December’s Most Wanted Malware: Crypto-Miners Affect 55% of Businesses Worldwide
Check Point’s latest Global Threat Index reveals the rise of crypto-mining malware targeting enterprises
During the month of December 2017, crypto-mining malware rapidly rose in Check Point’s Global Threat Index’s top ten most prevalent malware.
Crypto-mining malware refers to cybercriminals hijacking the victim’s CPU or GPU power and existing resources to mine cryptocurrency. Check Point researchers found that crypto-miners managed to impact 55% of organizations globally, with two variants in the top three list of malware and ten different variants in the expanded top 100. In December, the crypto-miner Coinhive replaced RoughTed as the most prevalent threat, while the Rig ek exploit kit maintained its position in second. Another new entry to the top ten, the crypto-miner Cryptoloot is in third.
Furthermore, Check Point found that cryptocurrency miners have intentionally been injected into some top websites, mostly media streaming and file sharing services, without notifying the users. While some of this activity is legal and legitimate, the tools can be hacked to dominate more power and generate more revenue, using as much as 65% of the end-users’ CPU power.
Ad-blocking software, stemming from users losing patience with excessive pop-up and banner advertisements, has been slashing many websites’ advertising revenue. Those websites are turning to crypto-miners as a new source of revenue – often without the knowledge or permission of the visitors to the website. Similarly, threat actors are turning to crypto-mining malware as a new way to make money – illegitimately gaining access to the users’ CPU power to mine for their own crypto currency – making it even likelier that we’ll see this trend gain steam over the coming months.
Top 10 ‘Most Wanted’ Malware:
*Arrows relate to the change in rank compared to the previous month.
- ↑ Coinhive – Crypto-Miner designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s approval. The implanted JavaScript uses great computational resources of the end users machines to mine coins, thus impacting the performance of the system.
- ↔ Rig ek – Exploit Kit first introduced in 2014. Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer. The infection chain starts with a redirection to a landing page that contains JavaScript that checks for vulnerable plug-ins and delivers the exploit.
- ↑ Cryptoloot- Crypto-Miner, using the victim’s CPU or GPU power and existing resources for crypto mining – adding transactions to the blockchain and releasing new currency. It is a competitor to Coinhive, trying to pull the rug under it by asking less percents of revenue from websites.
- ↓ Roughted – Large scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware. It can be used to attack any type of platform and operating system, and utilizes ad-blocker bypassing and fingerprinting in order to make sure it delivers the most relevant attack.
- ↔ Fireball– Browser-hijacker that can be turned into a full-functioning malware downloader. It is capable of executing any code on the victim machines, resulting in a wide range of actions from stealing credentials to dropping additional malware.
- ↑ Globeimposter– Ransomware disguised as a variant of the Globe ransomware. It was discovered in May 2017, and is distributed by spam campaigns, malvertising and exploit kits. Upon encryption, the ransomware appends the .crypt extension to each encrypted file.
- ↓ Ramnit -Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
- ↑ Virut – Botnet that is known to be used for cybercrime activities such as DDoS attacks, spam, fraud, data theft, and pay-per-install activities. It spreads through executable file infection (through infected USB sticks and other media), and more recently, through compromised HTML files (thus infecting vulnerable browsers visiting compromised websites)
- ↓ Conficker– Worm that allows remote operations and malware download. The infected machine is controlled by a botnet, which contacts its Command & Control server to receive instructions.
- ↑ Rocks – Web based Crypto-Miner, which hijacks the victim’s CPU and existing resources for crypto mining.
Triada, a modular backdoor for Android, continues to be the most popular malware used to attack organizations’ mobile estates followed by the Lokibot and Lotoor.
Top 3 ‘Most Wanted’ mobile malware:
- Triada – Modular Backdoor for Android which grants superuser privileges to downloaded malware.
- Lokibot – Android banking Trojan and info-stealer, which can also turn into a ransomware that locks the phone.
- Lotoor– Hack tool that exploits vulnerabilities on Android operating system in order to gain root privileges.
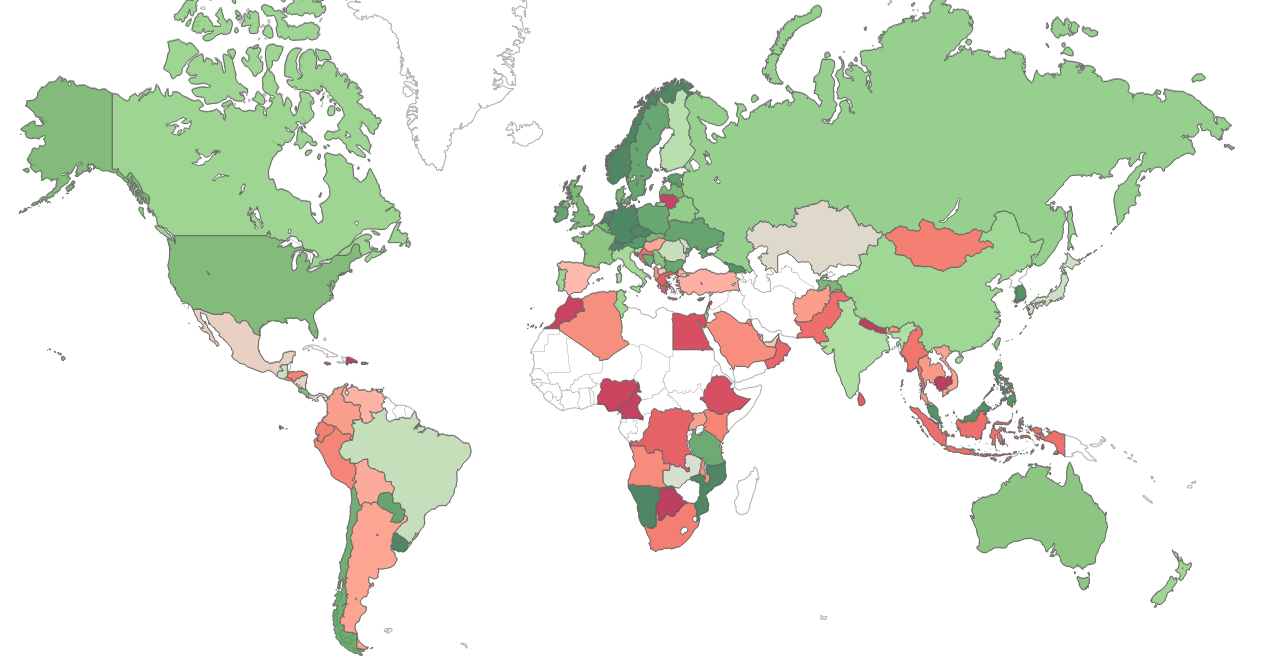
The map below displays the risk index globally (green – low risk, red- high risk, white – insufficient data), demonstrating the main risk areas and malware hot-spots around the world.
Check Point’s Global Threat Impact Index and its ThreatCloud Map is powered by Check Point’s ThreatCloud intelligence, the largest collaborative network to fight cybercrime which delivers threat data and attack trends from a global network of threat sensors. The ThreatCloud database holds over 250 million addresses analyzed for bot discovery, more than 11 million malware signatures and over 5.5 million infected websites, and identifies millions of malware types daily.
Check Point’s Threat Prevention Resources are available at: http://www.checkpoint.com/threat-prevention-resources/index.html