How Can Your Business Score Touchdowns Without An Offensive Line?
What the Philadelphia Eagles Can Teach Us About Cyber-Security
Imagine your founding CTO resigning … right before your company’s biggest annual conference. How do you adapt, maintain momentum, and bring home wins?
The Philadelphia Eagles experienced the American football version of this nightmare scenario when their star quarterback, Carson Wentz, tore his knee ligaments a few weeks before the NFL playoffs. Before his injury, the betting markets had the Eagles as front-runners, with 6-to-1 odds to win the championship. The week after, their odds tumbled down to 9-to-1.
This weekend, 110 million people in the United States will celebrate one of the country’s most important civic holidays: the Super Bowl. Tom Brady and his New England Patriots are on one side, fighting for a record-breaking sixth NFL championship.
Waiting for them? The Philadelphia Eagles, led by their backup quarterback Nick Foles.
How did the Eagles make it through their conference, beating out fifteen teams for a chance at its first-ever Lombardi trophy – without their starting, league-leading quarterback?
Turns out, the quarterback overshadows the five most consequential players on the field: the humble offensive line.
Tasked with physically blocking the opposing team’s defenders in complex moving patterns, the offensive linemen protect the quarterback and skill players from the defense’s disruption. And the Philadelphia Eagles happen to have the league’s best performing offensive line unit throughout the 2017 season, as rated by sports analytics firm Pro Football Focus.
Without a worthy offensive line, the rest of the offense’s skill level or talent is irrelevant. On the flip side, a cohesive, proactive and committed offensive line will vaunt mediocre, second-string, underdog quarterbacks to the Super Bowl.
In business, your cyber-security architecture is your offensive line. Your customers aren’t interacting with your anti-malware directly, but they’ll trust your product and your business when they know they’re protected. The absence of that trust will render all the talent and quality in your business irrelevant. If customers can’t trust their sensitive financial, personal and medical information with you, no star engineer team or marketing campaign or sales talent will convince them that they should do business with you.
Securing your business means you need a cohesive, committed offensive line that prevents threats proactively.
Cohesion Against the Pass Rush:
An offensive line has five players, playing five separate positions, with distinct responsibilities and different roles on each play. High-level offensive lines are said to be “playing on a string” – every player is moving in unison, setting screens, in a coordinated movement. Poorly-functioning offensive lines don’t communicate … the individual players may be executing well on their assignments, but gaps emerge when the line isn’t playing as one. The defense’s entire strategy is predicated on exploiting these gaps.
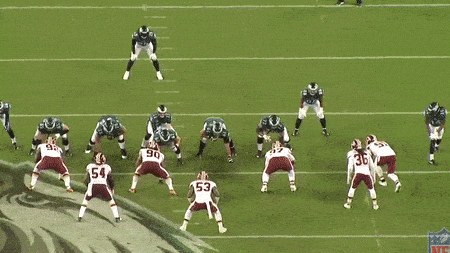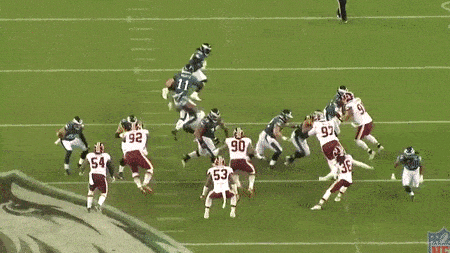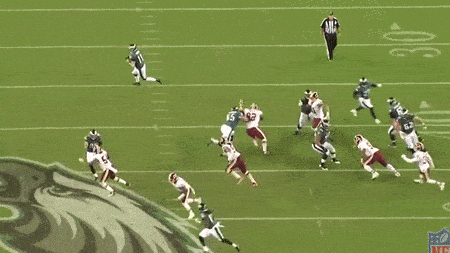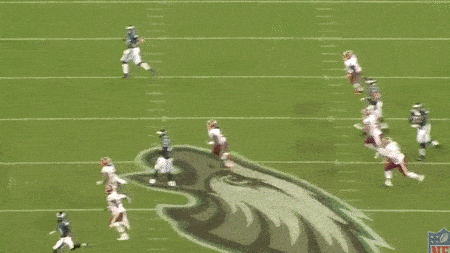
The Eagle’s offensive line executing a complex movement, allowing Foles to roll left pressure-free. Source
Most companies utilize a “confederation of point solutions” cyber-security strategy, where they mix and match their favorite products for separate functions … one company’s firewall, another company’s mobile solution and another company’s network solution, for example.
This strategy is misguided because it leaves gaps open for vulnerabilities to emerge, and that keeps cyber criminals in business. Your business needs a unified, cohesive, comprehensive cyber-security strategy, with your solutions working in tandem rather than separately.
Check Point Infinity Total Protection is based on this premise: by consolidating security across networks, cloud and mobile under one single interface, Check Point Infinity is able to block threats across all environments. Gaps emerge because of miscommunication and haphazard security management – Check Point Infinity closes those gaps by having your cyber security “play on a string,” in cohesion.
Proactively Preventing Threats Downfield:
Over the past decade, we’ve seen the NFL embrace riskier, more aggressive offensive play designs – plays like the read-option. Running out of spread offensive systems require the offensive linemen to run down the field, with the ball-carrier, and set up open lanes past the traditional line of scrimmage. Instead of sitting back and reacting to the defense’s strategy, these linemen are proactively opening holes for the other players on offense to exploit:
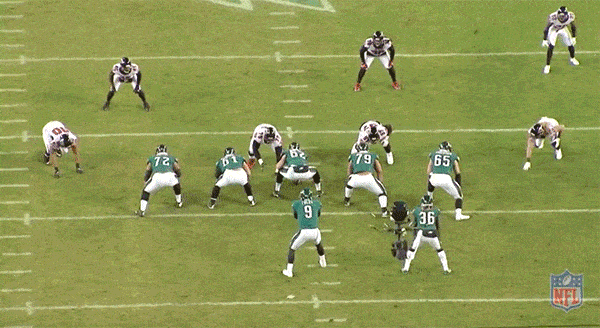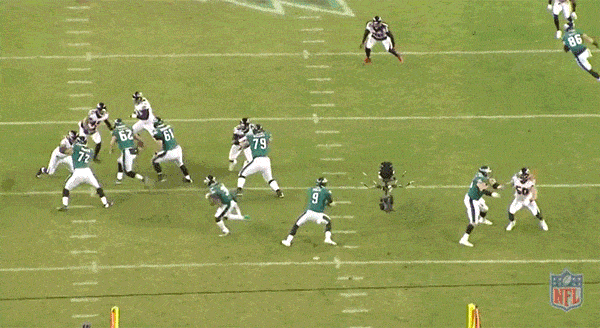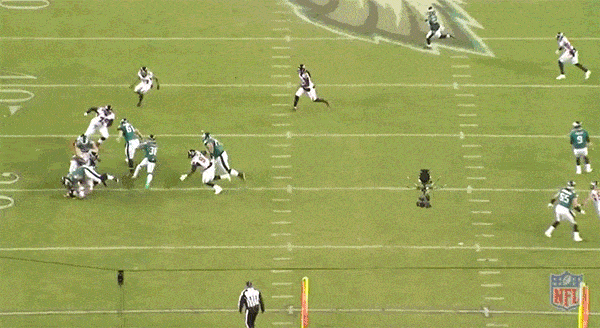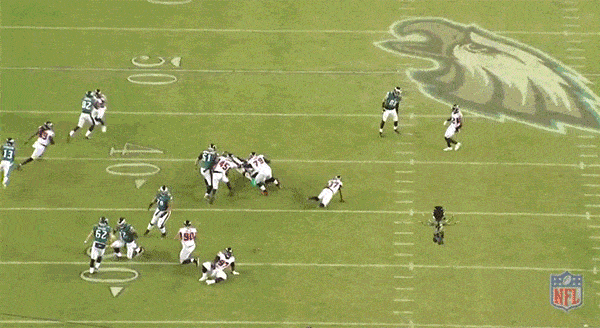
Notice the linemen running down the left field, allowing the ball-carrier to gain extra yardage. Source
Cyber-security is seeing a similar paradigm shift from detection to prevention. Waiting for a cyber attack and then cleaning up the damage is the status quo that has to change, if comprehensive prevention is what you’re looking for your enterprise.
At Check Point, we’re pushing for preventing the vulnerabilities before the threat actors have a chance to exploit and attack. By proactively eliminating vulnerabilities and paying attention to the threat landscape, we’re stopping attacks before they happen. That’s why NSS Labs recommended us for advanced threat prevention – achieving 100 percent threat prevention using only a single, consolidated gateway.
Commit, Commit, Commit:
You can have the most advanced and sophisticated cyber-security system in the market, but if your employees aren’t adopting best cyber hygiene practices as if their own personal data was at risk, you won’t survive a cyber attack.
The Eagles did not plan to lose Jason Peters, their offensive line’s veteran leader. But midway through the season, the nine-time Pro Bowl left tackle tore his knee, ending his season. The Eagles needed their players to take initiative and stay committed to their cause, despite this obstacle.
As reported by Sports Illustrated, he stayed on the sidelines to give advice and help coach the rookies who were filling in for him. His physical contributions ended after his injury, but his mental contributions only increased.
Whenever the team went on the road to play away games, he held daily phone calls with the inexperienced back-ups to help them get up to speed with the game plan. Peters went out of his way to mentor the young players. As quoted in Sports Illustrated by Peters’ teammate, guard Chace Warmack:
“Honestly, that’s why I think we have so much success—because we just communicate all the time. There’s no dumb question…there’s always information floating around this locker room, so if you need help with something, you can get it anywhere.”
The Eagles finished 13-3, ranking first in their conference. The players believed in their team – no matter the obstacle.
Cyber security requires the same culture of commitment and communication. Your employees need to be aware of your latest practices, understanding why they need to frequently change their passwords or why they shouldn’t open unfamiliar emails or access public, unsecured wi-fi on their work computers, and on and on.
There has to be enough buy-in to the cause of security in order to truly stay protected.
Main Takeaways:
Cybercrime isn’t avoidable. It’s inevitable. Cyber-attackers will always attempt to compromise your systems, access your data and steal your money. NFL defenses will always target the quarterback and attempt to tackle him in their attempt to stop the opponent from scoring. It’s part of the game.
Some companies leave gaps open, react too late, and fail to commit their culture to securing themselves. They get hacked. Not every NFL team has a chance at a Super Bowl – only one out of 32 can hold up that championship trophy at season’s end. The rest get sacked.
The Philadelphia Eagles have their shot at glory on Super Bowl Sunday. Watch for their offensive line – they might have a lesson or two on cyber security for you.
Learn more about Check Point Infinity Total Protect.









