Merry X-Mas Ransomware Decryption Tool
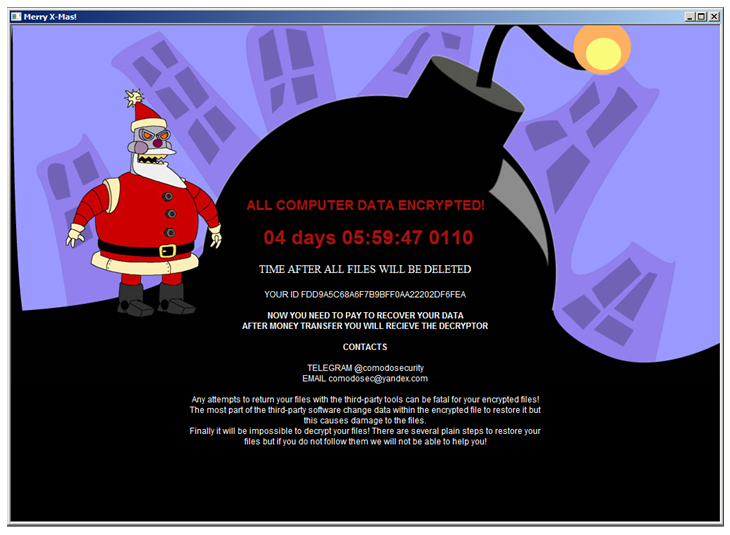
Merry X-Mas is a ransomware that was first spotted in the wild on January 3, 2017. Upon successful infection, the ransomware encrypts victims’ files and presents a “Merry Christmas” ransom note with a holiday-themed design and a demand for payment to regain access to the files.
The malware was first distributed through a spam campaign which claimed to be from the Federal Trade Commission. When the victim clicked the link in the email, it caused a zipped file with the extension pdf.exe to download. Disguised as a legitimate PDF file, this was actually the Merry X-Mas dropper.
The malware’s second attack wave came a few days later on January 8, with a similar spam campaign. This time itwas in the form of a court attendance notice with a link that downloaded a zipped Word document with a malicious macro. This campaign also spread an additional malware dubbed DiamondFox. This malware is an info-stealer capable of stealing credentials or credit card data, and may also be leveraged for synchronized Distributed Denial of Service (DDoS) attacks as part of a larger botnet.
The Merry X-Mas ransomware contacts a hardcoded malware server. If a response fails to arrive, the malware uses a hardcoded key to encrypt the victim’s files. The ransomware can encrypt both the file content and name. When a file is encrypted, its file extension is changed to one of the following unique extensions – ‘.PEGS1’, ‘.MRCR1’, ‘.RARE1’, ‘.MERRY’ or ‘.RMCM1’. If enabled by the attacker, the ransomware also encrypts shared network resources.
When the encryption process is complete, an HTA (html-based) file named ‘YOUR_FILES_ARE_DEAD.HTA’ or ‘MERRY_I_LOVE_YOU_BRUCE.HTA’ with the ransom note is dropped in every folder which contains encrypted files.
The Check Point Malware Research team conducted an investigation of the ransomware’s encryption process. Based on our findings, we were able to develop a decryption tool which can help victims recover their lost data free of charge.
The decryption tool can be downloaded here.MXM_Decryptor
To use the decryption tool:
- Download the tool.
- Press the Decrypt button.
- In the pop-up dialogue box, confirm the start of the decryption process.
- The decryption process begins.
- Wait until you receive confirmation that the decryption is complete.
- Access your recovered files.
Check Point is an Associate Partner of the No More Ransom (NMR) project, which aims to fight back against the ransomware epidemic. Our new decryption tools will be available for public use.