October 2018’s Most Wanted Malware: For The First Time, Remote Access Trojan Reaches Top 10 Threats
Check Point’s latest Global Threat Index reveals RATs gaining in prominence, while cryptomining malware continues to dominate rankings
For the first time, Check Point threat intelligence researchers found that a remote access Trojan (RAT) has reached the Global Threat Index’s Top 10. Dubbed “FlawedAmmyy”, this type of attack allows attackers to remotely control the victim’s machine– gaining full access to the machine’s camera and microphone, collecting screen grabs, stealing credentials and sensitive files, and intrusively monitoring the victims’ actions.
Over the last few months, Check Point researchers discovered a number of other campaigns distributing the FlawedAmmy RAT, but in October, the team found the most widespread Flawedammy RAT campaign yet seen, accounting for its surge. This is the first time that Check Point Threat Intelligence has seen this type of attack spread far enough to reach Global Threat Index’s top ten.
Cryptomining malware continue to lead the index — Coinhive remains the most prevalent malware with a global impact of 18%, and Cryptoloot has risen to second on the list impacting 8% of organizations worldwide. While cryptominers remain the dominant threat, the number of malware families on the list that target user data may indicate that information such as login credentials, sensitive files, banking and payment information is hasn’t lost any lucrative appeal to cyber criminals.
October 2018’s Top 10 ‘Most Wanted’:
*The arrows relate to the change in rank compared to the previous month.
-
↔ Coinhive – Cryptominer designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s knowledge or approval, and without sharing the profits with the user. The implanted JavaScript uses great computational resources of the end users to mine coins and might crash the system.
-
↑ Cryptoloot – Cryptominer, using the victim’s CPU or GPU power and existing resources for cryptomining – adding transactions to the blockchain and releasing new currency. It is a competitor to Coinhive, trying to pull the rug under it by asking a smaller percentage of revenue from websites.
-
↓ Dorkbot- IRC-based Worm designed to allow remote code execution by its operator, as well as the download of additional malware to the infected system.
-
↑ Roughted – Large scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware. It can be used to attack any type of platform and operating system, and utilizes ad-blocker bypassing and fingerprinting in order to make sure it delivers the most relevant attack.
-
↓ Andromeda – Modular bot used mainly as a backdoor to deliver additional malware on infected hosts, but can be modified to create different types of botnets.
-
↓ Jsecoin – JavaScript miner that can be embedded in websites. With JSEcoin, you can run the miner directly in your browser in exchange for an ad-free experience, in-game currency and other incentives.
-
↑ XMRig- XMRig is an open-source CPU mining software used for the mining process of the Monero cryptocurrency, and first seen in the wild on May 2017.
-
↓ Ramnit- Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
-
↔ Conficker- Worm that allows remote operations and malware download. The infected machine is controlled by a botnet, which contacts its Command & Control server to receive instructions.
-
↑ FlawedAmmyy RAT – Remote access Trojan (RAT) that was developed from the leaked source code of the remote administration software called ‘Ammyy Admin’. FlawedAmmyy has been used in both highly targeted email attacks as well as massive spam campaigns and implements common backdoor features, allows the attackers to manage files, capture the screen, remote control the victim’s machine, establish RDP SessionsService and much more.
Triada, the modular backdoor for Android has climbed to first place in the top mobile malware list. It replaces Android banking Trojan and info-stealer Lokibot, which has fallen to second place. Hiddad has returned to the list as this month’s third most prevalent mobile malware
October’s Top 3 ‘Most Wanted’ mobile malware:
-
Triada – Modular Backdoor for Android which grants super user privileges to downloaded malware, as helps it to get embedded into system processes. Triada has also been seen spoofing URLs loaded in the browser.
-
Lokibot – Android banking Trojan and info-stealer, which can also turn into a ransomware that locks the phone in case its admin privileges are removed.
-
Hiddad – Android malware which repackages legitimate apps and then released them to a third-party store. Its main function is displaying ads, however it is also able to gain access to key security details built into the OS, allowing an attacker to obtain sensitive user data.
Check Point researchers also analyzed the most exploited cyber vulnerabilities. Once again, CVE-2017-7269 remains in first place of the top exploited vulnerabilities list, with a global impact of 48% of organizations. In second place was OpenSSL TLS DTLS Heartbeat Information Disclosure with a global impact of 46%, followed by Web servers PHPMyAdmin Misconfiguration Code Injection impacting 42% of organizations.
October’s Top 3 ‘Most Exploited’ vulnerabilities:
-
↔ Microsoft IIS WebDAV ScStoragePathFromUrl Buffer Overflow (CVE-2017-7269) – By sending a crafted request over a network to Microsoft Windows Server 2003 R2 through Microsoft Internet Information Services 6.0, a remote attacker could execute arbitrary code or cause a denial of service conditions on the target server. That is mainly due to a buffer overflow vulnerability resulted by improper validation of a long header in HTTP request.
-
↑ OpenSSL TLS DTLS Heartbeat Information Disclosure (CVE-2014-0160; CVE-2014-0346) – An information disclosure vulnerability exists in OpenSSL due to an error when handling TLS/DTLS heartbeat packets. An attacker can leverage this vulnerability to disclose memory contents of a connected client or server.
-
↑ Web servers PHPMyAdmin Misconfiguration Code Injection – A code injection vulnerability has been reported in PHPMyAdmin. The vulnerability is due to PHPMyAdmin misconfiguration. A remote attacker can exploit this vulnerability by sending a specially crafted HTTP request to the target.
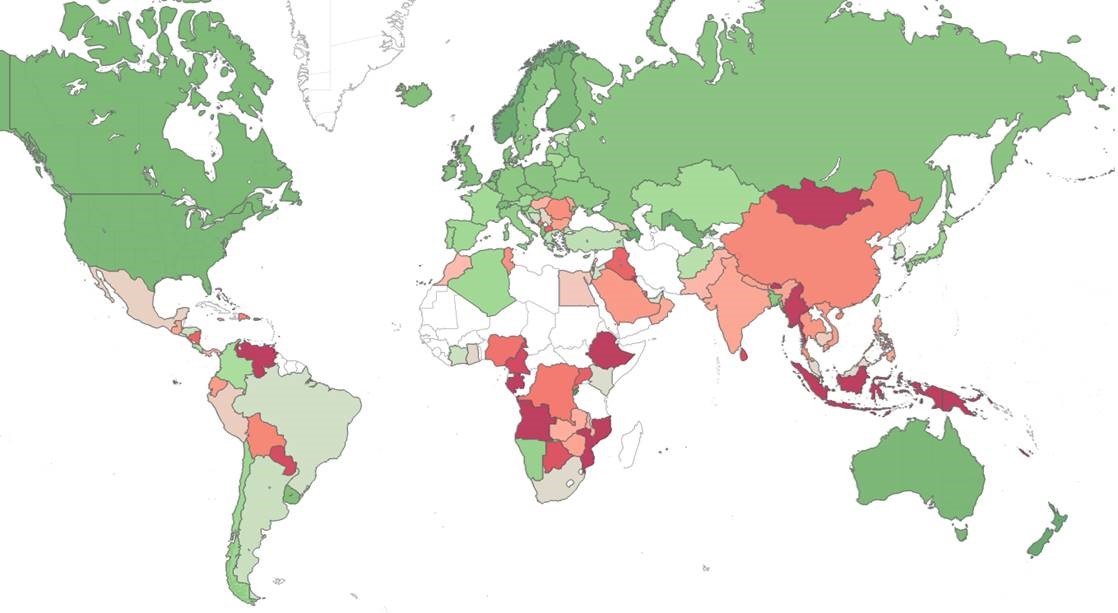
The map below displays the risk index globally (green – low risk, red- high risk, grey – insufficient data), demonstrating the main risk areas around the world.
Check Point’s Threat Prevention Resources are available at: http://www.checkpoint.com/threat-prevention-resources/index.html