
Can You Hear The Digging? The Dangers of Mobile Mining
Mobile malware focused cyber-criminals are fast adapters, and tend to follow rising trends in order to reach a wider audience. Today’s current trend is cryptocurrencies.
There are several ways in which cyber criminals are taking advantage of the current frenzy surrounding cryptocurrencies. Some mobile miners look to secretly mine these digital currencies without the user’s knowledge, while others aim to dupe the user into installing the malware by promising them a share of the mined coins but in fact intend to simply display illegitimate ads. Alternatively, the more sophisticated malware attempts to obtain the user’s cryptocurrency wallet credentials in order to brazenly steal his money.
Mobile miners do have a few things in common however. For starters, most of them manage to infiltrate official app stores such as Google Play and Apple’s App Store, and leverage them to reach a wide audience. In addition, they use technologies introduced by other mobile malware families such as banker malware and adware to improve their results.
In this article, we will review this emerging trend and suggest ways to tackle it.
Mining Undercover:
One type of mobile miner is that which infects the victim’s device by disguising itself as an unrelated and legitimate app, and then uses the device’s computing power to mine cryptocurrencies.
These malware rely on creating a large number of devices to form a botnet and, since they display minimal malicious activity, often manage to easily slip by an app store’s security defenses. Due to their clandestine maneuvers, there has been an increase in these silent cryptominers in recent years.
Indeed, just recently many of these malicious apps have been seen to infiltrate Google Play, with no end in sight to the trend. Check Point researchers also identified an example of a mining malware on Google Play which reached over 10,000 downloads, and has since been removed. Another strain of malware targeted users via SMS messages promising them free Bitcoins, but then abused their device for cryptomining instead. Mining activity was also one of the modules delivered to a botnet in one of the most comprehensive malware ever found.
Scam Miners – Mining Ads From Users
With the rapid rise in the value of cryptocurrencies, it is understandable that many would like to get in on the action. Not all however have the technical capabilities required to mine them however.
Cybercriminals thus take advantage of this combination of desire with a lack of know-how by promising users a share in the coins mined in return for them voluntarily installing ‘mining’ software.
However, this promise of riches is empty and all the user will actually receive in return for his good will is the display of unwanted and illegitimate ads, from which the malware’s developer profits.
Check Point researchers recently found an example of this type of malware on Google Play, in an app that reached over 100,000 downloads. The app in question claimed to mine Bitcoins, and promised to pay each new user 50,000 Satoshis (the smallest unit in Bitcoin, worth around $10 at the time of publication). Since the app claims that the user can only withdraw after an extortionate amount of Bitcoin is accumulated, the user’s share is never actually paid out as that amount of Bitcoin earned will never be achieved. The app also requests users to give it a five-star rating to inflate its reputation and enable it to trick more users.

The malware on Google Play
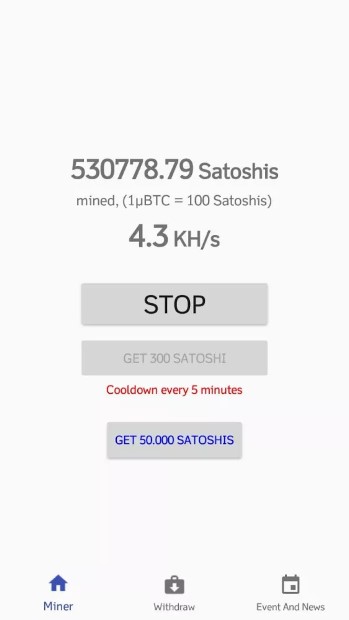
Fake “mining” page
Crypto-Bankers – A New Type of Mobile Bankers
Finally, and perhaps the most harmful, are mobile miners which try to steal a victim’s cryptocurrency wallet’s credentials by impersonating popular cryptocurrency sites.
The first example of this was discovered in October on Google Play. In this instance the malware had disguised itself as the Poloniex cryptocurrency exchange’s mobile app. Once downloaded, the hackers would then request the user to enter his credentials, supposedly to connect to his account, while actually redirecting the user to a compromised site `połoniex.com’ (notice the fake “l”) instead of ‘poloniex.com’.
While the two apps containing the malware were removed from the play store, Check Point researchers found a new version of it a month later, again disguised as a Poloniex app. This time the hackers had managed to fraudulently register as a @poloniex.com account. The malware was removed from the Play Store after Check Point reported it to Google, but not before it had reached over 10,000 downloads.
Mobile malware has even managed to breach Apple’s garden wall and enter the App Store, with a similar malware trying to get the users to grant the app access to their account details and authentications. The malware was soon removed after concerned users reported its suspicious activity, but this is a reminder that no app store is impregnable to mobile malware.
Appendix 1 – List of SHA256 Hashes
Mining on Google Play:
c5fd75c235a7954996694cf61986ece2e658d74eba6857328d1f025c62797d68
Scam miner:
coinminerandroid.coinminer.cma.coinminerandroid, 028e00d9d0fe5594d6dde9ba284e58029db36711e2ca0e35fdc909ed1d42e241
Crypto-Banker:
306a4fd41ce67784db399eced6531ac629bd9fe05d3347665bb935f1100e37f2









