
Ransomware: How to Avoid the Dangerous Wave of Attacks
By Yaelle Harel, Technical Product Marketing Manager
The average cost to rectify the impacts of most recent ransomware attacks is US$732,520 for organizations that don’t pay the ransom. It rises to US$1,448,458 for organizations that do pay [1].
The top ransomware types in Q3 were Maze and Ryuk. There has been a significant increase in Ryuk’s activities in 2020, and it has been damaging about 20 organizations per week, especially in the healthcare industry. Falling victim to a Ryuk ransomware attack is exceptionally costly to an organization. The operators of the Ryuk demand a high ransom and in some cases, even paying the ransom is not enough to regain a company’s access to sensitive or valuable data. The multi-year costs of protecting an organization from ransomware are less than the cost of recovering from a single ransomware attack.
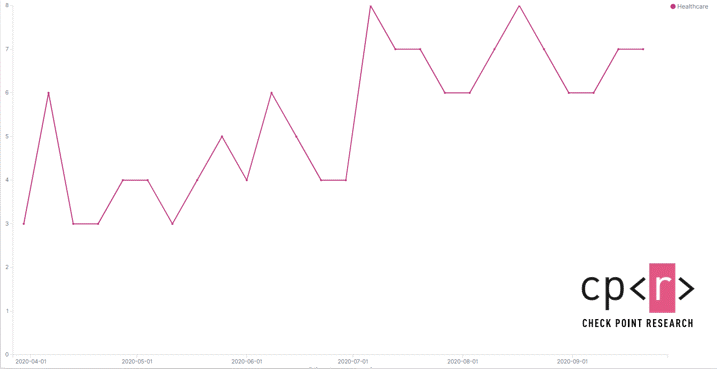
Figure 1 Ryuk Attacks on healthcare organizations
SandBlast Agent detects the Ryuk attack’s activity, blocks the ransomware, and prevents the damage. The Anti-Ransomware engine monitors the changes to files on user drives to identify ransomware behavior such as file encryption. Once the ransomware behavior is detected, SandBlast Agent blocks the attack and recovers the encrypted files automatically.
What if a Ryuk Ransomware encrypted one of the endpoint devices in your organization? How can you make sure it doesn’t spread and encrypt all of your endpoints? If you don’t have SandBlast Agent, or you didn’t set it to “Prevent” mode as Check Point recommends, how will you decide whether to pay out the ransom or not? Wouldn’t it be better to have built-in automatic recovery methods?
We will demonstrate how the SandBlast Agent Forensics Report allows you to investigate the Ryuk ransomware quickly and thoroughly. SandBlast Agent Forensics Report provides profound automatic insights including risk-based prioritization, attack flow diagram, business image, MITRE ATT&CK mapping, and a detailed report of suspicious events. SandBlast Agent Forensics Report also helps you stop the attack’s spread and mitigate the damage by providing built-in automatic remediation and recovery.
Overview of Ryuk attack
Ryuk is a ransomware used by the TrickBot gang in targeted and well-planned attacks against several organizations worldwide. The ransomware was originally derived from the Hermes ransomware, whose technical capabilities are relatively low, and include a basic dropper and a straight-forward encryption scheme. Nevertheless, Ryuk was able to cause severe damage to targeted organizations, forcing them to pay extremely high ransom payments in Bitcoin. Unlike common ransomware, systematically distributed via massive spam campaigns and Exploit Kits, Ryuk is used exclusively in tailored attacks. To learn more about the ransomware, sign-up for the upcoming case study webinar that will take place on Oct 28th 2020.
Damage assessment
As a victim of a ransomware attack, you are on the horns of a dilemma. You have to choose between paying the ransom and self-recovery. The first is expensive, encourages the attacker to keep his efforts, and it doesn’t even guarantee that your data will be restored or that already stolen data will not leak. The second option usually keeps the availability of the data disrupted for a more extended period which makes it expensive and sometimes even impossible. Damage assessment is a crucial step when deciding how to respond to ransomware. Manual damage assessment will take too long and in such a time-critical is simply not feasible. Automatic damage assessment and visualizing is, therefore, critical.
SandBlast Agent auto-generates Forensics report that provides a detailed business impact assessment. The potential business impact is determined by a patent-protected algorithm that finds the attack tree, attack root and entry point.
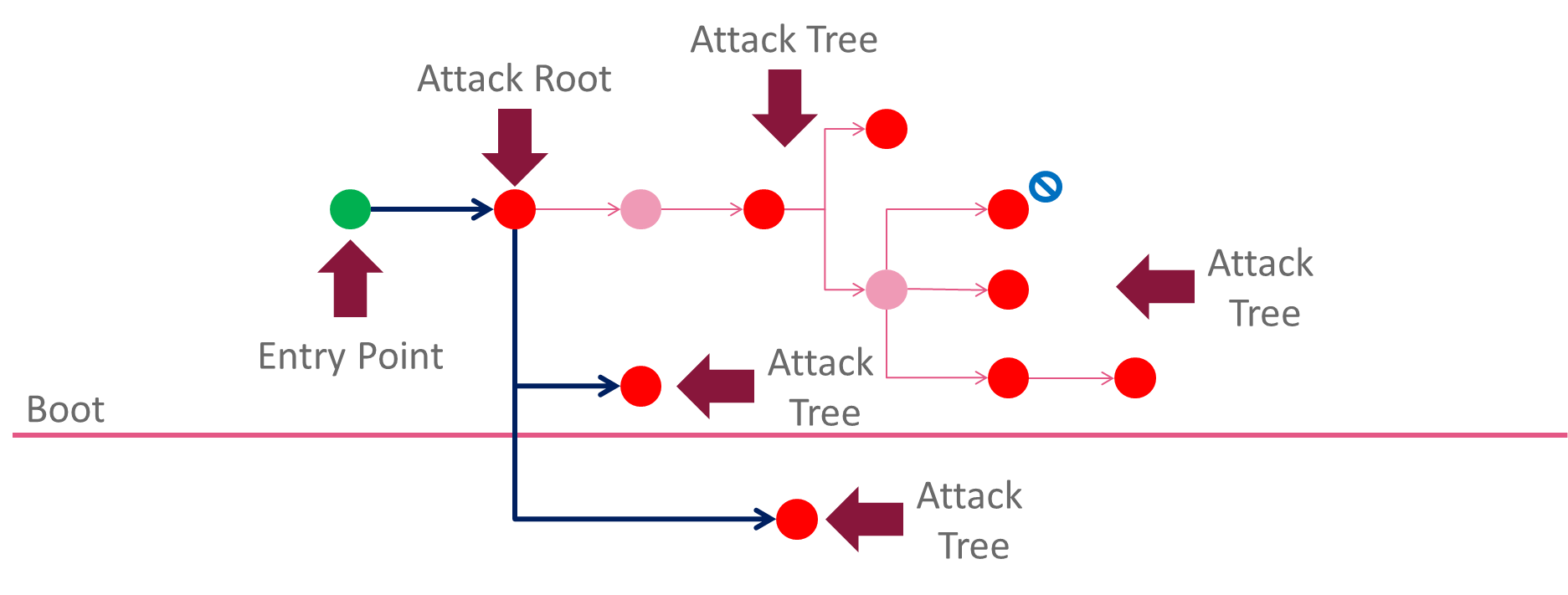
Figure 2 Forensics Report Attack Flow
Let’s go back to the Ryuk attack. First, let’s take a look at the overview of the Forensics report, as seen in figure #3 below. The attack type, status and business impact are clear and easy to drill-down. Visibility is a critical capability when choosing not to automatically prevent and remediate attacks (which we strongly recommend); however, understanding the business impact is also crucial. Even in blocked and remediate attacks, like the one in the below report, understanding the business impact is very important as it allows quick respond and retrospective analysis. It also highlights files and other resources that couldn’t be automatically restored and allows immediate response to those.
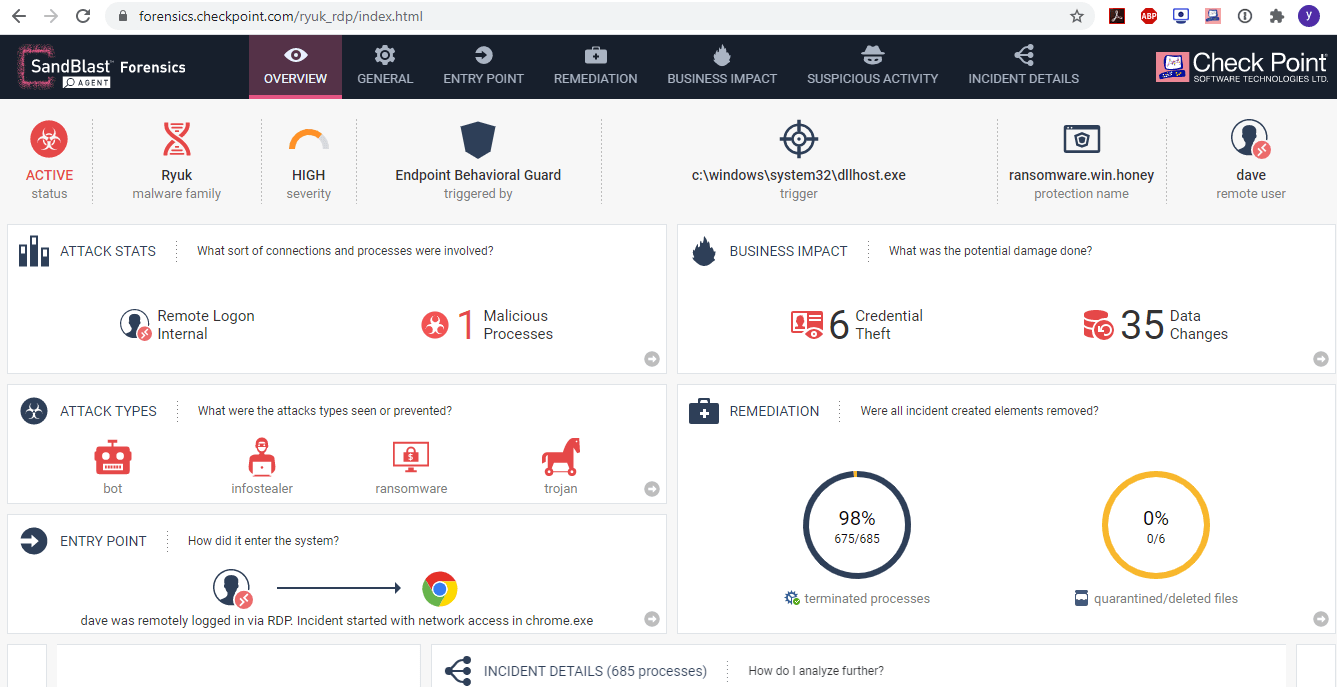
Figure 3- Forensics Overview
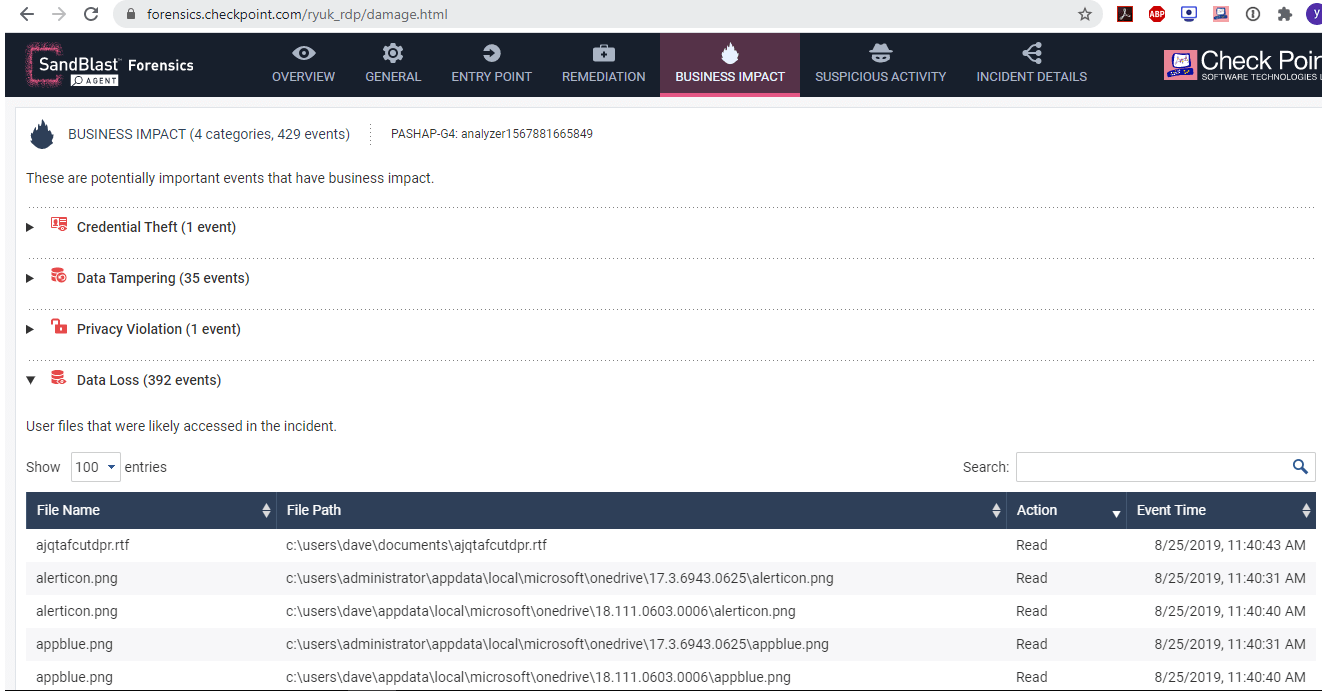
Figure 4 Ryuk Business Impact – Forensics Report
Attack Flow Visualization
Another important factor for quick and effective response to an attack is the ability to understand it well. Using a common-language attack story line is very important as it allows team to collaborate and to use external intelligence to support their response plan. SandBlast Agent automatically maps all events collected by the patent-based algorithm to MITRE ATT&CK techniques and tactics. As you can see in figure #5 below, the data is visualized in the Forensics Report as a matrix, which makes it easier to learn about the attack different steps and actions. In the below image you will find the Ryuk ransomware MITRE ATT&CK matrix, taken from the Ryuk attack’s Forensics Report. You can see the entry point, execution techniques and impact among other tactics. One click on any technique, leads to a detailed information page that explains it and lists all the correlated events.
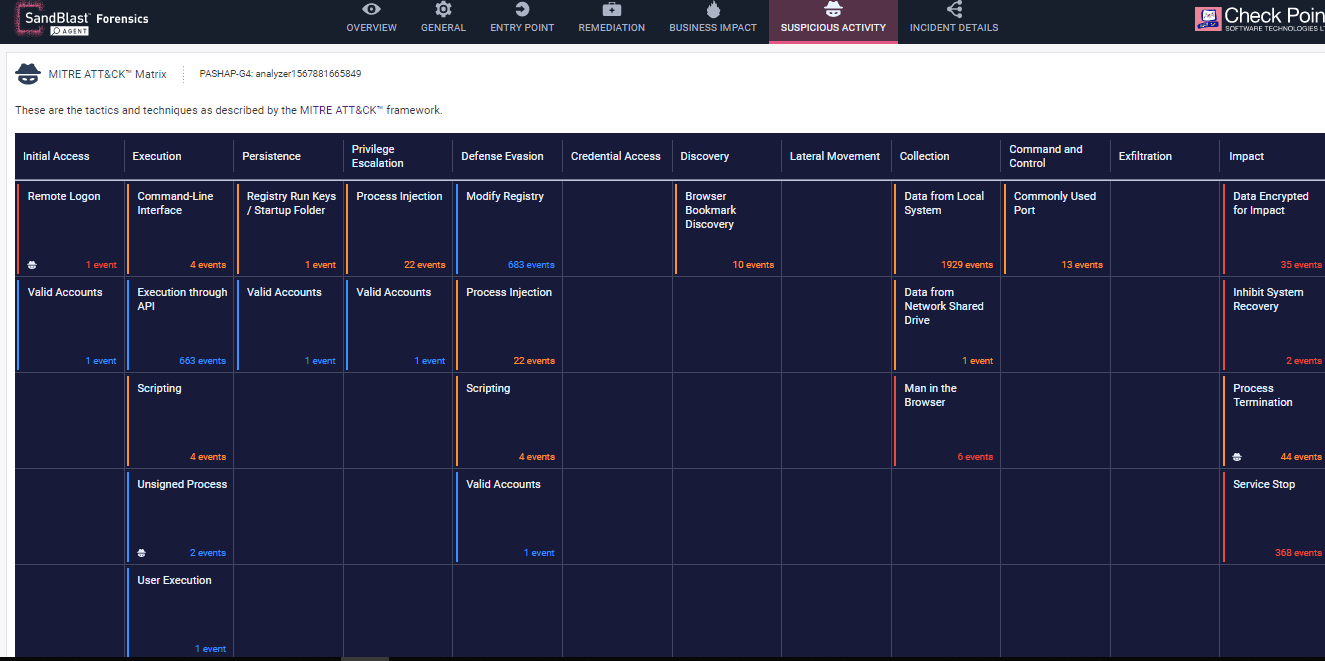
Figure 5 Ryuk MITRE ATT&CK Matrix
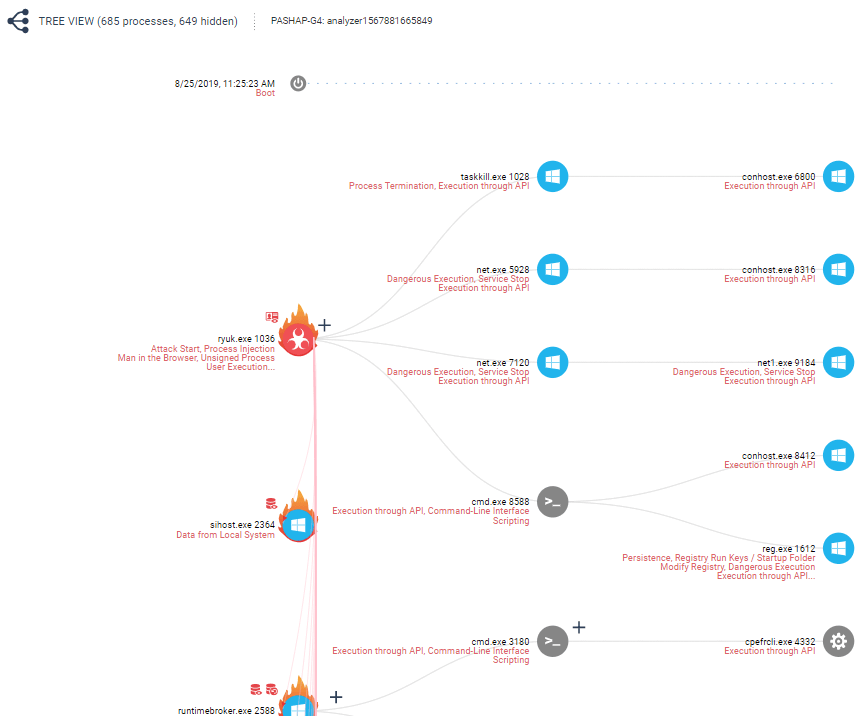
Figure 6 Forensics Tree View (Partial Tree)
Summary
In this blog, we demonstrated how Automated Forensics capabilities could shorten the time it takes to understand and respond to attack. We showed how SandBlast Agent’s visualization of the data, including attack flow, potential damage and MITRE ATT&CK matrix could support decisions that you need to take under the pressure of an active cyber-attack.
SandBlast Agent’s Forensics report is generated automatically based on patent-protected algorithms that ensure the most accurate visualization of the attack’s lifecycle. To learn more, take a look at the interactive Ryuk Forensics Report.
In the next chapter of the series, we will discuss how SandBlast Agent’s Threat Hunting solution helps you quickly and effectively investigate unnoticed attacks.
Sign up for the upcoming case study webinar that will take place on Oct 28th 2020









