
Championship Basketball, Championship Cybersecurity: Lessons from the Golden State Warriors
Immovable object, meet unstoppable force.
Led by two-time league MVP Stephen Curry, the Golden State Warriors are chasing basketball history. They’ve broken the record for wins in a regular season, they’ve scored and defended at all-time percentages, and they’ve won two championships in the past three years — nearly sweeping LeBron James and the Cleveland Cavaliers last year.
With a star-studded roster, it’s easy to dismiss the Warriors’ success as a matter of having superior talent. Dig a little deeper, however, and you’ll see that the Warriors are powered by innovation, creativity, and confidence. They offer the blueprint to defeating LeBron James – the basketball version and the cyber-attack version. (Read the first part of the series here)
When most people watch the Golden State Warriors play, they follow the camera and focus on the ball. But pay attention to what the other four Warriors are doing, and you’ll begin to understand how and why the dazzling offensive theatrics come to fruition.
Unified and Integrated Basketball
On offense and on defense, the other four players are constantly switching and screening. This means that on defense, instead of each player having an opposing player as their assignment all night, they’re constantly rotating on each possession – whoever has the ball is seeing multiple Warriors defenders, and as the defenders step out, they’re closing any gaps on the sides for the offensive players to pass through.
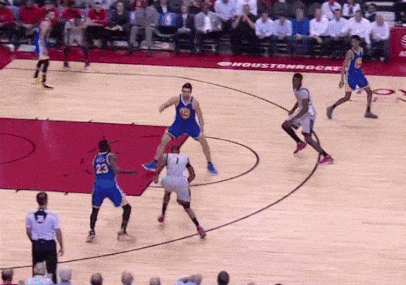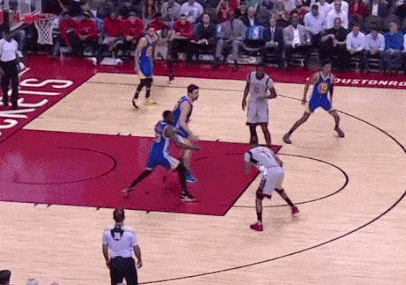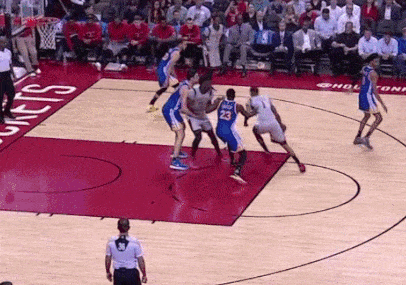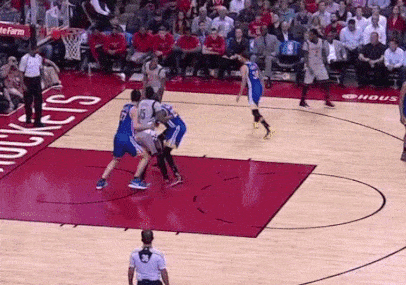
Notice how the ball-handler sees two defenders on the same play – the Warriors defenders know the exact right time to switch, adjusting to the offense’s movements. Source: https://www.sbnation.com/2017/3/29/15108012/james-harden-stats-warriors-bad-defense
This defense is unified and cohesive – the defenders “play on a string,” constantly communicating with each other in order to be aware of each other’s movements. The offense runs the same way – away from the ball. The Warriors set an elaborate sequence of screens, stepping in front of the defenders to briefly stop their momentum before running to other defender to do the same thing.

Follow #27 and notice how he subtly drops his hip in front of the scorer’s defender, giving him just enough space for a good shot. Source: https://medium.com/@dirtydub47/the-brilliance-of-draymond-green-a3fd4ba96129
This progressively breaks down the defense, as the defenders start losing track of where to run and what areas to cover. This swarm of screens provide the chaos needed for the scorers, be it Steph Curry or Kevin Durant or a rookie back-up player, to get enough space to cleanly shoot the ball.
Switching and Screening Fifth-Generation Malware
Cyber defense requires that unified, cohesive system as well.
Fifth-gen malware attacks multiple vectors. All they need is one vulnerable entry point – an unsecured mobile device, or an improperly protected cloud network – and once they find a way in, Gen V malware moves laterally to infect the entire system. Any gap in your protection is the gap to losing your sensitive data to cyber-criminals.
But when an organization has solutions in place for their cloud and mobile networks, and those solutions are all connected, they’re able to constantly switch on the malware. The malware may try to enter in the cloud, but with a unified, comprehensive security platform, the cloud defense alerts the rest of the system about this particular malware.
Instead of having five separate defenders for your organizations, all operating independently, you need one defensive system where the different products are working together on a string. Much like the Warriors, they’re constantly switching and screening and communicating with each other, closing any gaps before they emerge.
A multi-layered, unified cyber-security strategy is the first step toward beating mighty malware. Stay tuned to learn how Steph Curry’s advanced threat prevention capabilities can rain three pointers on the LeBron-esque fifth-gen malware of the world.









