
MITRE Engenuity ATT&CK® Evaluations Highlight Check Point Software Leadership in Endpoint Security with 100% Detection across All Tested Unique ATT&CK Techniques
By Oleg Mogilevsky, Product Marketing Manager, Threat Prevention and Yoni Nave, Product Manager, Check Point Harmony Endpoint and Shlomi Gvili, Senior Product Manager, Endpoint & Mobile Solutions
We are thrilled to announce that Check Point Harmony Endpoint, Check Point’s complete endpoint security solution, has been recognized for delivering the most comprehensive threat detection and visibility across detection categories in the latest round of MITRE Engenuity ATT&CK® Evaluations. Check Point Harmony Endpoint was evaluated, along with 29 vendors, for its ability to detect attack techniques employed by Carbanak and FIN7, sophisticated threat groups.
Join a live webinar with our security experts on May 5th to better understand the evaluation results and how they can help you strengthen your endpoint security strategy.
Register today: Americas, EMEA/APAC
The latest ATT&CK® Evaluations emulating the tactics and techniques of Carbanak and FIN7 showed Check Point Harmony Endpoint successfully detecting 100% of unique techniques used during the test. For 96% of these unique techniques, Check Point Harmony Endpoint had the highest technique detection level. Check Point Harmony Endpoint achieved a leading result among all participants in analytics detection (which includes context and mapping to the relevant technique instead of raw telemetry).
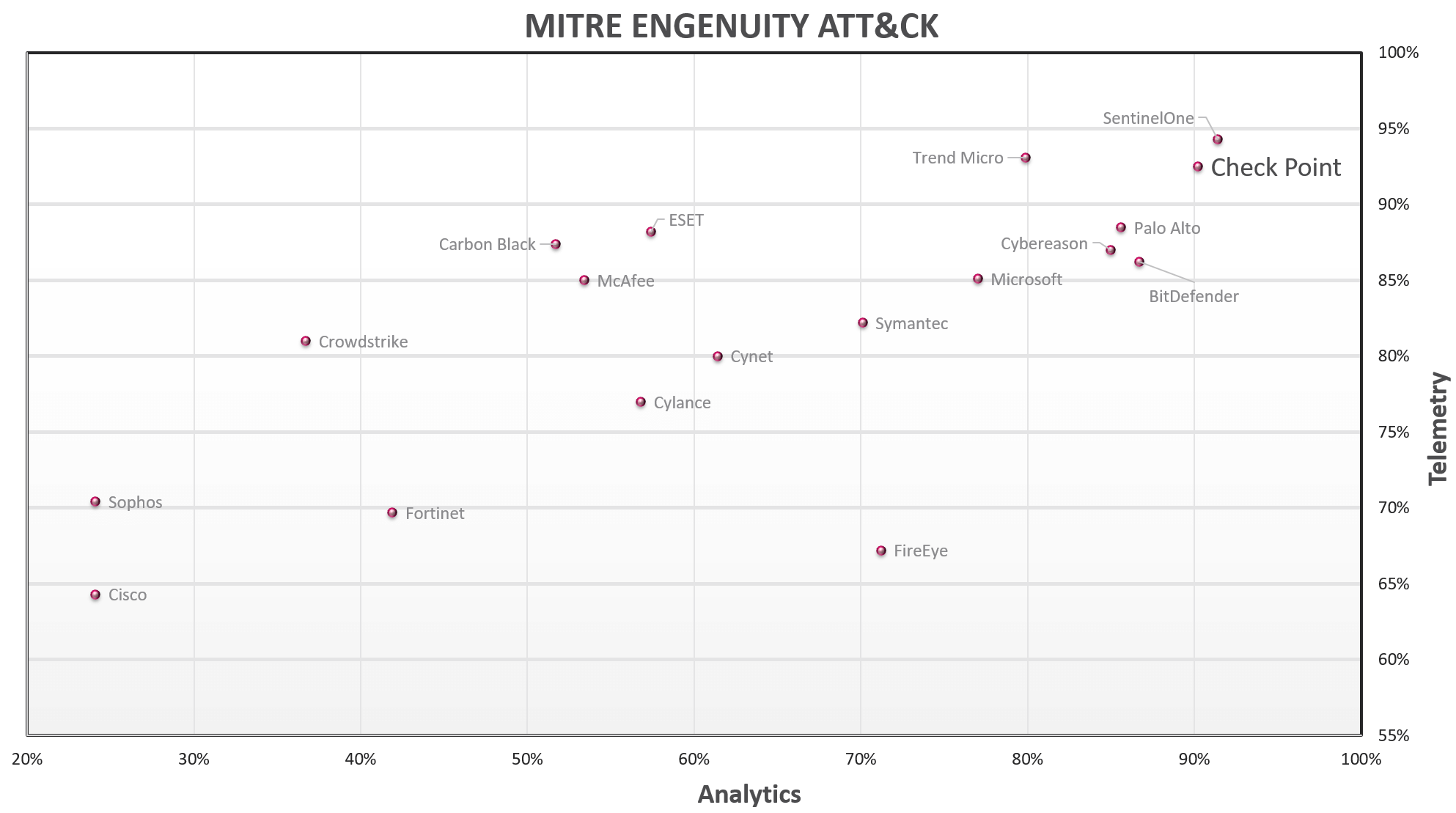
MITRE Engenuity ATT&CK® Evaluation 2021 results’ analysis. Source: Check Point Software. This is not an official MITRE Engenuity chart
These results highlight Check Point Harmony Endpoint’s ability to provide highest level of detection accuracy and contextualized visibility into real-world cyber threats, all while providing autonomous detection and response capabilities. So customers can rest assured knowing Check Point Harmony Endpoint will immediately and automatically block, remediate and recover from ransomware and other attacks before damage spreads. At the same time, their security teams can use the solution to accurately detect threats, investigate and respond to them effectively leveraging the industry’s most comprehensive correlation with the MITRE Engenuity ATT&CK® framework.
Join a live webinar with our security experts on May 5th to better understand the evaluation results and how they can help you strengthen your endpoint security strategy.
Register today: Americas, EMEA/APAC
Each year, MITRE Engenuity conducts independent evaluations of cybersecurity products to help the industry and government institutions make better decisions to combat security threats and improve their threat detection capabilities. The MITRE ATT&CK® knowledge base helps security operations understand attackers and their techniques, which creates the basis to a strong detection and response strategy, and eventually for a better security posture. The MITRE ATT&CK® framework is the most extensive knowledge base of adversary tactics and techniques based on real-world observations.
MITRE Engenuity ATT&CK® Evaluations test various vendors on their ability to automatically detect and respond to real-life cyberattacks within the context of the ATT&CK framework.
In this year’s test, MITRE Engenuity used the MITRE ATT&CK® knowledge base to emulate the tactics and techniques of Carbanak and FIN7. These two threat groups have been using sophisticated malware and tactics to launch attacks against financial services and hospitality organizations over the past five years, resulting in the theft of more than $1 billion across hundreds of businesses.
“MITRE Engenuity ATT&CK® Evaluations play a crucial role in the war against cybercrime. By evaluating cybersecurity solutions’ ability to defend against real-world cyberattacks and threat groups, the team at MITRE Engenuity raises the industry’s cyber protection standard,” said Neatsun Ziv, Vice President of Threat Prevention at Check Point Software Technologies. “With the massive shift to remote working model and the fast-evolving threat landscape, it has become critical for businesses worldwide to strengthen their endpoint security strategy. The latest ATT&CK® Evaluations results underscore Check Point Harmony Endpoint’s industry-leading threat detection and full attack visibility capabilities. Customers get all the endpoint protection they need against all imminent threats like ransomware, malware, phishing while enjoying robust detection and response capabilities at the best TCO”.
“MITRE’s evaluations empower the security community to make more informed decisions through a transparent evaluation process and we’re glad that Check Point Software participated in this important test, along with multiple other vendors,” said Frank Duff, MITRE ATT&CK Evaluations Lead. “Using the MITRE ATT&CK framework as the benchmark and our publicly available results, users can explore how Harmony Endpoint detected our emulated adversary behavior of Carbanak and FIN7. Working together, these evaluations can make cyberspace safer for everyone.”
This year’s MITRE Engenuity ATT&CK® evaluation results underscored Check Point Harmony Endpoint‘s top-class visibility and threat detection capabilities.
- Check Point Harmony Endpoint successfully detected 100% of unique techniques used during the test
- For 96% of these unique techniques, Check Point Harmony Endpoint had the highest technique detection level.
- Check Point Harmony Endpoint achieved a leading result among all participants in analytics detection (which includes context and mapping to the relevant technique instead of raw telemetry).
- During the ATT&CK® Evaluations testing, Check Point Harmony Endpoint proved its ability to provide full context and end-to-end threat visibility to detect threats and act quickly, reducing the attack surface.
Here’s the ATT&CK® Evaluations team’s summary of how Check Point’s Harmony Endpoint performed:
“Alerting Strategy: Indicators that are deemed to be related to a compromise are assigned severity values (Low, Medium, High, Critical). These compromise-related indicators are also enriched with contextual information, such as mappings to related ATT&CK Tactics and Techniques. Alerted events are aggregated into specific views as well as highlighted (icons, colors) when included as parts of other views of system events/data.
Correlation Strategy: The Forensics view captures correlation between system events and data, such as process lineage or interactions between processes and files. The Forensics view focuses on a single host, but dashboards exist to provide a wider perspective on events across multiple hosts. Process trees are generated that enable visualizations of process lineage, detections, and context for each of the processes within the tree.”
The results of this ATT&CK® Evaluations round once again emphasize Check Point Harmony Endpoint’s top-class threat detection capabilities, just recently confirmed by the solution’s “Top Product” recognition by AV-TEST.
To learn more about Check Point’s Harmony Endpoint performance in this latest round of testing and review the full results, please visit MITRE Engenuity’s blog and testing overview.
Join a live webinar with our security experts on May 5th to better understand the evaluation results and how they can help you strengthen your endpoint security strategy.
Register today: Americas, EMEA/APAC
How Check Point Harmony Endpoint integrates with MITRE ATT&CK® framework
Check Point Harmony Endpoint’s threat hunting is a powerful tool that helps hunt and investigate incidents promptly. It includes pre-defined queries that allow you to quickly find active attacks, detected attacks, malicious files and more.
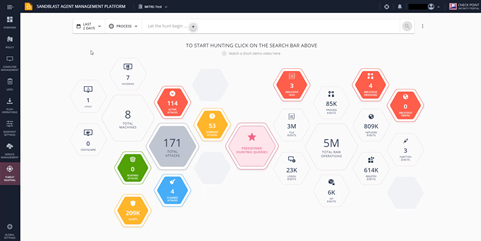
Figure 1. Threat Hunting Overview Screen
Check Point Harmony Endpoint boosts your endpoint security by proactively hunting for MITRE ATT&CK® techniques using its enhanced threat hunting capabilities. The solution provides a MITRE ATT&CK® dashboard that helps investigate attacks based on MITRE ATT&CK’s knowledge base.
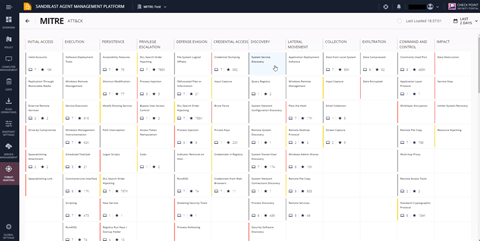
Figure 2. Check Point Harmony Endpoint’s MITRE ATT&CK® Live Dashboard
Take a few moments to watch this short video that describes how you can hunt for real-life threats using the Check Point Harmony Endpoint’s MITRE ATT&CK® Threat Hunting Dashboard
Discover all the capabilities of Check Point Harmony Endpoint by yourself, and schedule a personalized demo to see it in action.
Join a live webinar with our security experts on May 5th to better understand the evaluation results and how they can help you strengthen your endpoint security strategy.
Register today: Americas, EMEA/APAC









