Does Your Mobile Anti-Virus App Protect Or Infect You? The Truth Behind DU Antivirus Security
With mobile attacks representing nearly 20% of all cyberattacks in the Americas during the first half of 2017, users are constantly warned to be aware of security risks affecting their data and privacy, and install security software to protect their device. But what happens when antivirus solutions can’t be trusted, and actually compromise users’ privacy?
Check Point mobile threat researchers recently discovered a free mobile anti-virus app developed by the DU group, a developer of Android apps, which collects user data without the device owners’ consent. The app, called DU Antivirus Security, was distributed over Google Play, Google’s official app store, and downloaded between 10 and 50 million times, according to Google Play data.
According to Check Point’s research, when the app runs for the first time, the DU Antivirus Security app collects information from the device, such as unique identifiers, contact list, call logs, and potentially the location of the device. This information is then encrypted and sent to a remote server. The customer information is later used by another app offered by the DU group, called “Caller ID & Call Block – DU Caller,” which provides users with information about incoming phone calls.
While users trusted DU Antivirus Security to protect private information, it did the exact opposite. It collected the personal information of its users without permission and used that private information for commercial purposes. Information about your personal calls, who you’re speaking with and for how long, was logged and later used.
Check Point reported the illegal use of the users’ private information to Google on August 21, 2017, and the app was removed from Google Play on August 24, 2017. A new version that doesn’t include the harmful code was uploaded to the Play store on August 28, 2017. Version number 3.1.5 of DU Antivirus Security is the latest version number found to include this privacy-leaking code, but older versions might still include it.
In addition to DU Antivirus Security, Check Point researchers detected the same code in 30 other apps, 12 of which were found on Google Play, and subsequently removed. These apps probably implemented the code as an external library, and transmitted the stolen data to the same remote server used by DU Caller. All in all, the illicit code affected between 24 and 89 million users who installed these apps, according to Google Play data.
Users who installed the DU Antivirus Security or any of the other apps should verify they are upgrading to the latest version that does not include this code.
Since anti-virus apps have a legitimate reason to request unusually extensive permissions, they are the perfect cover for fraudsters looking to abuse these permissions. In some cases, mobile anti-virus apps are even used as a decoy for delivering malware. Users should be aware of these suspicious anti-virus solutions, and use only mobile threat protection from reputable vendors that are proven to be capable of safeguarding mobile devices and the data stored in them.
Technical Details:
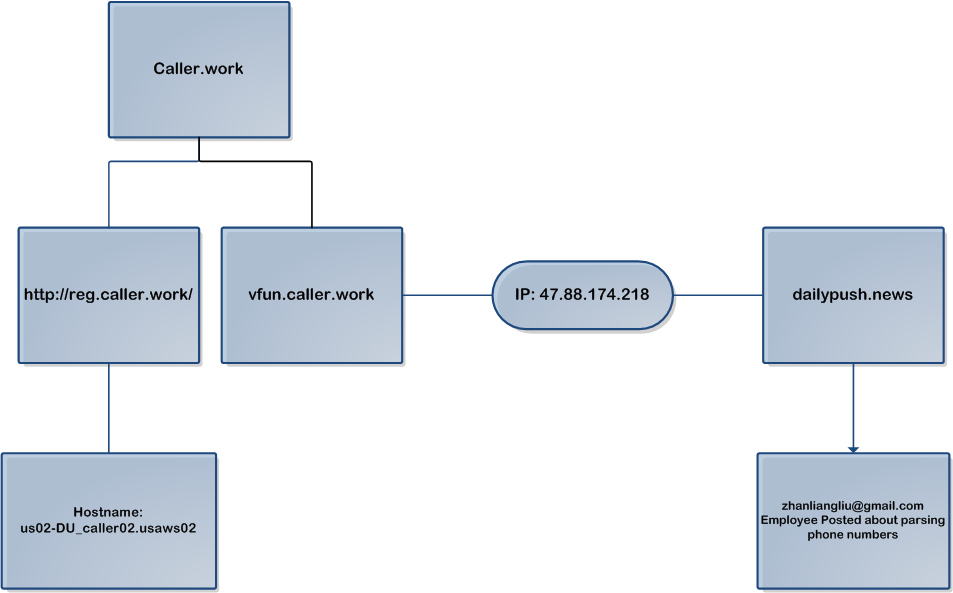
DU Antivirus Security steals the information from the user’s device when the app is first run. The stolen information is then sent to the server caller.work, which is not registered to DU apps. However, this domain has two subdomains which indicate it is indeed connected to the DU caller app. First, the subdomain http://reg.caller.work/ is a PHP webpage, which specifies its hostname: us02-Du_caller02.usaws02, and contains the name of the DU caller app.
See Check Point Research for the complete technical report.
In addition, the sub domain vfun.caller.work is hosted on IP 47.88.174.218, a private server which also hosts the domain dailypush.news. This domain is registered to zhanliangliu@gmail.com, a Baidu employee, who used the same email address to post about parsing phone numbers (http://zliu.org/post/python-libphonenumber/). Since the DU apps are part of the Baidu group, and the post deals with a functionality related to the caller app, this indicates a connection between the stolen information and the caller app.
The DU caller app already came under fire for an ambiguous privacy policy, which displays different terms on separate pages, and of executing its activity regardless of whether it received the user’s consent. Last year, Cheetah Mobile’s Anti-Virus faced similar accusations after providing a service which may violate privacy regulations.