
Global Surges in Ransomware Attacks
- In Q3 2020, Check Point Research saw a 50% increase in the daily average of ransomware attacks, compared to the first half of the year
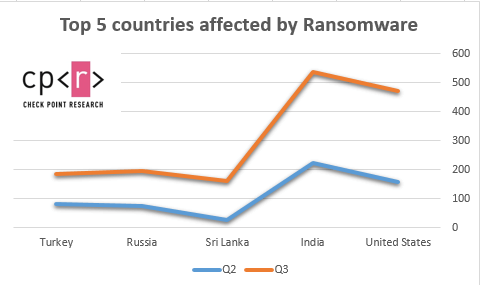
- Countries with the most number of ransomware attacks in Q3 are US, India, Sri Lanka, Russia and Turkey
- Top ransomware types in Q3 were Maze and Ryuk
- Ryuk ransomware now attacks 20 organizations a week
Organizations worldwide are in the midst of a massive wave of ransomware attacks. In the last 3 months alone, the daily average of ransomware attacks has increased by 50%. As these attacks continue to mature both in frequency and intensity, their impact on business has grown exponentially. In the past month, there has been reports about ransomware attacks targeting a shipping giant, a US-based broker and one of the largest watch-makers in the world.
Claiming a new victim every 10 seconds, ransomware has proved to be a lucrative attack method for cybercriminals. Check Point Research studied and analyzed this wave of recent attacks, and this blog details characteristics, the targeted countries, potential reasons for the wave, and tips on how organizations can prevent ransomware attacks.
Ransomware in Q3 2020 – which countries are most impacted?
In the last 3 months, there has been a 50% increase in the daily average of attacks, compared to the first half of 2020. US ransomware attacks doubled (~98% increase) in the last 3 months, making it the #1 most targeted country for ransomware, followed by India, Sri Lanka, Russia and Turkey.
The top 5 countries affected by ransomware in Q3 in terms of the number of attacks are:
- US (98.1% increase)
- India (39.2% increase)
- Sri Lanka (436% increase)
- Russia (57.9% increase)
- Turkey (32.5% increase)
*All the graphs and statistics used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in ThreatCloud during Q3 2020.
Why is this happening now?
The current pandemic has forced organizations to make rapid changes to their business structures, often leaving gaps in their IT systems. These gaps have given cybercriminals the opportunity to exploit security flaws and infiltrate an organizations network. Hackers will encrypt hundreds of thousands of files, incapacitating users and often taking whole networks hostage. In some cases, organizations simply prefer to pay the price instead of dealing with encrypted files and recovering their IT systems. This creates a vicious cycle – the more these type of attacks “succeed” the more frequently they occur.
Cyber-criminals have also started to incorporate a new tactic in their ransomware playbook: double extortion. In what has become a trend since Q1 2020, threat actors are adding an additional stage to their attacks. Prior to encrypting the victim’s databases, the attackers extract large quantities of sensitive information and threaten to publish this information unless their ransom demands are paid.
Driven by fear, organizations sometimes prefer to pay the ransomware immediately to avoid having their valuable data exposed. Recently, different ransomware operators have taken advantage of the current pandemic and used this tactic to force hospitals and medical research institutes to pay the ransom, putting the lives of patients in danger.
Furthermore, Emotet, after taking a 5 month hiatus, has surged back to 1st place in the Most Wanted Malware Index, impacting 5% of organizations globally. Emotet is an advanced, self-propagating and modular Trojan. It was originally a banking Trojan, but has recently been used as a distributor of other malware or malicious campaigns.
Emotet operations sell their infected victim’s details to ransomware distributers and because they are already infected, these victims are vulnerable to more attacks. This makes ransomware attacks even more “effective” to the attacker since more infected targets means more entry points for ransomware attacks.
Ryuk Ransomware in focus
Unlike common ransomware which is systematically distributed via massive spam campaigns and exploit kits, Ryuk is used exclusively for tailored targeted attacks. Ryuk was first discovered in mid-2018, and soon after, Check Point Research published its first thorough analysis of the ransomware which was then targeting the United States. There has been a significant increase in Ryuk’s activities since July 2020, and it has been attacking about 20 organizations per week.
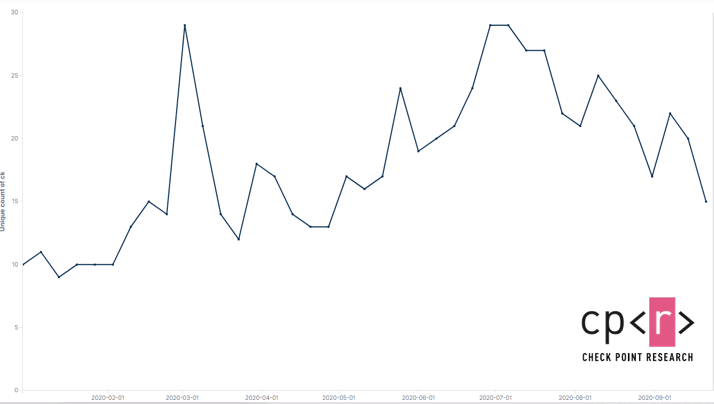
Ryuk attacks per week across all sectors
There has been a steady increase in the number of healthcare organizations targeted by Ryuk, and there has been an almost twofold increase in the percentage of healthcare organizations being impacted by ransomware globally, from 2.3% in Q2 to 4% in Q3. And, healthcare is number one most targeted industry in the US.
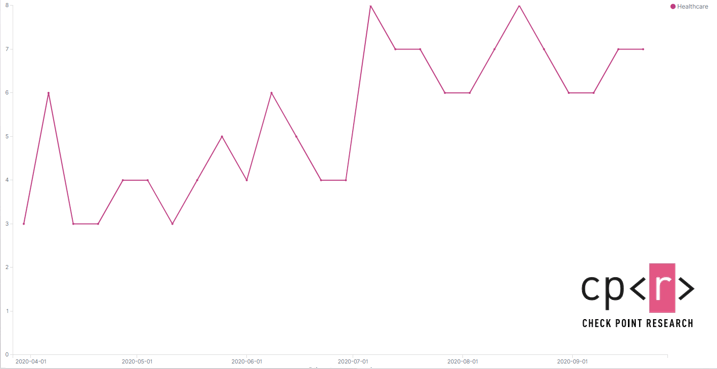
Ryuk Attacks on healthcare organizations
Our data comes from ThreatCloud, Check Point’s threat intelligence engine, which is derived from hundreds of millions sensors worldwide, enriched with AI-based engines and exclusive research data from Check Point Research.
Preventing Ransomware
So what can organizations do to ensure they’re less susceptible to ransomware attacks? Here are some tips to consider.
General Good Practice
- Education: Training users on how to identify and avoid potential ransomware attacks is crucial. Many of the current cyber-attacks start with a targeted email that does not even contain malware, but a socially-engineered message that encourages the user to click on a malicious link. User education is often considered as one of the most important defenses an organization can deploy.
- Continuously data backups: Maintaining regular backups of data as a routine process is a very important practice to prevent losing data, and to be able to recover it in the event of corruption or disk hardware malfunction. Functional backups can also help organizations recover from ransomware attacks.
- Patching: Patching is a critical component in defending against ransomware attacks as cyber-criminals will often look for the latest uncovered exploits in the patches made available and then target systems that are not yet patched. It is critical that organizations ensure that all systems have the latest patches applied to them as this reduces the number of potential vulnerabilities within the business for an attacker to exploit.
Security Best Practice
- Endpoint protections: Conventional signature-based anti-virus is a highly efficient solution for preventing known attacks and should definitely be implemented in any organization, as it protects against a majority of the malware attacks that an organization faces.
- Network protections: Advanced protections in the enterprise network such as IPS, Network Anti-Virus and Anti-Bot are also crucial and efficient in preventing known attacks. Advanced technologies such as sandboxing have the capability to analyze new, unknown malware, execute in real time, look for signs that it is malicious code and as a result block it and prevent it from infecting endpoints and spreading to other locations in the organization. As such, sandboxing is an important prevention mechanism that can protect against evasive or zero-day malware, and defend against many types of unknown attacks on the organization.
Check Point’s Anti-Ransomware solution defends organizations against the most sophisticated ransomware attacks, and safely recovers encrypted data, ensuring business continuity and productivity. Anti-Ransomware is offered as part of Check Point’s comprehensive endpoint security suite, SandBlast Agent, to deliver real-time threat prevention to your organization’s endpoints.









