Is Malware Hiding in Your Resume? Vulnerability in LinkedIn Messenger Would Have Allowed Malicious File Transfer
The popular business social network LinkedIn has accumulated over 500 million members across 200 countries worldwide. Whether you’re a manager seeking to expand your team or a graduate on the job hunt, LinkedIn is the go-to place to expand your professional network.
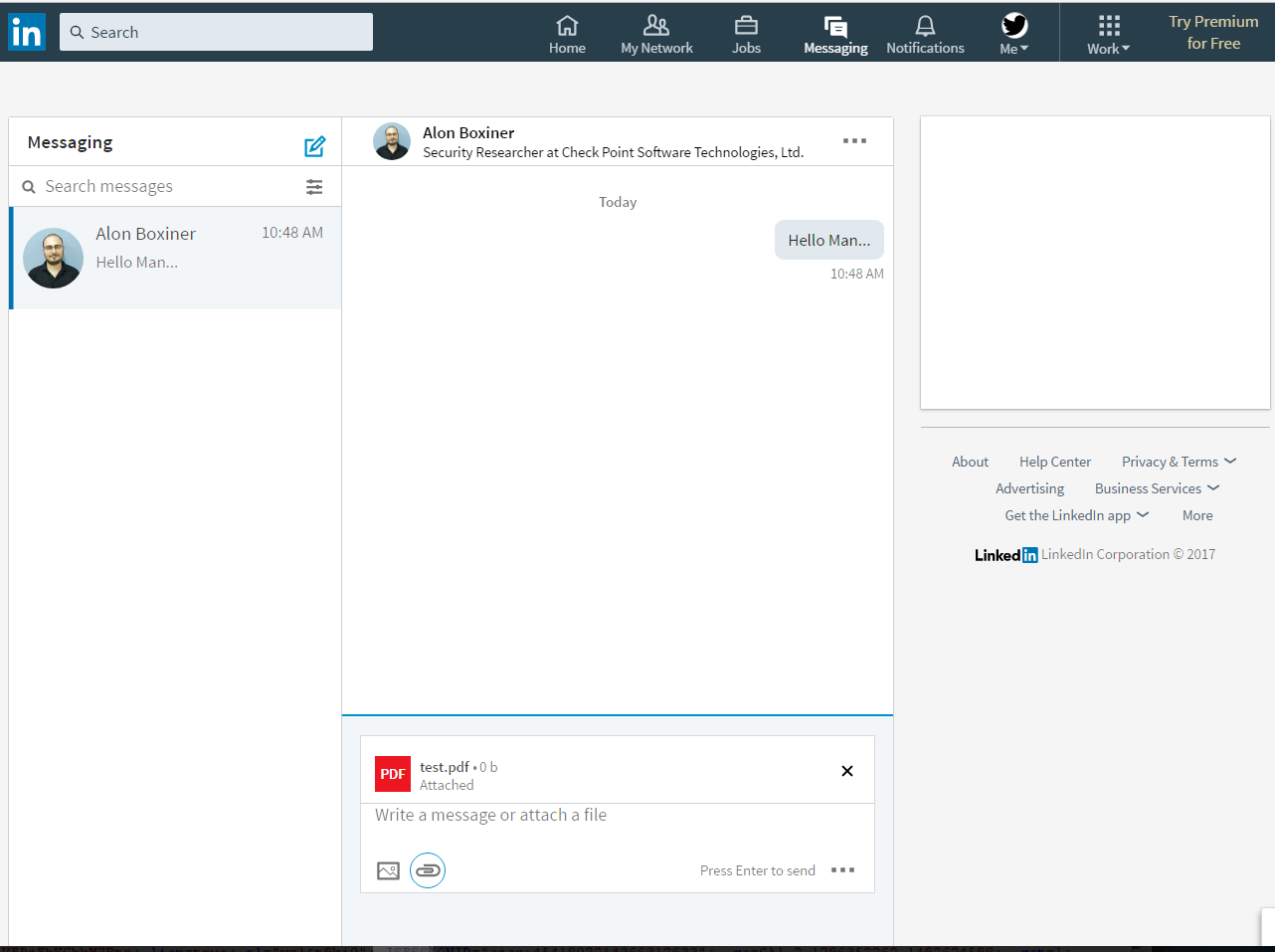
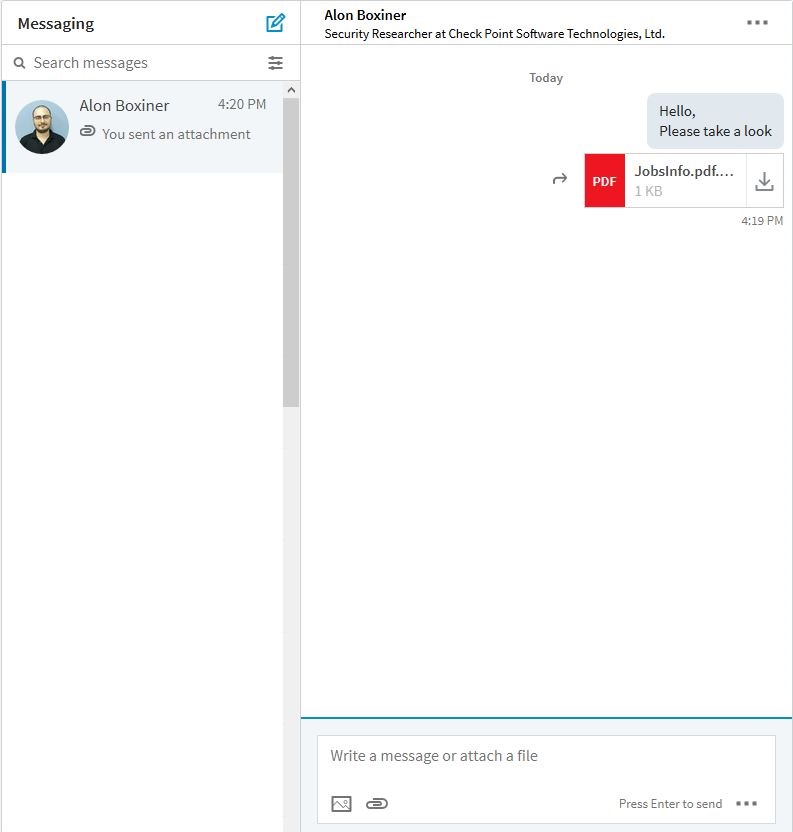
As the world’s largest professional network, LinkedIn has acquired a noteworthy reputation. Individuals utilize the site to seek out trustworthy business connections and job opportunities. The most used feature on the site is the messenger platform. It enables users to easily send resumes, transfer academic research and share job descriptions. Users open messages under the assumption that the information is safe, secure and sent by a user with good intentions. Unfortunately, this trusting assumption can sometimes be abused. Check Point researchers discovered a vulnerability within LinkedIn’s messenger platform, that if exploited would enable attackers to spread malicious files.
In an effort to protect users, LinkedIn restricts the file types that can be sent via messenger, allowing only the following file extensions to be uploaded and attached within a message:
- Documents – csv, xls, xlsx, doc, docx, ppt, pptx, pdf, txt.
- Images– gif, jpeg, jpg, png.
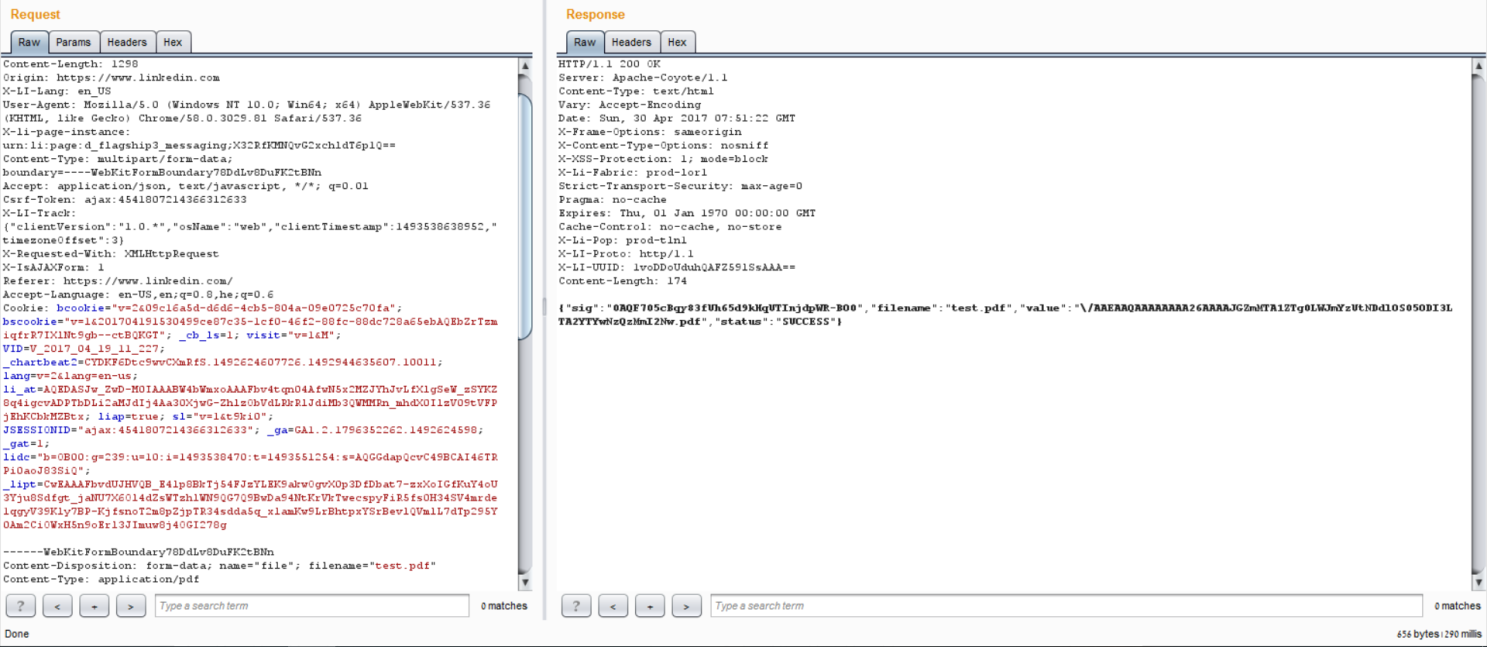
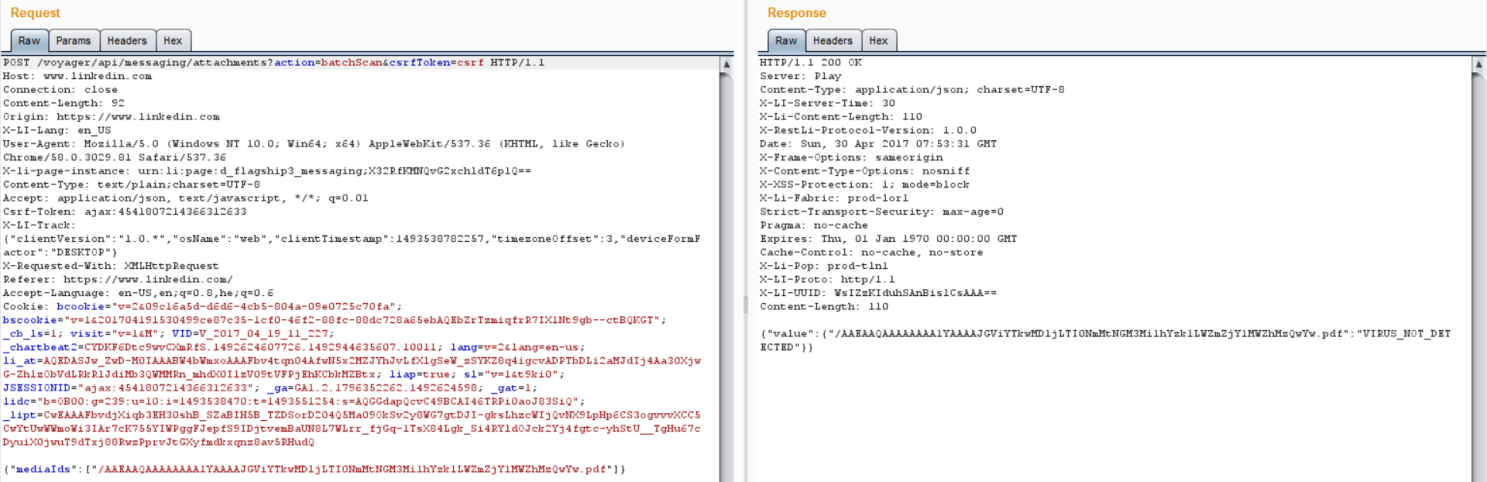
We have been able to identify multiple vulnerabilities that take advantage of LinkedIn’s security restrictions. When a valid file is uploaded and sent, LinkedIn’s security protections scan the attachment for malicious activity. However, in a recent trial conducted by Check Point researchers, it was discovered that attackers could bypass the security restrictions and attach a malicious file to the LinkedIn messaging service. To do this, an attacker could have uploaded a normal-looking file that passes LinkedIn’s security checks; however the file is only masquerading as a legitimate file, in reality, it is a form of malware that contains malicious content, able to infect the recipient’s network.
Check Point identified the four flaws and reported the discovery to LinkedIn on 14 June 2017. LinkedIn verified and acknowledged the security issues and deployed a fix effective 24 June 2017.
Technical Details
The following flaws presented a possibility to execute arbitrary code on a LinkedIn client PC by hiding malicious document types under the cover of legitimate ones.
The vulnerability can be demonstrated by the following examples:
Flaw 1: Malicious PS1 (PowerShell)
The attacker crafts a malicious Power Shell script. The script is saved as a .pdf file.
The attacker uploads the .pdf file to LinkedIn’s CDN server:
Then the attacker proceeds by sending the .pdf file. At this stage, the attacker controls the name of the file (Name parameter), the format of the file (MediaType parameter), and the file extension.
When the victim downloads the file and opens it, a payload is executed and the victim’s device is infected.
Flaw 2: Registry file
REG is a file type that can make changes in the Windows Registry database. In a nutshell, the Registry contains important data, such as program preferences, dynamic Windows modules, list of installed/uninstalled programs, etc. The REG file type is designed for advanced users, in order to make it easier for them to perform all changes at once, rather than applying them manually one by one.
In our case, the attacker could craft a REG file which contains a malicious PowerShell script and disguise it as a .pdf file. The REG file is sent via the LinkedIn platform and passes the virus check. Then it is uploaded successfully to LinkedIn’s CDN and sent to the victim. When the victim opens the file received via LinkedIn, the crafted REG containing the malicious payload runs, giving attacker control over the user’s machine. From now on, the script will run each time the user logs in to his computer.
Flaw 3: Scrambled Macro
The attacker crafts a malicious XLSM file, embedded with Macro, disguised as an XLSX file. The Macro is a scrambled VB script shell code. The masqueraded file passes the anti-virus check and then it is uploaded successfully to LinkedIn’s CDN and sent to the victim. When the victim opens the malicious XLSM file, Excel runs the VB scripts and the victim gets infected.
Flaw 4: Malicious File Containing OLE (CVE 2017-0199):
To watch the Demo, click here.
The attacker crafts a malicious DOCX file containing an external object. This object is linked to an HTA file on the attacker’s server. The DOCX file is then uploaded successfully to LinkedIn’s CDN, passing the virus check and sent to the victim. When the victim opens the malicious DOCX file, WINWORD automatically downloads the HTA file through the object link, and then runs it. Once the HTA file is executed, the victim is infected.