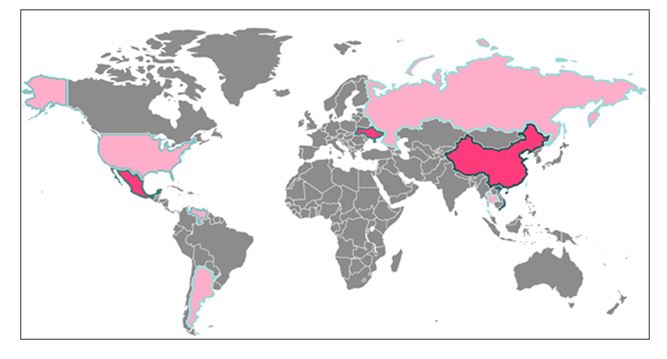
The IP addresses that initiated the largest number of attack attempts related to the Slammer worm are registered in China, Vietnam, Mexico, and Ukraine, as shown:
To summarize, although the Slammer worm was primarily spread during 2003, and has barely been observed in the wild over the last decade, the massive spike in propagation attempts that was observed in our data leads us to wonder – is the worm trying to make a comeback?