Huawei Routers Exploited to Create New Botnet
- A Zero-Day vulnerability in the Huawei home router HG532 has been discovered and hundreds of thousands of attempts to exploit it have already been found in the wild.
- The delivered payload has been identified as OKIRU/SATORI which is an updated variant of Mirai.
- The suspected threat actor behind the attack is an amateur nicknamed ‘Nexus Zeta’.
Introduction
In the last 10 years, the number of connected devices has grown to over twenty billion, and, as the years go by, they get progressively smarter. However, whereas they score high on convenience, the latest discoveries from Check Point Research shows they still have a lot of homework to do to get their security score up to par.
Attempted Router Exploitation
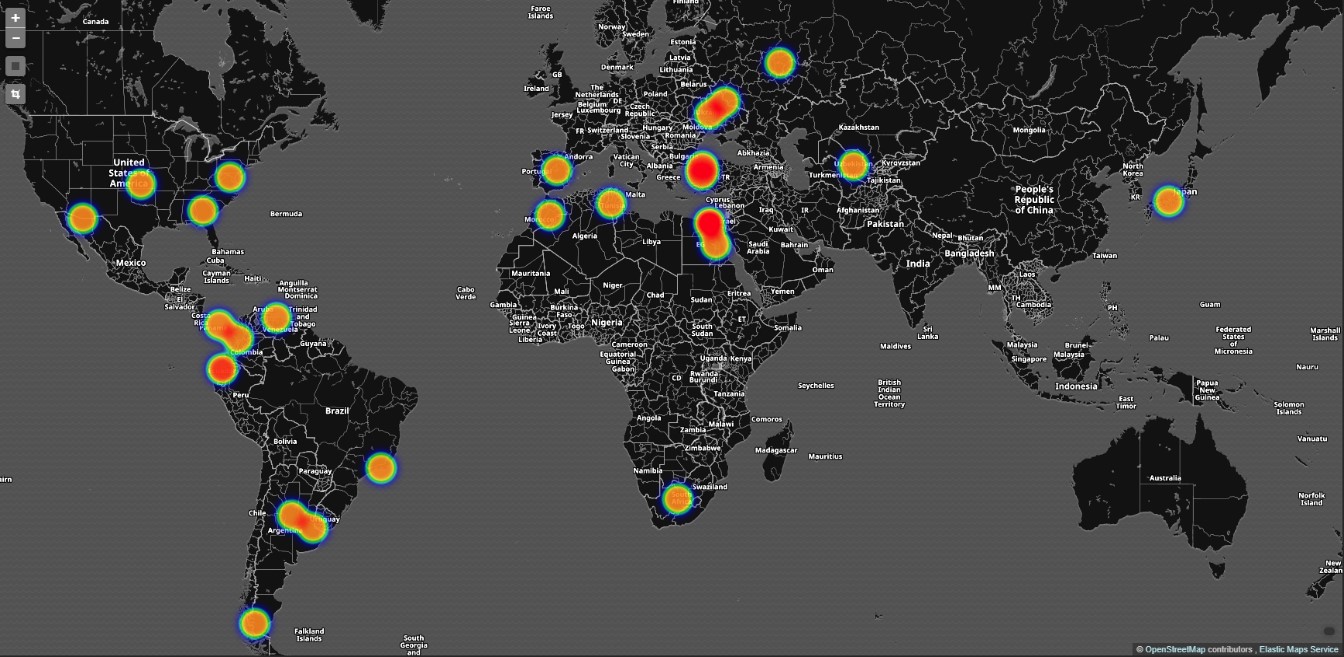
On 23rd November, our sensors and honey-pots were generating suspicious security alerts. Upon further inspection, our analysts were noticing numerous attacks exploiting an unknown vulnerability in Huawei HG532 devices across the world, most notably in the USA, Italy, Germany and Egypt, to name a few. The aim was to create a new variant of the Mirai botnet, the botnet that was responsible for global infrastructural damage in 2016.
How It Works
Huawei aims to make its Home Gateway router as simple and seamless to integrate with home and corporate networks. To do this it applies the Universal Plug and Play (UPnP) protocol via the TR-064 technical report standard.
Designed and intended for local network configuration, TR-064 in practice allows an engineer to implement basic device configuration, firmware upgrades and more from within the internal network.
In this discovery though, our researchers found that TR-064 implementation in Huawei devices unfortunately allowed remote attackers to execute arbitrary commands to the device. In this case, it was the OKIRU/SATORI malware that was being injected in an attempt to build a new variant of the Mirai botnet.
Who Is Behind It?
Due to an impressive volume of traffic, an unknown Zero-Day and multiple attack servers, the identity of the attacker was initially a mystery, with speculations running from advanced nation state perpetrators to notorious threat gangs.
Surprisingly, it appeared an amateur threat actor under the nickname ‘Nexus Zeta’, seemed to be behind this new botnet creation attempt. Indeed, he had recently been active in hacker forums seeking advice on how to build such an attack tool indicating that a combination of leaked malware code together with exploitable and poor IoT security, when used by unskilled hackers, can lead to dangerous results.
The Resolution
As soon as the findings had been confirmed, the vulnerability was discretely disclosed to Huawei so as to mitigate further propagation. Thanks to the fast and effective communication by the Huawei security team, Huawei was able to quickly patch the vulnerability and update their customers.
In parallel, our product teams developed and released an IPS protection, making sure Check Point’s customers were also the first to be protected.
For the full investigation on how this attempted attack operates and who is behind it, please see Check Point Research.