The Malware-as-a-Service Industry
Several recent developments have brought the malware infrastructure-as-a-service industry into the spotlight, reminding everyone how prominent it is in the cybercrime arena. The infrastructures that create malware exploit kits are so immense that the global threat landscape can be completely altered when one of them is downed.
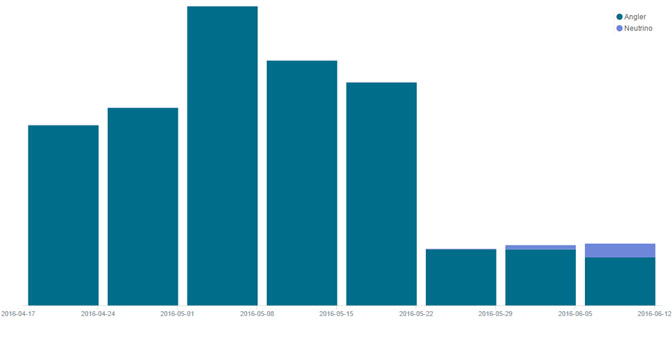
According to Kafeine, a leading exploit kit researcher, the Angler exploit kit has vanished completely since June 7th. We too have detected a major decrease in Angler’s traffic, as seen in figure 1 below. Angler was the most prominent exploit kit in use, however it was soon replaced by the Neutrino exploit kit, which began to spread the same payloads Angler was delivering.
Figure 1: Angler’s Spread
Angler’s disappearance did not go unnoticed by other exploit kit developers. The Neutrino exploit kit developer has doubled the monthly rent charged for the use of his infrastructure from $3,500 to $7,000. These sums are similar to those charged by the Nuclear exploit kit developer and indicate just how profitable exploit kits are for their developers.
We still do not know whether Angler is gone for good or if this is only a minor pause, as it experienced early this year in January. In both scenarios, this points to the large competition in the malware infrastructure-as-a-service industry, with developers doing their best to gain market share. We have seen how easy it is for attackers to use such a service when we analyzed the Nuclear exploit kit, which has a comprehensive user interface that allows attackers to manage their operation with ease and comfort.
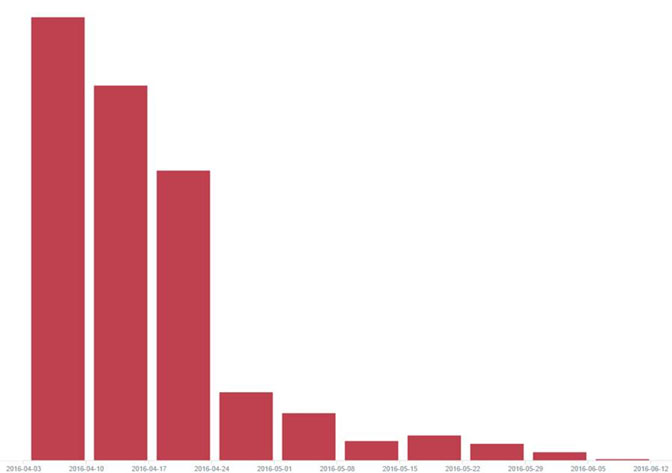
Another major change in the threat landscape is the disappearance of the Necrus botnet, which together with Nuclear’s decline might have a connection to the decrease in the Dridex banker spread, as seen in figure 2 below. This goes to show what a major part the malware-as-a-service industry has in the global cybercrime scene.
Figure 2: The Decline In Dridex Spread
The driver behind this booming black market industry is the growing complexity of security systems. Exploits kits need to be able to evade multiple layers of security, which makes it much harder for a lone hacker to create a successful attack infrastructure on his own. Many attackers rely on existing infrastructures, as we have seen in Nuclear’s case, which served 15 different attackers simultaneously and spread over 110,000 samples of the Locky ransomware in one month alone.
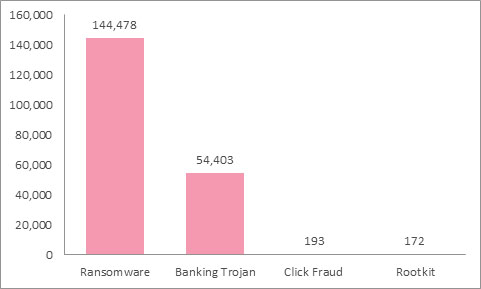
Advanced exploit kits have a stunning success rate, which provide attackers with the capability to strike users hard. They are so powerful in the cybercrime landscape that one can learn about global trends by simply inspecting one of them. The rise of ransomware over banking malware was clearly displayed in the different payloads delivered by Nuclear, as seen in figure 3 below.
Figure 3: Payloads Served By Nuclear
Takeaways from the infrastructure-as-a-service industry
Users and CISOs must understand they are very likely not facing a lone wolf who is trying to infiltrate their network. They are dealing with large organized groups that invest great amounts of time, effort and sums of money to develop the best cybercrime infrastructure in a very competitive market. In order to stay protected, organizations must use multi-layered, threat prevention-focused security measures that are capable of dealing with these actors.