A security architecture review is one of the most powerful tools in a security architect’s toolkit. Organizations conduct security architecture reviews in various contexts:
- Initial Deployment: When deploying an application for the first time in the cloud, to ensure that the deployed architecture reflects what was designed.
- Ongoing Deployments: For all material infrastructure changes to a cloud environment, e.g., when a new service is added or components are significantly changed.
- Configuration Drift Monitoring: Ongoing evaluation of those security controls to ensure that there is no security drift.
- External Vulnerabilities: When new vulnerabilities come to light, such as when Spectre and Meltdown were announced, to identify the potential impact to your environment.
AWS provides powerful security constructs that allow you to segment east-west traffic in your cloud environment — VPCs and security groups. A security architecture review in the cloud involves examining security group configurations across your VPC.
In AWS today, a security audit would start with navigating to the Security Groups window in AWS. This is the first step to natively view and understand your security posture.
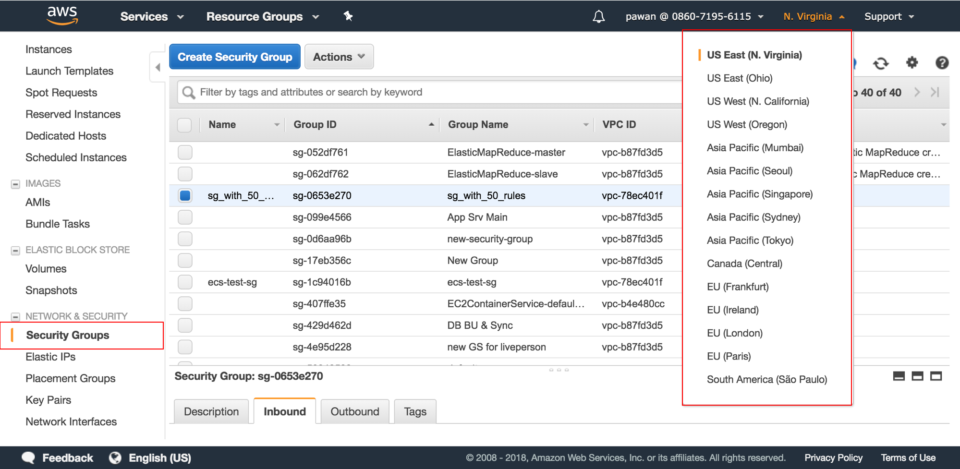
The AWS security groups view provides textual information around your assets, VPCs, and SG/policies across regions. There is a limitation in how much information can be absorbed from this view. Security architects now have to make multiple diagrams for internal stakeholders to provide an accurate picture of their cloud security infrastructure.
Above is an example of a typical AWS topology with the associated security groups that an architect creates. If you know your environment well and are looking to verify your security architecture, this could take about an hour. If you don’t know where to start, this manual drawing out process can be extremely time consuming and frustrating (can take up to several hours to obtain a complete diagram of your network security configuration). Not to mention this is error prone and can get outdated quickly.
And especially when you have assets spread across multiple regions in AWS or have multiple accounts, you have to have multiple tabs open to identify all the communication channels and assess the state of the current network.
For a security architect, a single visual pane of your micro-segmentation architecture is needed to easily understand the effective security policy governing each entity.
Solution: Dome9 Clarity Visualization Tool
When you login to Dome9 and connect your AWS/Azure/GCP accounts, within minutes Clarity gives you a holistic view of all your assets and a lens into your environment like you never did before. Clarity is a dedicated, purpose built platform for understanding and reviewing your security architecture.
What is my Perimeter?: Dome9’s Clarity answers the most important questions around:
– What assets do I really have in the cloud?
– How do the assets interact with each other?
– What is the effective security policy governing each of my assets?
– Which of my assets are at risk of exposure to the public internet?
You can visually interact with your cloud infrastructure in real time and see the relationships between the different VPC components and SG relationships and verify whether the assets/policies that are supposed to be internal facing are actually internal.
Microsegmentation Analysis: You can tell how the security groups (SG) interact with each other and can now understand whether any internal assets are communicating with the public world based on their inbound and outbound rules. The different swimlanes (which are auto classified by Dome9, so customers don’t need to manually create them) represent security groups with various levels of exposure to the public.
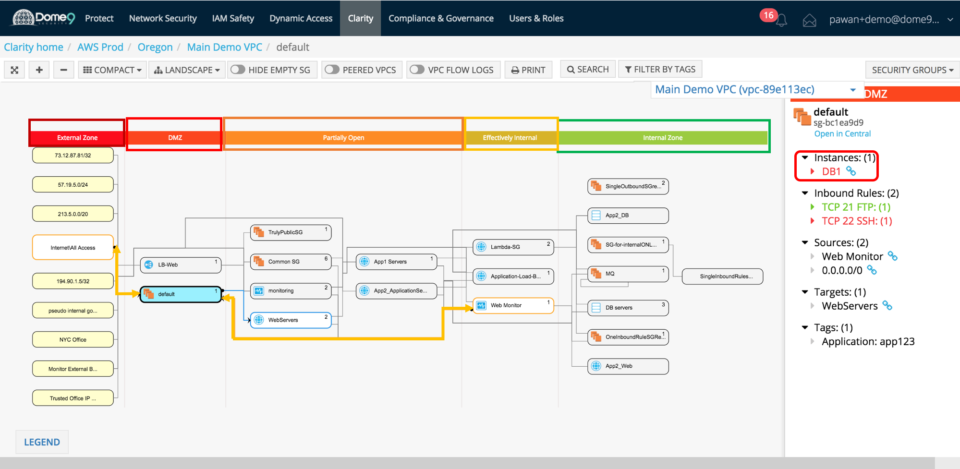
Identify holes in your security posture: From an architectural view, the security group view is a logical representation of your firewall policies that displays the security groups and the associated rules. It also builds out the relationship between which instances can talk to each other based on the configuration. You can immediately identify zombie security groups or instances that are exposed.
In the effective policy view below – you can see default SG is in the DMZ zone and has one instance assignment (DB1, which is also part of the DB servers group). So while the DB Servers security group is itself protected because it is in the internal zone, one of your databases, i.e. DB1 is not protected. Why?
Digging deeper, we realize that even if the rules associated with the security group are correct, an instance can still be assigned to the wrong security group. This is due to a misconfiguration that occurred due to assignment of multiple security groups, and specifically an incorrect default SG to DB1 instance.
The effective policy view brings this to light and tells you what security groups an instance belongs to, and therefore what the effective security policy is. Now it is clear – DB1 is exposed because it belongs to not only the internal DB Servers SG, but also to the Default SG which is in the DMZ.
Spot configuration errors quickly: User misconfigurations account for over 80% of breaches in the cloud – this is a core problem we tackle. You can dig in to the security group and find the culprit – a rule that allows all traffic on SSH port 22.
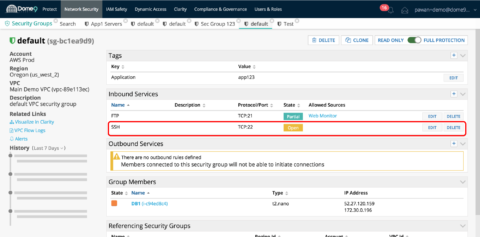
These user configuration errors and potential breach points in your network are the key insights that Clarity provides in an intuitive visualization platform combining asset and policy views. If you want to obtain more information about the security groups and the associated NACLs, security group policies – there is an entity explorer view that Dome9 provides for all your assets to get specific attributes about any instance in your network.
In the next blog – we will discuss how we can address this challenge using Dome9 Active Protection capabilities. Dome9 simplifies and speeds up architecture reviews to ensure that you maintain robust security in your cloud environment.
Please reach out to us if you have any questions about how to best use Clarity for your assessments or cloud security in general.
For more details on security group configuration in Dome9: https://dome9-security.atlassian.net/wiki/spaces/DG/pages/220102810/Security+Groups









