Layered protection is a must. Here’s why.
Cyber attacks are advancing in their sophistication. Take WannaCry – once it makes a single entry, its ability to spread throughout the organization and evade protection layers infected hundreds of thousands of computers. These advances make it clear that there’s no singular point solution that can act as a “magic bullet”.
Companies have been approaching their security reactively: incidents or trends push them to test and buy a single point solution for one, specific gap at a time, resulting in a collection of point solutions without an equal increase in protection. Most attacks use this lack of integration to their advantage, attacking multiple stages to defeat a disjointed collection of point solution.
Let’s take a deeper dive into this concept using a well-known attack, Wannacry, a hot industry, end point protection, and the challenges that face customers in making decisions about strategy and technologies.
Why is testing good?
Customers in a “hot” industry like security, and specifically end point protection, face a lot of noise in the form of marketing messages. The idea is that testing products cuts through this noise and lets the customer make an informed decision. These are often called Proof of Concept, or PoC, tests. A PoC is one of the most important steps in the sale cycle because it puts the marketing message to the test. Often, the sales pitch highlights what the customer wants to hear while hiding the products downfalls. A PoC is the most reliable way to verify a statement and select the best solution while answering the customer’s needs from a variety of vendors.
The Challenge – Proof of Concept Manipulation
From a security perspective, after stability and performance, the most important part of a PoC is the detection ratio. A PoC checks detection rates versus misdetections. Ideally, this would take place in a real world traffic environment, but most PoCs are performed in a staged environment in order to avoid the dangers of down time and performance issues.
The downside of POCs is the security effectiveness. Vendors are constantly competing head to head, hoping to block the most attacks, preferably detecting attacks which other vendors fail to detect. One way vendors show their competitive advantage is by offering customers an additional set of testing samples which the vendor is certain his product will detect while the competitors will fail.
Though this is the most effective way to stay current with the latest exploit and evasion techniques, it sometimes leads to “over cooked” samples. These samples can lead to attack step detection by a single vendor, which are part of the attack chain but are not malicious by themselves, and they are convicted using static signatures made by their creator.
A classic example of such detection is a vendor creating a Command & Control (C&C) for the home cooked sample with a matching signature to block it. The vendor is “detecting” the attack though it has no reputation data related to it and can’t be marked as malicious based on a general heuristic.
A bit about heuristics vs. signatures:
The most optimal solution to detect an attack is signature matching. Identifying a file or domain as a specific known malicious file or URL would be the fastest and most accurate detection technique.
Unfortunately, the attack needs to be known for signature matching, rendering it largely ineffective for unknown and unidentified risks.
Our solution is to implement heuristics. Heuristics is a model that compares behavior based on experience to return a verdict on a potential threat. While a signature looks at a picture frozen in time, the heuristic looks to see if the threat behaves like other malicious things.
Going back to the classic scenario of C&C detection, signature based detection would be:
- Detect all URLs under malicious.com
While a heuristic detection might be:
- Detect all URLs under a domain that was newly registered in the last 5 days, if the domain register created a known malicious domain in the last year.
You can see how the signature will be faster and more accurate than the heuristic, but the heuristic can match previously unseen attacks.
Layers of heuristic prevention
So what do we mean when we say layered protection? Layered protection highlights how unknown attacks can be prevented without using signatures. We just need to have inspection points at every various step or layer in order to prevent unknown, incoming attacks.
Let’s look at WannaCry as an example of an attack that wasn’t known when it struck and how it can be stopped using layered protection.
WannaCry, one of the most well-known and destructive cyber-attacks, could have been prevented with good security hygiene – which includes patching vulnerable systems, in this case the SMB vulnerabilities used in the attack.
The EternalBlue exploit, a tool developed by the NSA which has IPS protections that were released two month prior to the attack, could have been stopped by inspecting the SMB traffic with Intrusion Prevention Systems for a known vulnerability.
After penetrating an enterprise, the self-sufficient WannaCryworm has all it needs to move laterally, making it harder to prevent. The attack can be contained in the infected environment either by segmenting the network (literally putting up inspection gates between parts of the business), or inspection of internal traffic, which sends that traffic through a system that can inspect for threats.
In the first few hours of a worm spread, the signature is not available for AV’s, this is similar for the NotPetya spread. A heuristic approach to malicious file encryption can prevent this attack vector by blocking the attack in the final protection layer which is the end point agent before any damage is done.
Real attacks and layered protection
So now that we understand the difference between signatures and the heuristic approach, including how they are used in layered protection, let’s go over the detection of a real attack chain. Below shows each step of an attack and how they can be blocked through layered protection.
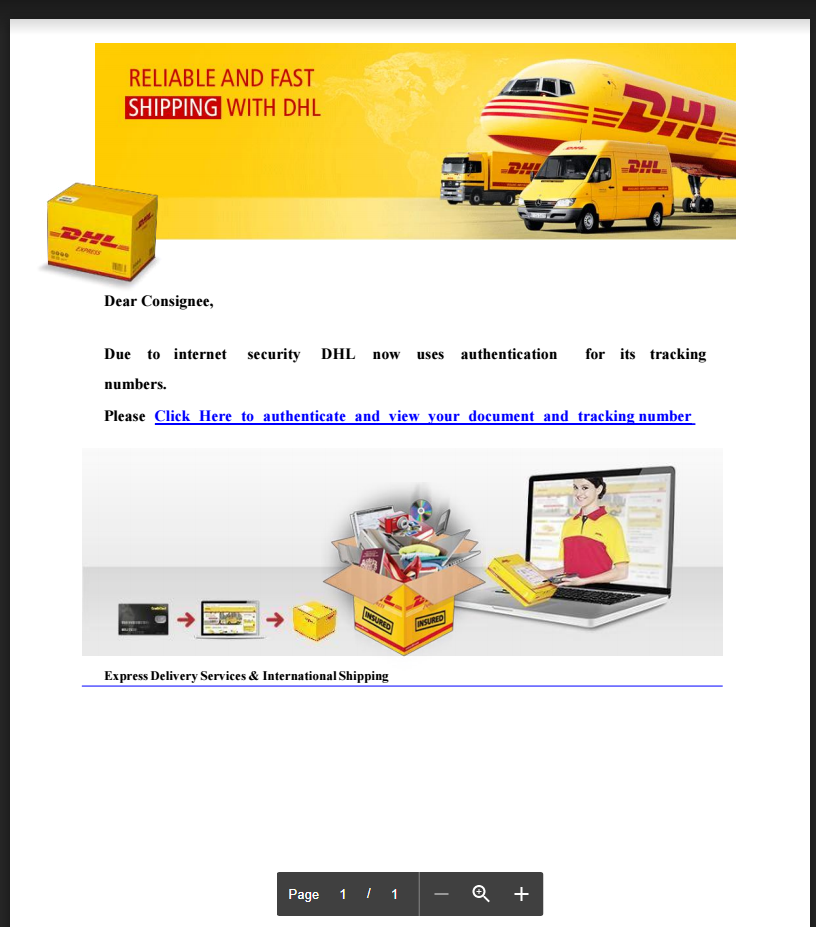
1. Phishing email with an attachment containing a phishing link
See the following DHL phishing message, enticing the user to click a redirecting link on tinyurl.com
To prevent this you can block all shortening services, but marking all URLs under tinyurl.com as malicious will result in too many false alerts and make your customer move your product off prevention mode in to detection mode (just alerting that an attack succeeded without preventing it).
Another approach can be following the link, but this can lead to unwanted results (email verification, service enlisting or unsubscribing, data exfiltration from air gapped networks etc.).
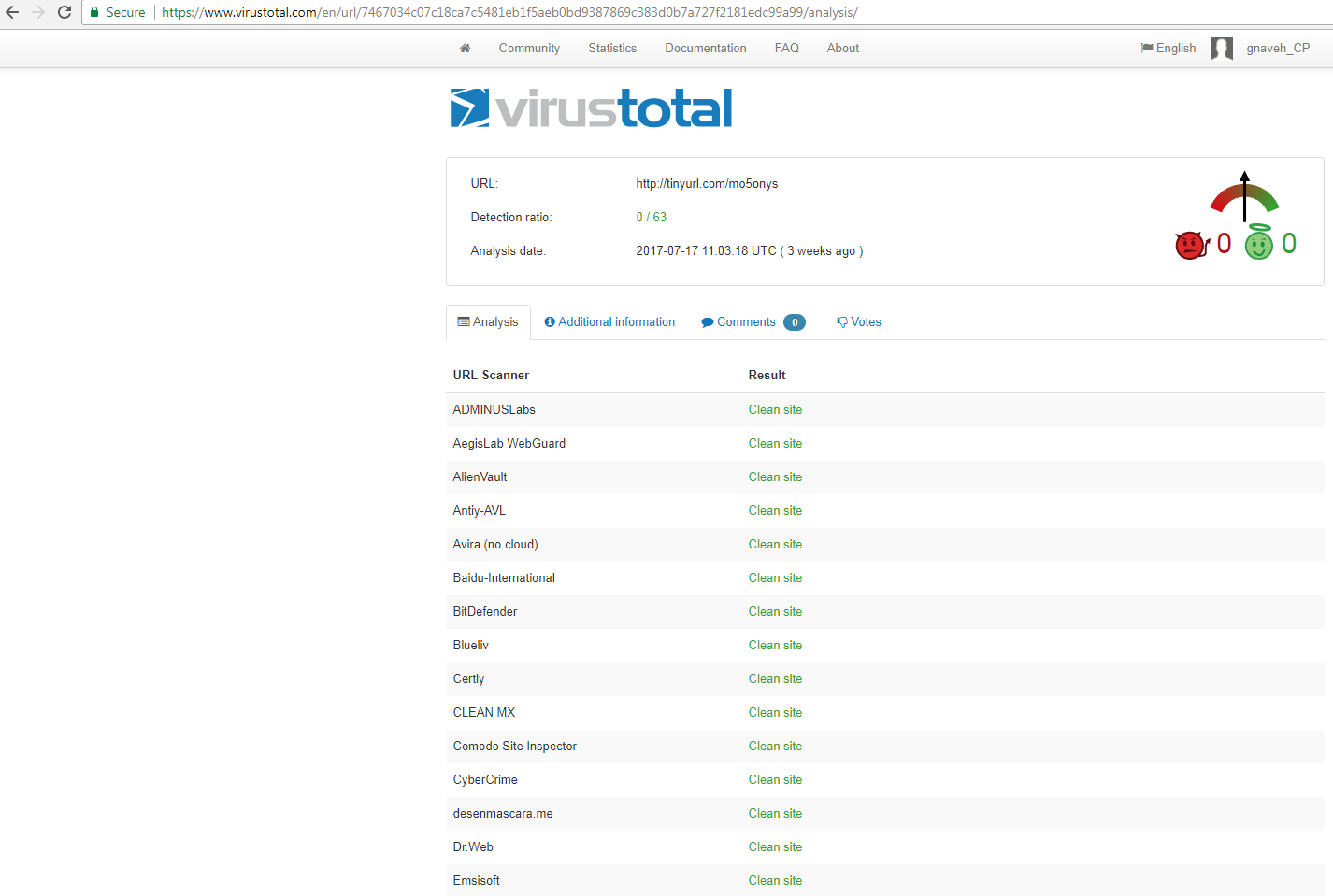
As the following VirusTotal reputation service for the URL shows it would not help:
A layered protection would have the following points of detection if the attachment is not blocked by spam filters or AV’s:
- Matching the attack when the link is clicked and the redirecting service will get to the malicious URL.
- If the URL is not known, the phishing page will be retrieved and can be found malicious based on heuristics (mirroring a site, sending credentials in clear text or to bad reputed sites.
- Detecting a user entering credentials to the wrong site (Like SandBlast Anti Phishing protection)
2. Downloading and executing a payload
Another way to bypass URL reputation is using a legit file sharing, like drop box and Sendspace as in the following link we saw in the wild:
hxxps://fs08n1.sendspace[.]com/dl/1b18640ff2ab3549d7a81a1d0ab578ca/5982fd9312c657be/0tmka2/Windows Loader v2.2.2.zip
As general blocking of sendspace will not work for all enterprises and can cause misdetections in PoCs, a layered protection can meet the attack in the following way:
- Emulating the file in a sandbox environment and blocking malicious file download before they reach the end point.
- If a file is downloaded outside the perimeter or encrypted and can’t be sandboxed, using an end point agent the file can be uploaded to a sandbox by the agent once it is decrypted on the end point.
- An undetectable multi staged payload can be blocked from retrieving the next payload or from data exfiltration by blocking the communication to a C&C, the affected agent can be quarantined and the attack can be contained.
3. Ransomware Encryption Process Detection.
Malicious encrypting tools can be detected when interacting with sensitive data, but some ransomware use legit encryption tools like WinRAR and 7zip. How can one differentiate between legit and malicious use of the programs?
Here is where the SandBlast Anti-Ransomware can be used as the last front line layer by handling the data on the end point.
SandBlast Agent continuously monitors a files encryption while looking for malicious behavior. Once detected, SandBlast contains the attack and restores the affected files. Anti-Ransomware is the last layer to defend the loss of your data. There is no dependency on malware detection or any specific malware family encryption technique, if Anti-Ransomware detects a general extortion type encryption, it will restore the files and stop the attack.
Where’s it all going?
As you can see, there are advantages and disadvantages for every protection layer. Every layer has its vulnerability, which is why in order to defeat attacks, you have to assume there is no magic bullet and you need to keep persistent layered protection.
If customers can resist the shiny new toy syndrome and adopt a consolidated, layered protection strategy, they can be prepared for the next real attack — even if we don’t know what the attack will be.
Our advice is look at the risk in your business and how you are addressing it. When testing products, make sure to determine how that product will integrate with other products to help cover all of your risk and use cases… and not just the shiny new one that you need to fill right now.